
The Problem With Backdoors
Government-imposed backdoors make security much worse, not better
Federal law enforcement leaders in the U.S. and
U.K. argue that growing use of encryption will cause them
to lose their investigative capabilities.
Their apocalyptic talk of terrorist communication "going dark"
frightens politicians who know nothing about
information technology.
The failed "Crypto Wars" of the 1990s are back.
That was when the U.S. Government wanted everyone to use
the Clipper chip, which would provide backdoor access to
all encrypted communication and storage.
The Clipper chip failed, but we did get the nonsense of
"export grade" cryptography.
That was a system by which, if the U.S. didn't tell
foreigners how to do math, they would never figure
it out themselves.
Right...
Then in 1998 two Belgian cryptographers,
Joan Daemen and Vincent Rijmen, submitted their
Rijndael cipher to U.S. NIST and it came to be accepted
as the U.S. Advanced Encryption Standard or AES.
Oops. Daemen went on to be part of the team that
developed the Keccack cryptographic suite, part of which was
formally accepted as SHA-3
in August 2015.
Government-imposed backdoors
cause huge problems.
Some individual or group of the supposed good guys can
abuse the backdoor for personal or political gain.
Or other people can use the backdoor, perhaps the
very adversaries the backdoors were installed to fight.
Or third parties can steal the collected data, revealing
secrets of the surveillance target, the government,
or both.
And sometimes two or more of those problems
are caused by a single backdoor.
2015–2016 saw a one-year period with three
major SSL/TLS security problems caused by those government
imposed weaknesses of the 1990s.
In 1992 the FBI's Advanced Telephony Unit warned that within three years their Title III wiretaps would fail to help them fight crime and terrorism. At best only 60% would still be intelligible, and quite likely all would become useless. But the reality has been that law enforcement has enjoyed ever increasing surveillance capabilities since then.
Current best practices include forward secrecy and authenticated encryption. Backdoors would interfere with both of these, forcing significant steps backward and re-enabling a variety of cyber-crimes that these security mechanisms can prevent.
Backdoors require significantly increased system complexity, leading to more vulnerabilities and increased difficulty in finding those vulnerabilities. As a former Director of Research at NSA said, "Complexity is the enemy of security."
Backdoors collect sensitive information of great interest to attackers. The existence of backdoors attracts more attacks from outsiders and invites more abuse by insiders.
Wall Street
Bombing
The problem of insider abuse goes back to before the Internet, to an era when letters and telegrams were the dominant forms of communication. During the wave of anarchist bombings of the early 1900s, including the Wall Street bombing of 1920, J. Edgar Hoover moved from being head of the Justice Department's Alien Enemy Bureau to being the head of its new General Intelligence Division. Mail was opened, telegrams were copied, and telephone lines were tapped. Hoover was appointed director of the Bureau of Investigation, later to become the FBI, in 1924. He quickly became entrenched, exceeding the FBI's jurisdiction and building dossiers he could use for political leverage. Harry Truman said that Hoover had transformed the FBI into a private secret police force, and "we want no Gestapo or secret police. The FBI is tending in that direction. They are dabbling in sex-life scandals and plain blackmail. J. Edgar Hoover would give his right eye to take over, and all congressmen and senators are afraid of him".
Michael Hayden, formerly the head of both the NSA and CIA, was interviewed in February 2016 about the FBI's demand that Apple enable backdoors. Hayden was against the backdoors:
You just watched Apple attorney Ted Olson defend the
protection of customer data. Where do you stand?
My position is that with the FBI and others demanding that
Apple universally enable backdoors in their devices to break
otherwise unbreakable encryption, I actually side with Apple.
On the grounds of security and safety, I think that's the
best choice.
American security and safety, in this current
cyber era, is better served with end-to-end
unbreakable encryption.
In late 2017 and early 2018, U.S. Government officials were demanding the same dangerous weaknesses. They were now calling their unreasonable demand "Responsible Encryption", trying to make the point that it would be unreasonable for industry not to add the security holes they want.
