
Government Electronic Surveillance
The walls have ears, behave accordingly.
The U.S. Government's surveillance of its own citizens seems like that of East Germany and Oceania at times, but the only thing really new about the PRISM / US-984XN / XKeyscore / Boundless Informant revelations beginning in June 2013 was the public announcement. After all, domestic surveillance activity ramped up soon after September 2001. But domestic surveillance by the U.S. government goes much further back.
"Qu'on me donne six lignes écrites de la main du plus honnête homme, j'y trouverai de quoi le faire pendre."
"If one would give me six lines written by the hand of the most honest man, I would find something in them to have him hanged."
— Cardinal Richelieu
This is not new.
The Internet has been an arena for surveillance all along. Much of what you find helpful, convenient, and even fun works because of all the tracking you aren't fully aware of most if not all of the time.
Let's take a calm look at some clear analysis that came out during the three months before the PRISM story exploded. As Bruce Schneier wrote for CNN in March, 2013:
[...]
So, we're done. Welcome to a world where Google knows exactly what sort of porn you all like, and more about your interests than your spouse does. Welcome to a world where your cell phone company knows exactly where you are all the time. Welcome to the end of private conversations, because increasingly your conversations are conducted by e-mail, text, or social networking sites. And welcome to a world where all of this, and everything else that you do or is done on a computer, is saved, correlated, studied, passed around from company to company without your knowledge or consent; and where the government accesses it at will without a warrant.
In April, 2013, Schneier wrote for The Atlantic:
[...]
Soon, governments won't have to bother collecting personal data. We're willingly giving it to a vast network of for-profit data collectors, and they're more than happy to pass it on to the government without our knowledge or consent.
Then in early May, 2013, still before the PRISM revelation, Schneier wrote for The Atlantic:
[...]
Second, we need to ensure that law enforcement does what we expect it to do and nothing more. Police powers are invariably abused. Mission creep is inevitable, and it results in laws designed to combat one particular type of crime being used for an ever-widening array of crimes. Transparency is the only way we have of knowing when this is going on.
[...]
As we respond to the threat of terrorism, we must remember that there are other threats as well. A society without transparency and accountability is the very definition of a police state. And while a police state might have a low crime rate — especially if you don't define police corruption and other abuses of power as crime — and an even lower terrorism rate, it's not a society that most of us would willingly choose to live in. We already give law enforcement enormous power to intrude into our lives. We do this because we know they need this power to catch criminals, and we're all safer thereby. But because we recognize that a powerful police force is itself a danger to society, we must temper this power with transparency and accountability.

Brownstone at 141 East 37th Street in New York. This was the home of the U.S. Government's "Black Chamber" code breaking operation run by Herbert Yardley in the 1920s.

|

|
Meanwhile, U.S. cloud providers have made it clear since 2011 that they will silently hand over data to U.S. authorities, even when that data is physically stored in the EU where that transfer is illegal.
For background read the Congressional Research Service report Cloud Computing: Constitutional and Statutory Privacy Protections. Congress refuses to release these public documents to the public. The problem is that the Congressional Research Service is scrupulously non-partisan, so most Congress members dislike CRS for not slanting things their way. The good news is that the Federation of American Scientists makes these available to the U.S. public.
Amazon
ASIN: 1591149894
Large-scale U.S. government surveillance of its citizens and the imprisonment without charge of suspicious foreigners goes back to a fear of terrorism. Some of the surveillance scaled up after that horrific bombing on the East Coast where 38 people were killed.
Wait, what? 38 people?
1920Wall Street
bombing
Only three people were killed in the two bomb explosions at the 2013 Boston Marathon. But 38 people were killed and 143 people seriously injured at noon on September 16, 1920 when a shrapnel-packed bomb exploded on Wall Street in Manhattan.
This was just one of a wave of bombings in the U.S. from 1910 through the early 1930s perpetrated by anarchists and labor radicals, with a whole series of bombings in 1919.
