Hardware and Firmware Vulnerabilities and Exploits
Attacking the Platform
These are attacks on computer systems and networks based on exploiting hardware design or manufacturing bugs, or "not playing by the rules" in dealing with the hardware. The idea of violating the "rules" by freezing the semiconductors or overwriting Ethernet firmware data seems analogous to the very common software vulnerabilities caused by not fully validating user input. Well, maybe not just analogous, maybe we should consider frigid liquids or Firewire signals or Ethernet signals as user-supplied input just like packet contents or form data submitted to web servers.
What makes these different is that we don't generally have control of the hardware design and manufacturing. Yes, you could choose to buy an Ethernet card or CPU or motherboard from a different manufacturer, but you have to choose from the existing market.
What if you can't trust the
semiconductor manufacturer?
Then you can't trust anything!
The paper "Stealthy Dopant-Level Hardware Trojans:
Extended Version" in the
Journal of Cryptographic Engineering
looked at undetectable backdoors built into chips.
Journal of Cryptographic Engineering link (paywall)
Paper provided by authors
While there are some interesting open-source hardware projects, they are the exception and do not generally provide the features and performance needed. Enthusiasts must not forget that corporations and government agencies require well-known and trusted hardware manufacturers.
Speculative Execution CPU Design Flaws
In early January 2018 we learned that effectively all Intel CPUs and many AMD and ARM CPUs since 1995 have hardware design flaws. They do not really enforce isolation between user applications and the operating system. The kernel memory leak flaw allows a user process to read memory pages of other processes and of the kernel itself. This can expose cryptographic keys and other sensitive data.
When a CPU reaches a conditional branch in the code, something
like if (condition) ...,
it tries to predict which branch will be taken before
the decision is known.
If its prediction was correct, it will have already executed
a block of code before the decision is known.
If not, execution rolls back and
follows the correct branch instead.
Modern processors are good at this "speculative execution" because they store details about previous branch decisions in the BHB or Branch History Buffer.
While this often leads to the correct decision, the conditional statement may be security-critical. The roll-back at incorrect predictions doesn't include cache and the Branch History Buffer. That's because the speculative execution is done for performance reasons, and rolling back cache and BHB would hurt performance.
However, speculative execution, by its very nature, is not controllable and possibly dangerous.
Finding a CPU Design Bug in the Xbox 360
See the great
article
on the discovery of a hardware design bug in the Xbox 360
CPU, a three-core PowerPC processor made by IBM.
It had the usual dcbt instruction for
memory pre-fetch.
But because it was a video game console processor and
performance was therefore all-important,
an xdcbt or extended prefetch
instruction was added.
They found that calls to xdcbt were
corrupting memory.
So, they started compiling the code so as to not use
that instruction.
However, the crashes continued.
They eventually figured out that the branch predictor
would sometimes speculatively execute the
xdcbt instruction.
If it appeared anywhere in the application code,
only where it was used in an extra-cautious way,
it might be speculatively executed where it shouldn't,
corrupting memory.
The author of that piece mentions that the DEC Alpha processor had a similar problem.
Fixing a design flaw requires redesigning the system. People have looked at this, see this paper for a discussion of designing a new instruction-set architecture that would be immune to Spectre and similar attacks while still being almost as fast as a CPU using what we now recognize to be dangerous speculative execution.
Speculative execution vulnerabilities aren't restricted
to the x86 architecture.
The ARM-based M1 CPU used in Macs is susceptible to
the "PACMAN" flaw.
An attacker can bypass the ARM Pointer Authentication
which is intended to defend against pointer corruption attacks.
MIT paper on the flaw
doi: 10.1145/3470496.3527429
The Register
Macworld
Apple on arm64e pointer authentication
Kernel Page Table CPU Design Flaws
These mechanisms are abused in the "Spectre" and "Meltdown" attacks on speculative execution.
Meltdown and Spectre attacks on 1995-2017 Intel, AMD, and ARM CPUs Very early public report The Register initial report
The Spectre attack paper describes two exploits: (1) reading kernel memory from user space when running on bare metal, and (2) reading host kernel or hypervisor memory from kernel space on a VM.
The Meltdown attack paper describes an additional exploit, also reading kernel memory from user space when running on bare metal.
Other variants appeared in the following months.
See the research paper from researchers at
Princeton University and NVIDIA:
"MeltdownPrime and SpectrePrime:
Automatically-Synthesized Attacks Exploiting
Invalidation-Based Coherence Protocols"
Also see the paper by researchers at the College of William
and Mary, Carnegie Mellon University, University of
California Riverside, and Binghamton University:
"BranchScope: A New Side-Channel Attack
on Directional Branch Predictor"
Also see CVE-2018-3639, CVE-2018-3640, CVE-2018-3693,
TA18-141A,
updates from Oracle's Director of Security Assurance,
and a paper from MIT's Computer
Science and Artificial Intelligence Lab:
NVD: CVE-2018-3639
NVD: CVE-2018-3640
NVD: CVE-2018-3693
Alert TA18-141A:
Side-Channel Vulnerability Variants 3a and 4
Oracle's Eric Maurice on
CVE-2018-3640 ("Spectre v3a") and
CVE-2018-3639 ("Spectre v4")
Oracle's Eric Maurice on CVE-2018-3693 or Bounds Check Bypass Store
"Speculative Buffer Overflows: Attacks and Defenses"
The SWAPGS side-channel attack appeared in August, 2019.