On with the examples of how government-imposed backdoors so often go wrong:
Blackmail, bribes, and extortion: Telecom Italia
Over the period 1996–2006 Telecom Italia suffered an insider attack. Over six thousand people were the targets of unauthorized wiretaps apparently operated by authorized Telecom Italia employees gone rogue. Dossiers were collected on politicians, judges, bankers, business executives, and others. The dossiers were sold through a private investigation agency in Florence, and used for blackmail and extortion. It is believed that no large business or political deal during this period was truly private. See this La Repubblica article, this Der Spiegel article, and the February 17 2001 testimony by Susan Landau to the Judiciary Committee of the U.S. House of Representatives, "Going Dark: Lawful Electronic Surveillance in the Face of New Technologies." By late 2015 the wiretapping and extortion was believed to have been carried out under the direction of a high-ranking official at SISMI, the Italian military intelligence agency, according to an editorial for the Association for Computing Machinery by Meredith Whittaker and Ben Laurie.
Politically motivated abuse: Vodaphone Greece
In the mid-2000s, Vodaphone Greece had purchased Ericsson telephone switches designed to allow lawful interception. A switch software update automatically added the wiretapping capability without adding a user interface to easily use or audit the use of that capability. Intruders modified the switch software to initiate eavesdropping and enable further software updates. The telephone activity of over one hundred senior officials of the Greek government was monitored and recorded for a period of ten months in 2004–2005. Targets included the Prime Minister, the head of the Ministry of National Defense, and the head of the Ministry of Justice. There is an in-depth story at IEEE Spectrum, a post-Snowden in-depth story in The Intercept by James Bamford (2015), a short overview on Wikipedia with links to background material, a 2007 story at The Register, and a manual for Ericsson's Interception Management System explaining how some of the system worked.
Backdoors may break existing functionality
An "update" for BlackBerry-using customers of Etisalat in the United Arab Emirates actually installed spyware developed by American firm SS8. The spyware sent received messages back to a central server. It was noticed because Etisalat users had a sudden epidemic of crashes, poor reception, and reduced battery life, and some handsets completely stopped working.
If this spyware was intended to help catch terrorists, it did an awfully sloppy job.
Misuse by trusted insiders: Police abuse of records
An Ars Technica article reported: "Denver police officers performed searches on state and federal criminal justice databases that were not work-related and instead were made to help officers' in the romance department and to assist friends, according to an independent department monitor. The report said that punishment, usually a written reprimand instead of being charged criminally, is not enough to deter future abuse of the National Crime information Center (NCIC) and the Colorado Crime Information Center (CCIC) databases." The report by the Denver Office of the Independent Monitor said, ""When used appropriately, they can be powerful tools to investigate crime," the report stated. "But the misuse of these databases for personal, non-law enforcement purposes may compromise public trust and result in harm to community members." And then there was the Minneapolis police office whose driver's license record was illegally accessed over 400 times by her fellow officers.
Potential for unseen misuse by trusted insiders: Cisco IP network architecture, and U.S. DOD phone switches
Tom Cross discovered in 2010 that a Cisco IP network architecture designed for law-enforcement interception could be exploited. His presentation "Exploiting Lawful Intercept to Wiretap the Internet" describes several vulnerabilities: two authentication weaknesses in the SNMPv3 protocol used to control the interception function, a lack of audit trails, susceptibility to packet spoofing, and the lack of a requirement for encryption.
In 2012 all the U.S. Department of Defense's phone switches were reported to be vulnerable due to the included wiretapping capabilities required by the CALEA or Communications Assistance for Law Enforcement Act regulations. This was reported in an editorial for the Association for Computing Machinery by Meredith Whittaker and Ben Laurie.
Other Cisco Backdoors
Cisco has had several, and they even wrote an IETF proposal for "Exploiting Lawful Intercept to Wiretap the Internet" in 2004. Someone showed in 2010 how to abuse this to take control of routers.
Then, 5 new backdoors in the first half of 2018:
Potential for widespread misuse by hackers: Volkswagon
Not a government decree, but it's a prominent error caused by a single secret backdoor: Volkswagon designed a wireless door locking system that has one static key value that can open about 100 million VW vehicles. See the stories in Techdirt and in Wired. The same researched had discovered another vulnerability in VW systems a few years before, one that allowed them to start the engine. In response, Volkswagon spent two years suing the researchers in an attempt to hide the flaw.