Dashiell Hammett's Red Harvest was based on a violent event in Montana during this period. Beverly Gage's The Day Wall Street Exploded describes the Wall Street bombing and its whole bomb-plagued era in detail. And then Akira Kurosawa made Yojimbo and Sergio Leone made A Fistful of Dollars based on Red Harvest.
Amazon
ASIN: B001ON78SO
Amazon
ASIN: 0679722610
J. Edgar Hoover got his start with the Justice Department in its War Emergency Division, becoming head of its Alien Enemy Bureau and authorized by President Woodrow Wilson to arrest and jail disloyal foreigners without trial. In 1919 he became head of its new General Intelligence Division, also called the Radical Division, monitoring and disrupting domestic radicals. U.S. government domestic surveillance underwent a huge increase and has never been dialed back.
A former U.S. State Department staff member wrote in the Washington Post in 2014 that Reagan's Executive Order 12333 from December, 1981, is worse than the Patriot Act. All the NSA has to do is traffic shaping, manipulation of routing done normally to balance traffic loads, and 12333 lets them sample all content of traffic between two Americans under no formal suspicion or surveillance order. Being an American and communicating is itself suspicious enough.
In October 2014 the American Civil Liberties Union announced that the U.S. Government had released documents showing that the NSA relies on Reagan's Executive Order 12333 as the basis for the majority of its surveillance activity.
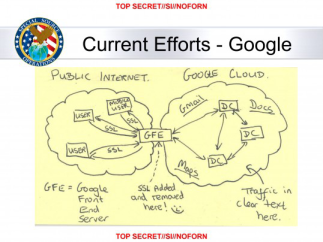
Slide from NSA presentation on "Google Cloud Exploitation" showing where internal communications are compromised.
Before the 20th Century bombings, an 1877 U.S. Supreme Court decision on the government's ability to inspect the content of letters sent via the postal service found that "No law of Congress can place in the hands of officials connected with the postal service any authority to invade the secrecy of letters and such sealed packages in the mail; and all regulations adopted as to mail matter of this kind must be in subordination to the great principle embodied in the fourth amendment of the Constitution."
But then there were Project SHAMROCK (1945-1975) collecting telegraph communications, Project MINARET (1960-1973) with its watch lists for terms and names, and the Drug Watch Lists (1970-1973). For descriptions of all three see " A Review of Intelligence Oversight Failure: NSA Programs that Affected Americans" by Major Dave Owen, Military Intelligence Professional Bulletin, Oct-Dec 2012, pp 33-39.
Stingray Family
Surveillance Manuals U.S. Government
catalog of mobile
surveillance gear
A very clear explanation of how SIGINT works is in Section 2 of this document, in which GCHQ sets out goals for long-term data mining research goals for the Heilbronn Institute for Mathematical Research at the University of Bristol.
As for PRISM itself, see the initial story in The Guardian and the following story in The Washington Post.
For the MUSCULAR program in which NSA and GCHQ exploit internal communications at Google and Yahoo, see the 30 Oct 2013 Washington Post story "NSA infiltrates links to Yahoo, Google data centers worldwide, Snowden documents say", and the 4 Nov 2013 Washington Post story "How we know the NSA had access to internal Google and Yahoo cloud data".
Articles in Foreign Policy, RT, Techdirt and elsewhere shed some light on the FBI's DITU (pronounced dee-too) or Data Intercept Technology Unit. DITU is part of FBI's Operational Technology Division, which does electronic surveillance, code breaking, and black bag jobs to install surveillance hardware and spyware. It's a key part of PRISM, in "a sprawling compound" at Marine Corps Base Quantico and among the most secretive groups there. It's at one end of a direct fiber link from Quantico to Ft Meade.
DITU works with the "big three" carriers AT&T, Verizon, and Sprint to intercept domestic traffic and hand it over to NSA. It also works with technology companies like Google, Facebook, Apple, etc. DITU managed the FBI Carnivore system in late 1990s. This lets technology companies claim — correctly — that they provide no information to NSA. They give it to FBI, who passes it to NSA.