US-CERT on SWAPGS Threatpost on SWAPGS Phoronix on SWAPGS mitigation impact
The post "x86 is a high-level language" from 2015 explains why these exploits are possible.
The 1995 paper "The Intel 80x86 Processor Architecture: Pitfalls for Secure Systems" listed, among other security flaws, "Prefetching may fetch otherwise inaccessible instructions in virtual 8086 mode."
RSB Speculative Execution Attacks
The RSB or Return Stack Buffer is another specific target in speculative execution attacks. In July 2018, researchers at University of California, Riverside announced what they called SpectreRSB, a "Spectre-class" attack on the RSB.
The attack allows modification of the return address pointer, and recovery of data from other processes running on the same CPU. It can expose data outside an SGX or Intel Software Guard eXtensions enclave.
Intel says that this is related to CVE-2017-5715, the Branch Target Injection vulnerability.
Side-Channel CPU Information Leakage
Hacking the Micro-Op Cache
Intel, AMD, and ARM processors translate complex instructions
into simpler internal micro-operations that are cached in
a dedicated on-chip structure called the
micro-op cache.
This paper describes exploiting it as a timing channel
to leak supposedly secret information.
I See Dead μops: Leaking Secrets
via Intel/AMD Micro-Op Caches
The Hertzbleed Attack
Power side-channel attacks on Intel and AMD x86 CPUs can be turned into timing attacks that can be done remotely through the Hertzbleed attack. As the paper's authors say:
In this paper, we show that on modern Intel (and AMD) x86 CPUs, power side-channel attacks can be turned into timing attacks that can be mounted without access to any power measurement interface. Our discovery is enabled by dynamic voltage and frequency scaling (DVFS). We find that, under certain circumstances, DVFS-induced variations in CPU frequency depend on the current power consumption (and hence, data) at the granularity of milliseconds. Making matters worse, these variations can be observed by a remote attacker, since frequency differences translate to wall time differences!
They have demonstrated a chosen-plaintext attack against
constant-time implementations of SIKE, a post-quantum
key encapsulation mechanism, allowing full key
extraction via remote timing.
Hertzbleed paper
Hertzbleed web site
Other CPU Design Flaws
Intel x86 Considered Harmful
Intel x86considered
harmful
The paper Intel x86 Considered Harmful is an excellent discussion of an architecture that is overly complex for what it provides. The complexity provides too many opportunities for vulnerabilities.
The paper has a great description of the firmware, the peripherals, networking, USB, graphics, disk and storage controllers, audio devices, video devices, and other potential points of attack and defense. Can these be audited? That isn't practical.
AMD Zen architecture CPU Bugs
In March 2018 CTS Labs announced what they called a "Severe Security Advisory" about vulnerabilities in AMD's Ryzen and EPYC product lines.
The describe the problems as four classes of attack. Given administrative-level privileges on the system, an attacker could plant malware that would persist not only through reboots but also reinstallations of the operating system.
Then only shared the information with AMD one day before releasing it, versus the typical disclosure window of at least a few months. And, their paper has very little technical detail. On top of that, their website contains a disclaimer that CTS Labs may have "an economic interest in the performance of the securities of the companies whose products are the subject of our reports."
The attacks, to the extent they're described, exploit vulnerabilities in AMD's Secure Processor and in a peripheral controller chipset sold by ASMedia. The debugging backdoors are built into the hardware, meaning they can't be fixed, only replaced.
Security Advisory Website CTS Labs whitepaper
Historical notes:
There were some interesting short articles about Intel Core 2 bugs, see here and here for the articles, and also see the background on Intel's quiet patch release. Affected CPUs were the Core 2 Duo E4000/E6000, Core 2 Quad Q6600, Core 2 Xtreme QX6800, QX6700, and QX6800.
Remember the Pentium CPU's that were bad at floating-point division?
For some Pentium CPU's, a block of machine code
starting 0xF00F will just plain halt it.
Intel x86 Processor Rosenbridge Backdoor
Christopher Domas demonstrated an x86 processor backdoor at the 2018 Black Hat USA and DEF CON meetings. It allows Ring 3 (user space) code to circumvent processor restrictions and read and write Ring 0 (kernel) memory. The backdoor is enabled by default on some processors.
This "Rosenbridge" backdoor is a small CPU core embedded alongside the main x86 core. It is controlled by one of over 1,300 undocumented model-specific registers (or MSRs) built into the processor. This secondary core has its own independent architecture, but shares parts of the instruction pipeline with the main core.
The vulnerable processors are used in various older
desktop, laptop, and embedded systems.
Researcher's explanation and code repository
Dark Reading story
Lazy FP State Restore CPU Bug (CVE-2018-3665)
This bug allows the floating point register content to be leaked from another process. Unfortunately, those registers are also used for cryptographic operations. The bug is present on Intel Core based microprocessors from the Sandy Bridge architecture up to the bug announcement of June 2018.
Register content can be saved and restored when switching from one process to another, but this takes time. This can be done "lazily" (that is, when needed) as a performance optimization.
This bug was fixed in the Linux kernel at release 4.9 (Dec 2016) by defaulting to "eager" (and safe) floating point restores on all x86-64 processors from around 2012 and later. Windows 10 and Server 2016 are believed to be safe, although Server 2008 needs a patch. Current OpenBSD and Drangonfly BSD are safe, and FreeBSD has a fix.