Exposure of government secrets, and the secrets of its targets: Indian government and RINOA
In 2012 the Indian hacker group "The Lords of Dharmaraja" posted documents they had downloaded from an Indian military network showing that India's military intelligence and Central Bureau of Investigation had been collecting telecommunications traffic at least since April 2011. In exchange for access to the Indian market, manufacturers including RIM, Nokia and Apple (collectively defined as "RINOA" in the document) agreed to provide backdoor access to their devices. The Indian government then used those backdoors to intercept internal e-mails of the U.S.-China Economic and Security Review Commission, a U.S. body mandated with monitoring, investigating, and reporting to Congress on the trade relationship between the U.S. and china. The hackers posted those internal e-mails to Pastebin.
Rogue police action: Gujarat police
The Hindustan Times reported in May 2013 that the Gujarat police obtained call detail records of up to 93,000 mobile phones without the state police chief knowing anything about the operation.
Exposure of government and personal secrets: Chinese theft of Google and Microsoft data collection
The U.S. Government required Google to collect and hand over data on a large number of users. Chinese hackers stole the resulting database. It listed those people who the U.S. government had under surveillance as they were suspected of being Chinese agents. This was a big win for China, as it told them which of their agents were suspected, so they could destroy information and leave the country. It could at least suggest that unlisted agents hadn't come under suspicion, letting Chinese intelligence best utilize its human resources. Google had disclosed an intrusion by Chinese hackers in 2010, discussed here, but the U.S. Government prevented Google's disclosure of this database breach. Unnamed "current and former government officials" told the Washington Post about it for this 2013 story. Microsoft then said that Chinese hackers had targeted Microsoft servers around the same time, looking for similar information about Government-required data collection by Microsoft.
Exposure of user data: BlackBerry Password Keeper
It appears that BlackBerry's Password Keeper has either a backdoor or a stunningly bad design. Whichever it is, Elcomsoft's Phone Password Breaker or EPPB can immediately decrypt content without a need for brute-force attacks on a user-selected password. An escrow key is stored alongside the data in BlackBerry 10 backups.
EPPB is said to have been used to automatically discover iCloud passwords in prominent exploits, like the 2014 theft of nude photographs many celebrities had taken of themselves and stored in iCloud.
Other Gaping Holes in BlackBerry
Vice generated a lot of attention with articles here and here about how the Royal Canadian Mounted Police has had a global encryption key for Blackberry devices since 2010. As The Register explained, this wasn't a new story, and the RCMP had announced how they did this for their Clemenze Project against Italian-based organized crime in 2014.
Exposure of government secrets and abuse by third parties: Dual_EC_DRBG and multiple Juniper backdoors
In 1997 the paper "The Prevalence of Kleptographic Attacks on Discrete-Log Based Cryptosystems" introduced the "discrete log kleptogram" concept. In 2005 two Certicom employees working on the ANSI X9.82 standardization committee filed for a U.S. patent, it was issued in 2007 as US20070189527 A1 "Elliptic curve random number generation." It describes a backdoor in an elliptic curve random number generator function, and ways to neutralize such a hidden backdoor by choosing alternative curve points and more bit truncation in the output function.
The NSA got NIST to standardize the Dual_EC_DRBG algorithm in 2007. Members of the ANSI standardization committee to which the algorithm was submitted were aware of the potential backdoor and how to disable it (see that patent and the Crypto 2007 discussion), but they did not unconditionally disable it or widely publicize the issue.
Background of theDual_EC_DRBG
backdoor
The algorithm apparently had such a backdoor that could be used for Internet traffic surveillance, as reported in multiple New York Times stories (details below). This was part of a reported $250 million per year spent by NSA to insert backdoors in software and hardware as part of BULLRUN, a program described as existing "to covertly introduce weaknesses into the encryption standards followed by hardware and software developers around the world."

Juniperus chinensis 'Mountbatten' or Mountbatten Chinese Juniper, a member of Cupressaceae or the Cypress family.
Reuters reported in 2013 that NSA had secretly paid RSA Security $10 million to make the flawed algorithm the default in their RSA BSAFE cryptography software library.