TAO or the Office of Tailored Access Operations has been the NSA's top operational unit and its fastest growing. It carries out "Computer Network Exploitation" or CNE, subverting endpoint devices such as servers, workstations, and mobile computing devices, as well as network infrastructure including switches, routers, and firewalls, and other networked infrastructure including phone switches and SCADA systems. They also intercept shipments to modify software, firmware, and hardware on computer systems being shipped from manufacturers who don't cooperate with the NSA.
A multi-part article in Der Spiegel has an overview of TAO including its subversion of the SEA-ME-WE-4 cable system interconnecting Europe, North Africa and the Gulf States, and south and southeast Asia.
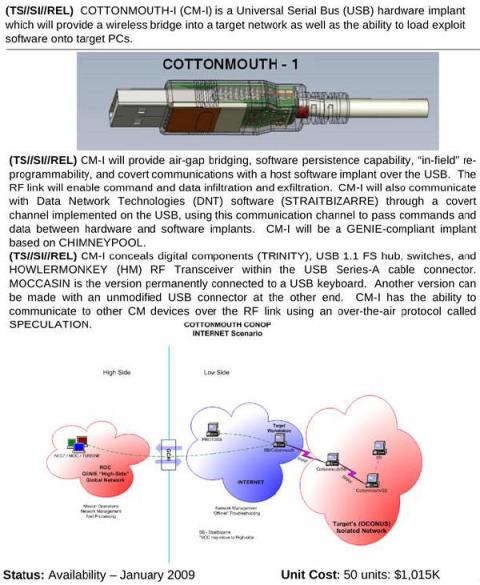
Another Der Spiegel article describes a 50-page internal "product catalog" from an NSA division called ANT, listing hardware and software (called "implants" in NSA terminology) which can penetrate systems to monitor, modify, and extract information. These include modified cables allowing "TAO personnel to see what is displayed on the targeted monitor", USB plugs and cables that covertly communicate over radio links (see the COTTONMOUTH device at right), replacement USB and Ethernet ports with covert data capture and communications built in, replacement chips and daughter cards to exploit the motherboard BIOS and using System Management Mode to reload itself at every boot, up to active GSM base stations that mimic legitimate mobile phone towers and therefore monitor and even control nearby mobile phones. ANT also attacks the firmware in disk drives manufactured by Western Digital, Seagate, Maxtor, and Samsung, and modifies hardware and/or firmware in Cisco, Juniper, and Huawei routers and firewalls. Cryptome has the full NSA ANT catalog available for download. A Wired article also discusses the catalog.
A Close Look at the NSA's Most Powerful Internet Attack Tool, a Wired article in March 2014, discussed the QUANTUM system. It's really a broad toolkit for network monitoring, exploitation, and attack.
Kaspersky Labs released a report in February 2015 describing what they call the "Equation Group", this seems to be their discovery of NSA TAO software and firmware in some of their customers' systems. Software and firmware, as it includes the ability to modify the firmware within more than a dozen brands of disk drives including Maxtor, Seagate, Hitachi, and Toshiba. Kaspersky describes this as the most sophisticated attack group of the approximately 60 such groups they track. The Equation Group software and firmware has ties to both Stuxnet and Flame among others, and goes back at least to 2001. Kaspersky has detected it in their customers' systems in at least 30 countries, concentrated in Iran, Russia, and Pakistan.
BlackBerry / RIM, Apple, and Nokia Give Up Data Under Government Pressure
The national governments of Saudi Arabia, the United Arab Emirates, and India threatened to block all BlackBerry use in their countries unless Research in Motion gave those governments the ability to read all BlackBerry traffic. That was reported by the BBC on 1 August, 6 August, and 13 August, 2010, and in The Guardian and then updated in The New York Times on 8 October, 2010.
Two years later, in August 2012, The Economic Times reported that RIM had demonstrated a solution from Verint that intercepts BlackBerry traffic and makes it available to the Indian security agencies. The government then planned to require all telecommunications companies to connect their networks to the RIM-built taps.