The FreeBSD kernel discussion (see the thread SSE in libthr shows how this type of problem arises. Someone finds a clever hack that improves performance by a few percent in a specific situation. That goes into place despite it not helping the majority of cases. Then someone finally notices that the change can be abused.
Red Hat back-ports fixes in the Linux kernel and applications. Especially with the kernel, the release number doesn't mean what you would assume it means. It would take a lot of work to figure out what all they have changed. RHEL 7 already had the fixes in place despite apparently having a kernel that describes itself as much older than 4.9.
NVD: CVE-2018-3665 Intel advisory INTEL-SA-00145 US-CERT alert ZDNet story
Other Design Flaws
Cisco Trust Anchor module and Thangrycat
ThangrycatCisco Trust Anchor module (or TAm) is a proprietary hardware security module used in a wide range of products, including enterprise routers, switches and firewalls. TAm is the root of trust that underpins all other Cisco security and trustworthy computing mechanisms.
The Thangrycat attack can make persistent modification to the Trust Anchor module through FPGA bitstream modification. This defeats the secure boot process and invalidates Cisco's chain of trust at its root.
While the flaws are in hardware, they can be exploited remotely.
Solid-State Drives Failing to Encrypt
Academic researchers published a draft paper reporting that
a wide range of solid-state drives fail to encrypt data
in any meaningful way.
Microsoft's BitLocker turns off software file system encryption
in the operating system if the drive claims to handle it.
So, many users who had enabled BitLocker had nothing but
a false sense of security.
Within a few days Microsoft had published a workaround
and US-CERT had issued a warning.
"Self-encrypting deception: weaknesses in the
encryption of solid state drives (SSDs)"
Microsoft: ADV180028 | Guidance for configuring
BitLocker to enforce software encryption
US-CERT: Self-Encrypting Solid-State Drive
Vulnerabilities
IPMI/BMC Weaknesses
IPMI or Intelligent Platform Management Interface is a protocol to communicate with a server via its BMC or baseboard management controller. The concept is called out-of-band management, and it's dangerously powerful. Serious security problems come from the Intel specification itself, how the protocol and BMC are implemented by the vendor, and how the customers use it.
For example, the IPMI standard requires passwords to be
stored in plaintext, or to be recoverable on demand.
If that isn't bad enough, vendors stuff in more attractively
powerful features that open further security holes.
See Dan Farmer's
IPMI page
for many details.
Dan Farmer's
IPMI page
IPMI was developed by Intel, Dell, HP, and others, server and firmware vendors add features and change the name: Dell calls their version iDRAC, HP iLO, IBM IMM, and so on. Brand names including:
- Integrated Lights Out Manager or ILOM (Oracle)
- Integrated Lights Out or iLO (HP)
- Integrated Dell Remote Access Card or iDRAC (Dell)
- Integrated Management Module or IMM2 (IBM)
- IMM (Lenovo)
- Integrated Remote Management Controller or iRMC (Fujitsu)
- SuperMicro Intelligent Management (SuperMicro)
You can monitor physical health and status (temperature, fan speeds, memory and disk errors, etc), and you can reboot the server, change firmware settings, attach optical media images, and thereby do a rescue boot or even install a new operating system.
An embedded server called the BMC or Baseboard Management Controller is installed on server motherboards. The BMC typically runs Linux on its own small CPU with memory and storage, and runs independently of the operating system or hypervisor you think of as being installed directly on the system. IPMI and the BMC provide networked access to the hardware even when the system is powered down.
The BMC controls the server at a very low level, mostly invisible to the operating system, and it can support HTTP/HTTPS and other application protocols. The BMC usually runs Linux on its own CPU, memory, and storage, and it operates even when the main power supply is turned off.
Papers and tools on IPMI security problems Bruce Schneier: "The Eavesdropping System in Your Computer" Internet Storm Center /SANS report: "IPMI: Hacking servers that are turned 'off'" Ars Technica: "'Bloodsucking leech' puts 100,000 servers at risk of potent attacks" USENIX report: "Illuminating the Security Issues Surrounding Lights-Out Server Management" Rapid7: "A Penetration Tester's Guide to IPMI and BMCs" ITworld: IPMI: The most dangerous protocol you've never heard of
There are several articles by Dan Farmer:
IPMI security
IPMI++ security best practices
"Sold Down the River"
on the state of IPMI vulnerability
exposures
"IPMI: Freight Train to Hell"
on flaws in IPMI and BMC
Intel has added something similiar to their Core processors
with Active Management Technology or
AMT, which gives you keyboard-video-mouse
remote access to a system regardless of the computer's state.
The default password is either admin
or P@ssw0rd
HowToGeek on AMT
Intel on AMT
Infineon Technologies TPMs Generating Weak RSA Keys
If the hardware won't even do what it's supposed to, there are big problems!
Infineon Technologies AG builds some secure hardware chips. They built their RSA library 1.02.013 into TPM chips starting in 2012. Unfortunately, that library and thus the chips generates RSA keys that can be factored in practical attacks. The vulnerable hardware had NIST FIPS 140-2 and CC EAL 5+ certification. The vulnerability was discovered in early 2017 and disclosed to the vendor, then announced 8 months later as CVE-2017-15361. Also see the research group's discovery report and their paper with the details.