Dual EC: A Standardized Back DoorIn January 2015 Matthew Green wrote a very nice history of the algorithm's subversion, at least as far as it was known then.
ScreenOS runs on Netscreen devices. Juniper bought Netscreen in 2004, eight years before the backdoors appeared.
Then, in December 2015, Juniper Networks announced that some versions of their ScreenOS firmware, one of their router operating systems, had two major security problems.
There was a backdoor for remote administrative access, and the flawed Dual_EC_DRBG cryptographic algorithm was used (CVE-2015-7755 and CVE-2015-7756, respectively). It's interesting to see that there was an article on firmware Trojans in Juniper ScreenOS firmware in Phrack in 2009.
The remote access backdoor used a
hard-coded password
embedded in the ScreenOS firmware.
Connect via either Telnet or SSH, provide any user name
and the string
"<<< %s(un='%s') = %u"
as the password, and you have full
access to the device.
Juniper bug
The flawed cryptographic algorithm in Juniper's words "may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic" (details below).
The cryptographic backdoor is speculated to have been further modified and used by attackers hostile to the NSA's mission, based on analysis and discussion by Ralf-Philipp Weinmann, Steve Checkoway, Willem Pinckaers, H.D. Moore, and Matthew Green (with some of the reverse-engineering details here), and as reported in Wired.
The Juniper backdoors were described in a presentation at the Real World Cryptography Conference 2016, by Wired, by Ars Technica, and by The Register here and here. That Wired article observed, "Even if the NSA did not plant the backdoor in the company's source code, the spy agency may in fact be indirectly responsible for it by having created weaknesses the attackers exploited."
Then in April 2016, the report "A Systematic Analysis of the Juniper Dual EC Incident" came out, written by Stephen Checkoway, Shaanan Cohney, Christina Garman, Matthew Green, Nadia Heninger, Jacob Maskiewicz, Eric Rescorla, Hovav Shacham, and Ralf-Philipp Weinmann. They analyzed the randomness subsystem and its interaction with the IKE protocol used for VPN key establishment. They identified a cluster of other changes introduced in 2008. Then they demonstrate how they can decrypt an IKE handshake and its associated IPsec VPN traffic in isolation without observing any other network traffic. It was followed by Where Did I Leave My Keys?: Lessons from the Juniper Dual EC Incident in November 2018.
A 2021 Bloomberg report provided more details. Juniper engineers knew that there was a vulnerability. But the U.S. Department of Defense insisted that Juniper include the flawed algorithm. Meanwhile the APT 5 hacking group tied to the Chinese government had hijacked the NSA algorithm back in 2012, and had added a separate backdoor in 2014.
The ScreenOS timeline was:
| 27 Oct 2006 |
Introduced Dual_EC_DRBG Introduced bug in RNG code Lengthened IKE nonces to leak enough information for key recovery |
| 12 Sep 2012 | Replaced ECC values with suspect Q point |
| 25 Apr 2014 | Added SSH backdoor |
| 17 Dec 2015 |
Vulnerability announced SSH backdoor removed Trusted ECC Q point restored |
| April 2016 |
Deprecated RNG replaced with HMAC DRBG
specified in NIST 800-90A Improvements in entropy collection See ScreenOS 6.3.0r22 release notes |

Juniperus chinensis 'Mountbatten' or Mountbatten Chinese Juniper.

Juniperus x pfitzeriana or Pfitzer Juniper.
In late 2017 Matthew Green reported about an apparent TLS bug in older Canon printers. It confirmed the theory that RSA's BSAFE TLS library included a feature called "Extended Random", which makes it easier to exploit the Dual EC backdoor and decrypt TLS connections. Commercial versions of RSA BSAFE deployed the Extended Random extension and made it active in third-party commercial products.
Entrenching the use of insecure designs:
The so-called DROWN vulnerability of SSL/TLS came out in 2016. As analysts point out, this was the third major Internet security problem in one year caused by late 1990s U.S. government policies restricting the export of strong cryptography.
Those policies were relaxed in the mid 2000s but protocol specifications still include support for intentionally weakened cryptography. Most implementations still support the "export-grade" weakened algorithms, and many servers aren't configured to refuse to use the insecure versions.