It was more than RIM — Nokia and Apple also provided backdoors for the Indian government. How do we know this? ComputerWorld reported that the Indian hacker group "The Lords of Dharmaraja" has posted documents they downloaded from an Indian military network. These documents discussed "Tactical Network for Cellular Surveillance (TANCS)" and the cellular and Internet surveillance operations continuing since April 2011 by India's military intelligence and Central Bureau of Investigation. In exchange for access to the Indian market, manufacturers including RIM, Nokia and Apple (collectively defined as "RINOA" in the document) agreed to provide backdoor accesson their devices. The Indian government then used those backdoors to intercept internal e-mails of the U.S.-China Economic and Security Review Commission, a U.S. body mandated with monitoring, investigating, and reporting to Congress on the trade relationship between the U.S. and china.
Then, in 2015, BlackBerry announced that they would shut down operations in Pakistan rather than (continue to) provide the government with backdoor access to encrypted data. See the CNet and CBC stories for more.
BlackBerry Weaknesses
Meanwhile, either BlackBerry was poorly designed or else the backdoors imposed by governments were too obvious. Elcomsoft announced a weakness in BlackBerry's use of the AES cipher in BlackBerry Desktop Software, its PC and Mac backup program. It's surprisingly easy to discover the password for the backup archive, which typically includes the contact list and the password settings for e-mail and WiFi. The attack takes "a few days" on an Intel Core i7 processor, but it's considerably faster on graphics hardware, like a GPU-based compute cluster you can rent on Amazon's EC2 cloud computing platform for US$ 2.40 per hour or less.
"In short, standard key-derivation function, PBKDF2, is used in a very strange way, to say the least. Where Apple has used 2,000 iterations in iOS 3.x, and 10,000 iterations in iOS 4.x, BlackBerry uses only one", as Elcomsoft's Vladimir Katalov explained it in a blog posting.
Elcomsoft soon had software for BlackBerry; Apple's iPhone, iPad, and iPod Touch; plus an iOS Forensic Toolkit available "only to selected law enforcement, forensic and intelligence agencies".
See the discussion in Network World and CIO.
Microsoft Live@edu Intentional Backdoors
Microsoft's Live@edu e-mail service created for universities and now also widely used in secondary and primary education in the U.S. is terribly insecure for the users themselves, despite Microsoft's claim that it is more secure. As described in Microsoft's FAQ page and discussed in Network World, data is not encrypted on the servers.

Secure. Microsoft keeps insisting that their cloud services are secure.
Yes, an encrypted TLS/SSL connection is established to the server, but your data is not encrypted while stored on the servers. A Microsoft director is quoted as saying "the password is encrypted on the server", even though you do not stored encrypted passwords if you want any security! (Tip to Microsoft: the rest of the world has realized this for decades and we instead store hashes of passwords.)
Why an intentionally insecure design?
Microsoft markets cleartext e-mail storage as a good thing somehow. I'm sure they will dream up scenarios of detecting a would-be massacre planner, and it is also handy for the administration to monitor the communication between faculty and staff to make sure they don't communicate without their bosses eavesdropping.
I have heard more than one story about a school that moved to this or similar all-cleartext e-mail easily accessible to school administrators. What quickly happened is that everyone, faculty and students, quickly moved all their communication to Gmail or similar.
The Problem With Backdoors
The problemwith backdoors
Government-imposed backdoors cause huge problems. "Exceptional access" for law enforcement leads to greatly decreased security for individuals, businesses, and the very government itself. Details and examples are here.
Secure E-mail Providers Shut Down, Then New Projects Appear
A number of secure e-mail providers shut down soon after the summer 2013 revelations of the U.S. government's US-984XN or PRISM mass surveillance and XKeyscore and Boundless Informant "big data" analysis and visualization systems.
Lavabit announced in August 2013 that it was immediately shutting down its service to avoid becoming "complicit in crimes against the American people." He had had some experiences over the preceding six weeks that he could not share because of laws he could not legally discuss. Network World reported this story. Lavabit's founder was interviewed by Forbes, saying "If you knew what I know about email, you might not use it."
Silent Circle was still resisting government demands for wiretapping backdoors as of early June, 2013. But Silent Circle also shut down its E-mail service in August, 2013. They kept operating their encrypted voice and text services, but they shut down their e-mail services.