The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli
They looked at the amount of CPU time required to factor the faulty keys, and converted that to US dollar cost on the Amazon AWS c4 computation platform.
A 512-bit RSA key would cost just $0.06 to break. 1024-bit RSA keys would cost $40-80, and 2048-bit keys $20,000-40,000.
The chips have been built into products sold by a wide range of vendors.
Two weeks later, Daniel J. Bernstein and Tanja Lange announced even faster attacks.
Ars Technica on initial announcement Estonia announces national ID card vulnerability Estonia disables 760,000 vulnerable ID cards Cybernetica Case Study: Solving the Estonian ID-card Case Infineon advisory Google advisory Microsoft advisory Faster attacks
Subverted Hardware and Firmware
If your hardware or firmware has been replaced or modified, there is no reason to expect it to behave as you would expect, or hope.
NSA ANT Attacks on Hardware
An article in Der Spiegel describes a 50-page internal "product catalog" from an NSA division called ANT, listing hardware and software (called "implants" in NSA terminology) which can penetrate systems to monitor, modify, and extract information. These include modified cables allowing "TAO personnel to see what is displayed on the targeted monitor", USB plugs and cables that covertly communicate over radio links (see the COTTONMOUTH device at right), replacement USB and Ethernet ports with covert data capture and communications built in, replacement chips and daughter cards to exploit the motherboard BIOS and using System Management Mode to reload itself at every boot, up to active GSM base stations that mimic legitimate mobile phone towers and therefore monitor and even control nearby mobile phones. ANT also attacks the firmware in disk drives manufactured by Western Digital, Seagate, Maxtor, and Samsung, and modifies hardware and/or firmware in Cisco, Juniper, and Huawei routers and firewalls. Cryptome has the full NSA ANT catalog available for download. A Wired article also discusses the catalog.
The router and firewall backdoors work by subverting the hardware's boot ROM, re-installing themselves every time the system starts and running below the operating system itself.
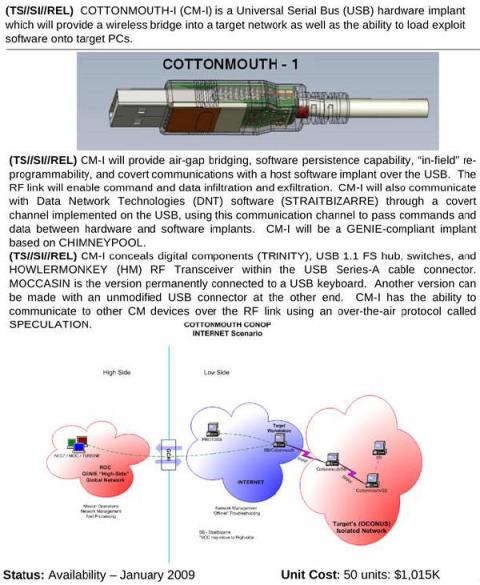
HEADWATER is a persistent backdoor software implant for selected Huawei routers. SCHOOLMONTANA, SIERRAMONTANA, and STUCCOMONTANA are persistent backdoor software implants for all modern versions of JUNOS, a version of FreeBSD customized by Juniper. They are for J-Series, M-Series, and T-Series routers, respectively.
FEEDTROUGH is a persistence technique for two software implants, BANANAGLEE and ZESTYLEAK, used against Juniper Netscreen firewalls. GOURMETTROUGH and SOUFFLETROUGH are used against other Juniper firewalls including the SSG 300 and SSG 500. JETPLOW is a similar product for Cisco PIX and ASA firewalls, HALLUXWATER is for Huawei Eudemon firewalls.
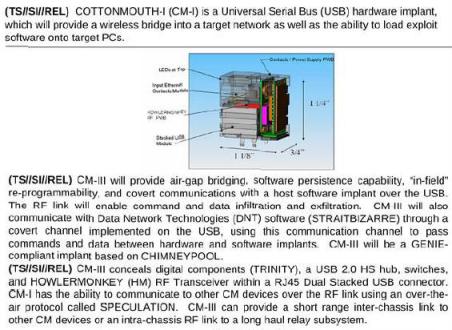
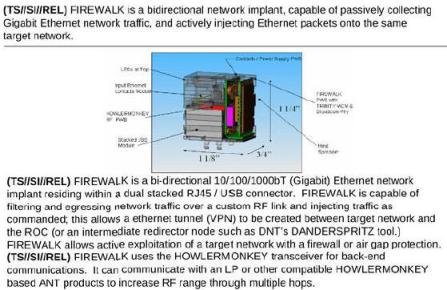

HOWLERMONKEY variants are RF transceivers to exfiltrate data from air-gapped systems. Other ANT products are miniaturized digital cores packaged in multi-chip-modules, basically miniaturized computers running full operating systems like the Raspberry Pi but concealed beneath a chip on the motherboard.
Chinese Implants? Supposedly
On 4 October 2018 Bloomberg Businessweek published The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies. The article quickly came under heavy criticism, with little effective support from Bloomberg.
The article said that Amazon and Apple had found in 2015 that motherboards from Supermicro, one of the leading suppliers, included "a tiny microchip, not much bigger than a grain of rice, that wasn’t part of the boards’ original design." This chip then sent data to servers China. Bloomberg cited "six current and former national security officials" backing up the story.