The other two within the past year were the FREAK attack, for "Factoring RSA Export Keys", which targets deliberately weak RSA keys, and the Logjam attack, which targets deliberately weakened Diffie-Hellman key negotiation.
Driving users to alternative, possibly less secure, solutions:
Microsoft markets their Live@Edu system to schools, advertising that its lack of encryption is a "security" feature. The school administrators can monitor communication between teachers for an advantage in salary or other negotiations, and of course Microsoft has frightening suggestions about the likelihood of mass shootings if students' messages aren't monitored. At many of the school that moved to this or a similar all-cleartext e-mail system, almost all faculty and students quickly moved all their communication to Gmail or similar and left the school's system unused.
Governments keep pushing for more backdoors
The UK government was pushing the MIKEY-SAKKE secure voice protocol with built-in key escrow and other problems in 2016, after rejecting a more secure standard. Meanwhile, the U.S. FBI and some lawmakers were restarting the 1990 "crypto wars" with demands for sweeping backdoors and security degradation so they don't "go dark," mostly over a work phone of a workplace shooter who had deluded dreams of being an actual terrorist. We'll have to wait to see how these blow up.
In late 2020 stories emerged that it wasn't just Crypto AG,
but Omnisec AG was a second Swiss company selling
US-compromised cryptographic technology.
Republik.ch Nov 11 2020
SwissInfo.ch Nov 26 2020
Swiss Parliamentary investigation
Swiss Parliament's Report
Why do backdoors for government access always lead to security problems? See the paper Keys Under Doormats: Mandating insecurity by requiring government access to all data and communications by an all-star team of authors, many of them leaders in various areas of information security: Harold Abelson, Ross Anderson, Steven M. Bellovin, Josh Benaloh, Matt Blaze, Whitfield Diffie, John Gilmore, Matthew Green, Susan Landau, Peter G. Neumann, Ronald L. Rivest, Jeffrey I. Schiller, Bruce Schneier, Michael Specter, and Daniel J. Weitzner.
The NSO Group's Pegasus spyware isn't a backdoor built into a useful product. It's just straight-up malicious software which can be covertly installed on a mobile phone, collecting all stored information and turning the device into a surveillance device. It first went onto the market and began being used by oppressive governments in 2014. It was discovered in August 2016, reported on in August and December 2020, and analyzed in detail and reported on in July 2021.
If You Can't Get a Backdoor, Maybe Spyware?
Spyware is seen as malicious and wrong,
until the government wants to use it.
Predator, Pegasus, there are several choices.
Government spy scandal in Greece,
spyware in the service of politics
Greek intelligence services tapping and hacking phones
of investigative journalists and political rivals
Cellphones of Spain's Prime Minister and Defense
Minister breached by Pegasus
Cellphones of France's President and 15 Ministers
breached by Pegasus
Some governments Know Better
The Dutch government was against backdoors and was funding the OpenSSL project in 2015, see stories here, here, and here.
France rejected backdoors in cryptographic systems in 2015 as the concept was "vulnerability by design".
Background of the Dual_EC_DRBG Backdoor
HowElliptic-Curve Cryptography Works
Elliptic curve cryptography is based on the set of points satisfying the equation y2 = x3 + ax + b where x and y are elements of a finite field and a and b are parameters of the curve. A pseudorandom bit stream generator based on ECC, also known as a random number generator, or a deterministic random bit generator in NIST parlance, applies mathematical functions to (x,y) points on the elliptic curve to generate new points and then select just some of their bits. Two points P and Q, on that elliptic curve are used in the process, which is fed an initial seed which functions as the key. That process should generate a bit stream that is statistically indistinguishable from truly random data. Below is a diagram from NIST SP 800-90A:
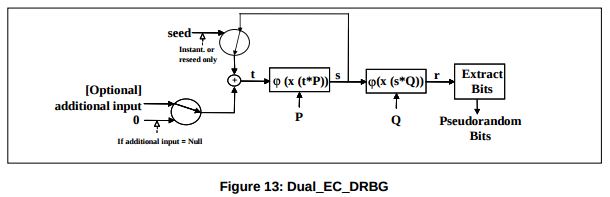
If the generator outputs too many bits per point, an attacker can start to predict following bits. Dual_EC_DRBG only discards the first 16 bits of the x coordinate and outputs the rest, meaning that you can do a brute-force search through the 216 = 65,526 possible values of x, solving for the corresponding y through simple algebra.