The US-984XN / PRISM / Boundless Informant revelations led to international outrage, even though many other countries do the same thing. While representatives of the German government howled in outrage, the ITIF analysis of the financial impact of the surveillance reported that German intelligence uses the G10 act to monitor telecommunications without a court order.
Then, in October, Der Spiegel reported that the Bundesnachrichtendienst or BND, the German foreign intelligence agency, has taps on DE-CIX, the major Internet Exchange Point (or IXP) in Frankfurt. This gives BND access to data sent through the world's largest Internet Exchange Point with peak traffic over 2.5 terabits per second.
All the same, in October 2013 the Brazilian President Dilma Rousseff announced that her government's SERPRO or Federal Data Processing Service was to create a secure e-mail system in an attempt to shield their communications from surveillance by the U.S. and others. This was reported by FRANCE 24, Deutsche Welle, Help Net Security and others.
The Dark Mail Alliance was announced at the end of October 2013, in Forbes and on ThreatPost on 30 October and 1 November. Lavabit and Silent Circle founded it, they intend to design a system with end-to-end encryption that separates the routing and addressing from the message content.
Electronic Surveillance Agencies
Here are some organizations that take information security and/or communications security very seriously indeed, some of which also expend some effort in breaking that of other peoples.
Depending on who and where you are, the below list will likely contain some mix of good guys and bad guys.
- Australia
- Canada
- Finland — Puolustusvoimien tiedustelulaitos (PVTIEDL) is the combined SIGIN, GEOINT, and IMINT agency of the Finnish Defense Forces.
- Germany — Bundesamt fur Sicherheit in der Informationstechnik, (Federal Office for Information Security, or BSI), is Germany's equivalent of the NSA.
- India
- Israel — Unit 8200 (8200 יחידה)
-
Japan
- Bōeishōjōhohonbu (Defense Intelligence Headquarters)
- Directorate for Signals Intelligence (the article has some obvious errors)
- Netherlands — NSO or Nationale SIGINT Organisatie is part of MIVD or Militaire Inlichtingen- en Veiligheidsdienst, the Dutch Military Intelligence and Security Service.
- New Zealand — Government Communications Security Bureau
-
Russia
- Служба Специальной Связи и Информации, Спецсвязь России (Spetssviaz, Special Communications and Information Service of the Federal Protective Service of the Russian Federation) is the successor of FAPSI, established in 2003 from the 8th Main Directorate (Government Communications) and 16th Directorate (Electronic Intelligence) of the KGB. It was incorporated into the Federal Protective Service or FSO in 2004.
- ФСБ (FSB) — Федеральная Служба Безопасности (Federal'naya Sluzhba Bezopasnosti, or Federal Department of Security) is the new name for Komityet Gosudarstvyenoy Bezopasnosti, the Committee for State Security, or the KGB.
- South Korea — National Intelligence Service — also with an English page.
- Spain — Centro Nacional de Inteligencia
- Sweden
- Turkey
-
Ukraine
- Державна Служба спеціального Зв'язку та Захисту Інформації України (Derzhspetszviazok, State Service of Special Communications and Information Protection of Ukraine)
- Sluzhba Bespeky Ukrayiny (SBU) (Security Service of Ukraine)
- United Kingdom
-
United States of America —
Note that NSA is the main comsec/sigint agency in
the U.S., although NRO operates satellites for NSA,
and DIA runs some of the other data-gathering
operations.
- CIA — Central Intelligence Agency
- DIA — Defense Intelligence Agency
- FBI — Federal Bureau of Investigation
- NRO — National Reconnaissance Office
- NGA — National Geospatial-Intelligence Agency It formed out of (among other things) NIMA — National Imagery and Mapping Agency, the home of Admiral James Sandecker. Or so I always claim. And confusingly overlapping with NRO. NRO operates the satellites, the sensors they carry are operated by NGA and NSA.
- NSA — National Security Agency. There was a lot of controversy over the NSA's listening to Europe in the late 1990s, which mostly proved that the Europeans hadn't been paying attention.
Back to the main Security Page