The article was accompanied by "artist's conception" artwork that many misinterpreted as actual photographs. Or, that Bloomberg wanted us to misterpret the artwork as photographs.
There is some obvious nonsense in the Bloomberg story. Their example of how it might work speculates about "the Linux operating system" and confuses the kernel, the operating system itself, with user-space programs that check user passwords. The article has been made friendly for non-technical readers, with "artist's conceptions" of what might have been. The result is that you don't know if they made the technical parts wrong to make them easier for non-technical readers, or if they're simply wrong to start with.
Amazon, Apple, and Supermicro published detailed rebuttals of the Bloomberg story. The National Cyber Security Centre, a unit of GCHQ, soon agreed with Apple and Amazon that Bloomberg was wrong. Officials from the U.S. Department of Homeland Security, the FBI, and the Office of the Director of National Intelligence either discounted the report's validity or said they had no knowledge of the attack as Bloomberg described it. The NSA issued public statements saying they were "befuddled" by Bloomberg's report.
Here is a piece from SecuringHardware.com, Do I Have a Hardware Implant? Here's a good summary from the Grugq.
See this excellent piece on counterfeit electronics (from 2011, when there had just been a scare about the U.S. DoD supply chain). It explains the many forms of counterfeit, remarked, refurbished, and simply re-used parts. You don't need elaborate sinister conspiracies to explain hardware mysteries.
Before long, The Atlantic had an article about how even if the story is wrong, at least we can learn a lesson about supply chain trust.
IEEE published an article about automated hardware inspection.
As several pointed out, Bloomberg has a track record of sensational but incorrect stories about hacking and cyberwar. The same reporters claimed in 2014 that the US government knew about the Heartbleed bug, and then refused to correct the story, follow up, or even comment.
Bloomberg published a sensational cyberwar story about a Turkish pipeline explosion in 2014 that technical experts and the intelligence community said was wrong, but Bloomberg never retracted it.
But then...
Bloomberg News published a
new story in February 2021
Now they said that 14 former law enforcement and intelligence
officials vouched for the story that China's exploitation
of Supermicro products "had been under federal
scrutiny for much of the past decade."
Bloomberg News Feb 2021 story
Bruce Schneier's overview
Atlantic Council report on the
insecure software supply chain
There were still significant oddities and clumsiness in the 2021 article. They quote someone as describing US military laptops that "had a chip encrypted on the motherboard." Clearly they should have said "embedded", why did Bloomberg either misquote them or not realize the need to add "[sic]" to the (mis)quote? Later they take pains to explain what BIOS is, when UEFI firmware almost completely replaced BIOS around 2010–2012. They offer as background support conversations they had with a former US Navy SEAL who co-founded a venture capital firm—maybe of interest to their readers but not a specialist in the fields of microelectronic manufacturing or cybersecurity.
Plus, they published their report just a month after a group of Qanon believers had stormed the US Capitol, at the end of four years in which an increasing number of people who believe the Qanon nonsense and other conspiracy theories were put into dangerously influential positions in the US Government. At that point, "recently retired US government officials" wasn't a terribly impressive or convincing source of background.
NSA said that it still stood by its comments about being "befuddled" by Bloomberg's 2018 report. Maybe that was the literal truth, maybe that was part of a cover story. Who knows?
Supply chain insecurity is a very important problem. I don't know how much this has to do with it.
Modify the main board firmware (BIOS, UEFI):
CVE-2017-5703
describes a vulnerability in Intel's SPI Flash memory,
a component of several Intel CPU series.
An attacker could use this vulnerability to block BIOS/UEFI
updates or selectively erase parts of the firmware.
CVE-2017-5703
INTEL-SA-00087 Security Advisory
There was concern back in 2006 about an ACPI/BIOS based attack.
The Rakshasa software collection can reflash firmware.
software collection Rakshasa can reflash firmware,
"Black Hat: Researcher Demonstrates Hardware Backdoor",
Dark Reading July 2012
"Researcher creates proof-of-concept malware
that infects BIOS, network cards"
"New Malware Can Bypass BIOS Security", can fool a host's Trusted Platform Module into thinking that the BIOS firmware is clean when it isn't, Dark Reading May 2013.
"Research Into BIOS Attacks Underscores Their Danger", Dark Reading Nov 2013.
The Computrace / Absolute Track / LoJack system seems like it's either rootkit or backdoor. Read the CoreSecurity review and see the related Black Hat presentation.
Other UEFI hacking resources include:
Hacking the Extensible Firmware Interface (UEFI) Thunderstrike: EFI bootkits for Apple MacBooks Attacks on UEFI security Speed Racer: Exploiting an Intel Flash Protection Race Condition Attacking UEFI Boot Script Attacking UEFI Boot Script Table Vulnerability How your Mac firmware security is completely broken
badBIOS — Real or Not?
The badBIOS story appeared in October, 2013. Dragos Ruiu told about very advanced malware that infected both Mac and PC hardware, reflashing the BIOS, UEFI, or EFI firmware, spreading via ultrasound or signals from software defined radios, traveling in USB memory sticks that were merely plugged in but never mounted..
Compilation of Ruiu's observations
Ars Technica 31 Oct 2013 "Meet 'badBIOS,' the mysterious Mac and PC malware that jumps air gaps"
InfoWorld 1 Nov 2013 "BadBIOS: Next-gen malware or digital myth?"