It gets worse: the internal state uses those two elliptic curve points, P and Q, which should be random. If there were a mathematical relationship between them, then anyone who knew that relationship and could observe just 32 bytes of output could derive the internal state including t and s and predict all the following output. From NIST SP 800-90A, pages 77-79, the curves are specified as y2 = x3 + 3x + b (mod p) where a = 3 and, with the order of the field p and order of the elliptic curve group n in decimal, the rest in hexadecimal:
Curve P-256 p = 115792089210356248762697446949407573530086143415290314195533631308867097853951 n = 115792089210356248762697446949407573529996955224135760342422259061068512044369 b = 5ac635d8 aa3a93e7 b3ebbd55 769886bc 651d06b0 cc53b0f6 3bce3c3e 27d2604b Px = 6b17d1f2 e12c4247 f8bce6e5 63a440f2 77037d81 2deb33a0 f4a13945 d898c296 Py = 4fe342e2 fe1a7f9b 8ee7eb4a 7c0f9e16 2bce3357 6b315ece cbb64068 37bf51f5 Qx = c97445f4 5cdef9f0 d3e05e1e 585fc297 235b82b5 be8ff3ef ca67c598 52018192 Qy = b28ef557 ba31dfcb dd21ac46 e2a91e3c 304f44cb 87058ada 2cb81515 1e610046 Curve P-384 p = 39402006196394479212279040100143613805079739270465446667948293404245721771496870329047266088258938001861606973112319 n = 39402006196394479212279040100143613805079739270465446667946905279627659399113263569398956308152294913554433653942643 b = b3312fa7 e23ee7e4 988e056b e3f82d19 181d9c6e fe814112 0314088f 5013875a c656398d 8a2ed19d 2a85c8ed d3ec2aef Px = aa87ca22 be8b0537 8eb1c71e f320ad74 6e1d3b62 8ba79b98 59f741e0 82542a38 5502f25d bf55296c 3a545e38 72760ab7 Py = 3617de4a 96262c6f 5d9e98bf 9292dc29 f8f41dbd 289a147c e9da3113 b5f0b8c0 0a60b1ce 1d7e819d 7a431d7c 90ea0e5f Qx = 8e722de3 125bddb0 5580164b fe20b8b4 32216a62 926c5750 2ceede31 c47816ed d1e89769 124179d0 b6951064 28815065 Qy = 023b1660 dd701d08 39fd45ee c36f9ee7 b32e13b3 15dc0261 0aa1b636 e346df67 1f790f84 c5e09b05 674dbb7e 45c803dd Curve P-521 p = 6864797660130609714981900799081393217269435300143305409394463459185543183397656052122559640661454554977296311391480858037121987999716643812574028291115057151 n = 6864797660130609714981900799081393217269435300143305409394463459185543183397655394245057746333217197532963996371363321113864768612440380340372808892707005449 b = 051953eb 9618e1c9 a1f929a2 1a0b6854 0eea2da7 25b99b31 5f3b8b48 9918ef10 9e156193 951ec7e9 37b1652c 0bd3bb1b f073573d f883d2c3 4f1ef451 fd46b503 f00 Px = c6858e06 b70404e9 cd9e3ecb 662395b4 429c6481 39053fb5 21f828af 606b4d3d baa14b5e 77efe759 28fe1dc1 27a2ffa8 de3348b3 c1856a42 9bf97e7e 31c2e5bd 66 Py = 11839296 a789a3bc 0045c8a5 fb42c7d1 bd998f54 449579b4 46817afb d17273e6 62c97ee7 2995ef42 640c550b 9013fad0 761353c7 086a272c 24088be9 4769fd16 650 Qx = 1b9fa3e5 18d683c6 b6576369 4ac8efba ec6fab44 f2276171 a4272650 7dd08add 4c3b3f4c 1ebc5b12 22ddba07 7f722943 b24c3edf a0f85fe2 4d0c8c01 591f0be6 f63 Qy = 1f3bdba5 85295d9a 1110d1df 1f9430ef 8442c501 8976ff34 37ef91b8 1dc0b813 2c8d5c39 c32d0e00 4a3092b7 d327c0e7 a4d26d2c 7b69b58f 90666529 11e45777 9de
The algorithm apparently had a backdoor, the P and Q parameters in the NIST are suspected of being related (although it remains a mystery as to just how to practically generate a related pair of points). Suspect P and Q values were also part of the Juniper backdoors.