Ars Technica 5 Nov 2013 "Researcher skepticism grows over badBIOS malware claims"
InfoWorld 12 Nov 2013
"4 reasons BadBIOS isn't real"
includes this analysis:
People following this story fall into a few
different camps. Many believe everything he
says — or at least most of it — is
true.
Others think he's perpetrating a huge social
engineering experiment, to see what he can get
the world and the media to swallow.
A third camp believes he's well-intentioned,
but misguided due to security paranoia
nurtured through the years.
A few even think we're witnessing the public
mental breakdown of a beloved figure.
They point out that paranoid schizophrenics
often claim to be targeted by hidden
communication no one else can hear.
To be honest, I've found myself in all these
camps since the story broke, though I'm
leaning toward those who think Ruiu is
well-intentioned, but perhaps seeing too
much of what he wants to see.
Is Your Hardware Really What You Think It Is?
There have been stories of counterfeit hardware from
Cisco modules down to integrated circuits for some time.
The first thing I noticed explaining just how these parts
get into the parts supply stream was this
Business Week
article,
"Dangerous Fakes",
subtitled
"How counterfeit, defective computer components
from China are getting into U.S. warplanes
and ships".
Given the horror stories it contains of entirely unmonitored suppliers chosen for U.S. military parts based largely if not entirely on their status as "disadvantaged", "woman and minority owned", and so on, I can see why the government didn't explain the details immediately....
Even If You Have AMD Hardware, Is It Really What You Thought It Was?
All AMD processors made during 2000-2010 included a secret debugging feature well outside the standard x86 architecture definition. All processors starting with the Athlon XP have a firmware-controlled feature that can put the CPU into debugging mode. See the article in The Register for an overview, the announcement by the discoverer for far more details, and this list of undocumented Machine Specific Registers in AMD processors.
Modify the processing hardware:
University of Illinois researchers exploited a system by modifying its processing hardware. With Linux running on a programmable LEON processor, based on Sun's Sparc design, they changed 1,341 of the over 1 million logic gates. A carefully crafted network packet injected the malicious firmware, and the attacker could then login as a legitimate user. Note that this would require a processor programmed with an OS with malicious hooks — this seems far-fetched but US DOD warned of this very attack in February 2005 because a shift toward overseas integrated circuit manufacturing could present a security problem. This was reported at the Usenix Workshop on Large-Scale Exploits and Emergent Threats in April 2008, and described in this IDG News article.
See "Stealthy Dopant-Level Hardware Trojans", a paper discussing how to tamper with logic gates by changing the doping of one transistor. This sabotage would be undetectable by optical inspection or functional testing.
Hardware / Firmware Exploits
NSA Hardware and Firmware Guidance
The NSA maintains an official Github account. Among other things, they provide guidance on these classes of vulnerabilities.
NSA Hardware and Firmware Security Guidance
MoonBounce UEFI-Based Rootkit
Kaspersky reported on the MoonBounce UEFI firmware-level
compromise in January 2022.
It's placed in SPI flash memory on the motherboard
instead of touching the disk, making it harder to detect
and capable of persisting through disk replacement.
They attributed it to APT41, a threat actor that has
been widely reported as Chinese-speaking.
Kaspersky analysis of MoonBounce
The First UEFI-Based Rootkit
Researchers at ESET announced in late December 2018
that they had discovered the first example of a UEFI-based
rootkit.
The group known variously as APT28, Sofacy, Fancy Bear,
and Sednit had recently started using this.
The researchers call the rootkit LoJax,
as it's based on Absolute Software's LoJack recovery software.
It takes advantage of firmware vendors allowing remote
re-flashing of firmware.
Detailed write-up
Brief Threatpost story
Supermicro Firmware Vulnerabilities
Research on modifying firmware, providing ultimate access
for attackers:
Firmware Vulnerabilities in Supermicro Systems
Reverse Engineering Firmware with Radare
Radare is a portable reverse-engineering framework and tool set that runs on Linux, OSX, ANdroid, Windows, Solaris, and Haiku.
See this presentation for details on using the radare2 reverse engineering framework and toolset. This can take advantage of CPU microcode, Intel and AMD controller chipsets, PCIe chips, Intel Ethernet controllers, magnetic and solid-state disk controllers, controllers in mice and keyboards and touchpads, controllers in webcams, PCI/PCIe option ROMs,
Subvert the Intel Management Engine
The Intel Management Engine
is a microcontroller that handles data transfer
between the processor and peripherals.
EFF on Intel Management Engine
Background on IME
In May 2017 researchers discovered a remote code execution
vulnerability (tracked as CVE-2017-5689) in this controller.
"A critical RCE flaw in Intel Management Engine
affects Intel enterprise PCs, dates back 9 years"
CVE-2017-5689
In August 2017 they discovered an undocumented setting
to disable the controller.
"Experts found an undocumented Kill Switch
in Intel Management Engine"
Later in 2017 we learned that the Management Engine runs
MINIX with a full network stack and a web server.
This is down at Ring –3.
That is, "minus 3", three levels below
what your kernel can see.
Google presentation
Dmitry Sklyarov analysis
Network World story
Techdirt story
Intel's advisory
Attack the Intel SGX Enclave:
Intel's SGX or Software Guard Extensions was intended to provide a secure enclave protected even from the Management Engine. Another term for this is a Trusted Execution Environment.
Well, it wasn't secure after all.
Intel refers to the vulnerability as L1TF
or Level 1 Terminal Fault.
See the Foreshadow speculative execution
attacks.
The original version extracts data from the SGX enclave.
The next-generation version can extract any data in the L1
cache, including memory in use by
virtual machines, hypervisors,
the operating system kernel,
and System Management Mode (or SMM) memory.
Foreshadow
Original Foreshadow paper
Foreshadow-NG technical report
CVE-2018-3615 (vs SGX)
CVE-2018-3620 (vs OS kernel & SMM)
CVE-2018-3646 (vs VMs)
Intel on L1TF
US-CERT on L1TF
The SGX attacks keep appearing:
Foreshadow Crosstalk description Crosstalk paper Intel on SGX attacks
Attack the Apple T2 security chip
Apple's T2 security chip was launched in 2017.
Within two to three years it was being exploited by the
same method used to jailbreak older iPhones.
This could disable macOS security features including
System Integrity Protection and Secure Boot.
It might also be exploited to obtain FileVault encryption
keys and decrypt user data.
Ars Technica on the flaw
Pangu Team vulnerability disclosure
Modify or Replace the Volume Boot Record:
FireEye identified malware modifying the Volume Boot Record, hijacking the system boot process. FireEye calls the group "FIN1", which they speculate is located in Russia or at least the group largely speaks Russian. FireEye calls the specific software "BOOTRASH", it's part of an overall system that its developers call "Nemesis." FIN1 is targeting payment card data for financial gain. ArsTechnica also covered the story with comparisons to other so-called bootkits.
Update Intel and AMD Processor Microcode:
Ben Hawkes' Notes on Intel Microcode Updates discusses how updateable CPU microcode exists to work around hardware and firmware bugs. There is speculation that malicious changes might be able to move sensitive data to a known location, but Hawkes' work shows there are RSA digital signatures, using SHA-1 on older processor models and SHA-2-256 in newer processors.
Modify USB firmware:
The firmware is proprietary so we have no "known good" for comparison. Plus, as the U.S. Government has demonstrated, they have no interest in closing this particular security hole.
BadUSB is an attack on the firmware controllers in typical USB devices. Malware on the system can subvert an attached USB device, and a hostile USB device can attack a system into which it is plugged.
Practical BadUSB attack software is available.
Modify RAM contents while running:
The Rowhammer vulnerability in DRAM devices is based on repeatedly accessing a row in high-density DRAM devices and flipping bits in adjacent rows. A Google team has demonstrated and documented using this to gain kernel privileges.
In July 2015 a group of Austrian and French researchers demonstrated a JavaScript attack, Rowhammer.js, meaning that an attacker only had to insert hostile JavaScript code into a page and wait for someone on a vulnerable platform to view that page with a browser.
The good news is that it's a much larger challenge to flip the bits in a constructive way that provides access for the attacker.
Turn off the NX bit while running:
The NX bit, also called the XD bit, is used by CPUs to enforce memory segregation into instructions versus data. Intel calls it XD for eXecute Disable, AMD calls it Enhanced Virus Protection, and ARM processors call it XN for eXecute Never. This feature is enabled as a BIOS setting, and so it would appear to be down in the hardware where neither applications nor the operating system can reach it. But... The NX bit is simply a hardware feature that may or may not be available. Even if available, the operating system may not use it.
For example, in Windows, Data Execution Prevention or DEP is Microsoft's name for support of this technology in the operating system. This page explains how to turn it on for specific programs or for all programs.
See the Wikipedia page on the NX bit for detailed descriptions of the technology and its support on various combinations of operating systems and processors.
Modify the TPM (Trusted Platform Module) chip:
In February, 2010, Christopher Tarnovsky announced a successful hardware exploit of an Infineon TPM chip.
Background: What is TPM?
Short overview at hackaday.com
Associated Press story
More technical article at Dark Reading,
with links to more detail
Freeze the memory:
Princeton researchers reported
cold boot attacks — literally cold boot.
The problem — sensitive information such as
passwords used for file system encryption and
some file contents themselves may remain in RAM
for surprising amounts of time, especially if
the RAM is chilled.
See the original report from Princeton
and discussion and news coverage:
Original report from Princeton
New York Times 22 Feb 2008
Bruce Schneier's blog
Wired magazine, February 2008
Break in through the Firewire port:
Winlockpwn is a tool where the attacker connects a Linux machine to the Firewire port. The attacker gets full read-write access to memory and the tool deactivates Window's password protection residing in local memory. Steal passwords, drop malware on the system, and so on. Similar hacks have been demonstrated against Linux and macOS. See the Dark Reading story
Break in through the network interface hardware:
There's been some work on attacking the firmware on network interface cards, some of which focuses on permanently damaging the card. But more interesting work looks at attacking the NICs on a firewall so they do PCI-to-PCI data transfers, moving information down at a hardware level where firewalls don't look. There is speculation this might allow reading the disk device through its PCI-based controller. See this discussion, referencing an excerpt from the Robust Open Source mailing list.