Another Potential Backdoor
In the article "A kilobit hidden SNFS discrete logarithm computation" researchers showed how a specially chosen prime looks randomly chosen and safe, but provides a practical attack. The Wired article "NSA could put undetectable 'trapdoors' in millions of crypto keys" provides an overview.
Background of the Juniper Bug
Let's look at the code decompiled by Steve Checkoway:
void prng_generate()
{
int index;
unsigned int bytes_generated;
int v2;
int v3;
char v4;
int time[2];
time[0] = 0;
time[1] = get_cycles();
prng_output_index = 0;
++blocks_generated_since_reseed;
if ( !do_not_need_to_reseed() )
prng_reseed();
for ( ; (unsigned int)prng_output_index <= 0x1F; prng_output_index += 8 )
{
memcpy(prev_prng_seed, prng_seed, 8);
memcpy(prev_prng_block, prng_block, 8);
ANSI_X9_31_generate_block(time, prng_seed, prng_key, prng_block);
if ( sub_561A30(0) && (!memcmp(prng_seed, prev_prng_seed, 8) || !memcmp(prng_block, prev_prng_block, 8)) )
{
v3 = sub_92D6F0();
sub_39E2C0(0, 6, v3, "FIPS ERROR: PRNG failure, duplicate random output\n", SLOBYTE(time[0]));
sub_65EDD0(67375118, v4);
error_handler("FIPS ERROR: PRNG failure, duplicate random output\n", 11);
}
index = prng_output_index;
bytes_generated = 0;
if ( prng_output_index )
{
do
{
if ( !memcmp(&prng_output_buffer[bytes_generated], prng_block, 8) )
{
v2 = sub_92D6F0();
sub_39E2C0(0, 6, v2, "FIPS ERROR: PRNG failure, duplicate random output\n", SLOBYTE(time[0]));
error_handler("FIPS ERROR: PRNG failure, duplicate random output\n", 11);
}
index = prng_output_index;
bytes_generated += 8;
}
while ( prng_output_index > bytes_generated );
}
memcpy(&prng_output_buffer[index], prng_block, 8);
}
}
The assumption is that the Dual_EC_DRBG output may be
weak, but it serves as input or seed to the
stronger ANSI X9.31 random number generator within that
for loop.
But...
Look for the places where the global variable
prng_output_index appears
within this prng_generate() function.
We see the variable prng_output_index set to zero.
Then it is used to index through that for loop
for what we expect to be four iterations.
The loop terminates when prng_output_index
exceeds 0x1F (31 in base 10), and 8 is added to
prng_output_index at the end of each
pass through the loop.
Four iterations: 0, 8, 16, 24.
But...
The prng_reseed() function
fills a buffer with raw Dual_EC_DRBG output.
What we don't see in this code block is that
prng_reseed() also sets
prng_output_index to 32.
The for loop fails its test immediately, its
contained code shown in red italics never executes,
so the call to prng_reseed()
is the last thing that happens
within prng_generate().
The relatively strong ANSI_X9_31_generate_block()
function is never called and all we get is
Dual_EC_DRBG output.
Some Backdoors Are Government Trojan Horses
Does it qualify as a backdoor if it's actually more of a Trojan Horse operated by the government?
The U.S. FBI and the Australian Federal Police owned and
operated a commercial encrypted phone app called
AN0M for three years.
They tricked organized crime groups around the world into
using it, and the FBI and AFP could read everything.
I suppose that from the criminals' point of view,
this was a supply chain exploit.
There were several media stories on this:
The New York Times
Australian Broadcasting Company
The Sydney Morning Herald
The Washington Post
The Guardian