Kristian Kielhofner's Packets of Death describes how problems with Intel's 82574L Ethernet controller has vulnerabilities: "death packets" containing the correct pattern can shut down an interface. It turns it off — the link lights on the card and the switch go out and only a power cycle can turn it back on. The "kill code" data pattern can be in the application layer payload, so a hostile HTTP server could put the pattern in an HTTP 200 response and shut down client machines behind a firewall.
The network interface may have its own processor powerful
enough to run an SSH server.
See these examples:
What if you can't trust your network card?
(paper)
Can you still trust your network card?
(presentation)
CVE-2010-0104
Network Interface Card SSH Rootkit
Project Maux Mk.II
Closer to Metal: Reverse engineering the
Broadcom NetExtreme's firmware
Exploit the disk controllers:
Storage devices, both rotating magnetic disk and
solid-state drives, have their own controllers.
That is, the SATA or SCSI or whatever interface has its
own processor with firmware, but
the storage device itself
also has one.
The SATA/SCSI/etc interface is on the motherboard or an
expansion card,
the drive controller is inside the small box containing
the drive.
Most of these are ARM and MIPS controllers.
Some of the firmware is stored in an embedded flash chip,
the rest is on hidden sectors of the disk.
Seagate:
Exploring the impact of a hard drive backdoor
Western Digital:
Hard disk hacking
Exploit the SD/MMC memory cards:
They include 8051 and H8 processors.
The Exploration and Exploitation of an
SD Memory Card (video)
The Exploration and Exploitation of an
SD Memory Card (slides)
Exploit the processor and firmware in the mouse and keyboard:
Logitech G600 mouse has an AVR architecture ATmega32u2
processor:
Mouse Trap: Exploiting Firmware Updates in
USB Peripherals
(paper and slides)
Mouse Trap: Exploiting Firmware Updates in
USB Peripherals
(paper)
KBT Poker II keyboard has a
Nuvoton NUC122SC1AN
ARM Cortex-M0 CPU with reflashable firmware:
Manufacturer's announcement of firmware release
Finding the executable code in the firmware
Firmware at GitHub
Ectool
is a small utility that dumps the flash RAM of a
laptop's Embedded/Environmental Controller or EC,
typically an 8-bit or 16-bit processor.
Table of EC details, links to much more
Synaptics TouchPads use an AVR or PIC architecture.
Synaptics TouchPad Interfacing Guide
Synaptics RM13 Interfacing Guide
Synaptics RM14 Specification
Synaptics PS/2 TouchPad Interfacing Guide
Exploit the webcam:
Reverse engineer and modify the firmware run by the processor in the webcam
Modify Intel AMT firmware:
Intel Active Management Technology
or AMT is part of the Intel Management Engine, built into
systems with Intel vPro technology.
It's intended for remote out-of-band management.
Video explaining the exploit:
Persistent, Stealthy, Remote-controlled Dedicated
Hardware Malware
Igor Skochinsky's presentation:
Intel ME Secrets: Hidden code in your chipset
and how to discover what exactly it does.
Exploit PCI / PCIe Option ROMs
PCI / PCIe expansion cards can have their own firmware,
and it might be exploited:
BIOS Disassembly Ninjutsu Uncovered
Building a "Kernel" in PCI Expansion ROM
Option ROMs: A Hidden (But Privileged) World
Broadcom Wi-Fi Firmware Vulnerability
CVE-2017-9417
is a heap overflow on Broadcom Wi-Fi chips,
triggered by a packet with a WME (Quality-of-Service)
information element with a malformed length.
Analysis
Proof of concept
Detailed description
Intel Atom "System on Chip" (or SoC) Bugs
In early 2017 Cisco issued an advisory warning about the failures of a clock signal component manufactured by one of their suppliers. They said:
Although the Cisco products with this component are currently performing normally, we expect product failures to increase over the years, beginning after the unit has been in operation for approximately 18 months. Although the issue may begin to occur around 18 months in operation, we don't expect a noticeable increase in failures until year three of runtime. Once the component has failed, the system will stop functioning, will not boot, and is not recoverable.
Others reported the problem on Synology storage devices and various products from Dell, HP, NEC, NetGear, SuperMicro, and other manufacturers. The problem seems to come from the Intel Atom s2000 SoC, as indicated by Intel's Specification Update, which stated that its clock may stop functioning and the SoC will no longer boot. The parts started shipping in 2013.
Cisco advisory The Register Router Jockey Intel Specification Update Synology community forum ClockGate 2017 on cantechit
Virtualization / Emulation Bugs
VirtualBox is a virtualization product that used to be from Innobox, which was purchased by Sun, which was purchased by Oracle.
See this message
from the OpenBSD project leader reporting that
CPU registers become corrupted under VirtualBox.
"We don't know how other operating system products
continue running when the userland ecx register
gets clobbered on a return from a page fault,
but at least people should be aware that there
is likely some security risk from running that
product.
That VM does not emulate the x86 correctly,
(either)."
See my page on Violating Virtualization Security for more information on Type 1 and Type 2 virtualization vulnerabilities, VM escape, the use of malicious hypervisors, and more.
How Not to Respond to Intrusions
The IT security department of the Economic Development Administration within the Department of Commerce ridiculously over-reacted and spent over $2.7 million destroying $170,000 in hardware including desktop computers, cameras, printers, keyboards and even mice after they were informed of a potential malware infection. They would have destroyed even more hardware but they ran out of money to continue the idiotic operation.
See the Network World overview and the official Office of the Inspector General report for further details.