
Authentication Tools
Authentication Concepts
Authentication is based one or more of these:
• Things you know (password, PIN, etc)
• Things you have (physical tokens:
badge, RSA token, etc)
• Things you are (biometrics:
fingerprint, hand shape, iris pattern, etc)
• The Way You Do Things
(behavioral)
Those are listed in the order of how often they are used today on computer systems: passwords are the most common, and so on. DARPA's Active Authentication research project just started around 2015 and there don't seem to be any usefully practical implementations yet. (Yes, there are early systems in this area, but nothing I've heard of that's a significant advancement) However, human society has used different versions of these over the millennia.
Something you are is the oldest, predating language. Is that a family member that should be allowed into the shelter? That method secured access to rock shelters occupied by hominids and early humans. That evolved over millennia into official guards only allowing recognized persons to enter controlled spaces. Only recognized advisors and family members were allowed into the royal chamber.
Something you know would have been the next one. The guard doesn't recognize the visitor, but the visitor knows the special pass phrase needed to gain admittance.
Something you have would have started with the development of stamps which could create recognizable patterns. Artisans with the skill required to create the technology to generate stamped clay tablets or papyrus sheets would have been employed by the state, with counterfeiting forbidden under penalty of death.
Something you do is based on how you behave, physically and/or linguistically. Yes, DARPA and others are working on current research projects for behavioral recognition, but it's been used for authentication at least since the Bronze Age. Consider the following passage, describing events from around 1370-1070 BCE and probably written around 700 BCE. The inhabitants of Giliad, a mountainous region east of the Jordan River, had defeated the invading tribe of Ephraim. The surviving Ephraimites were trying to cross back over the River Jordan into their home territory. In order to identify and kill them, the Giliadites blocked the river crossings and told each suspected Ephraimite to say the word שְׁבּׂלְת or shibboleth. The Ephraimite dialect did not contain the "sh" (or ש) sound, so anyone pronouncing it as sibboleth was killed. The reported body count was 42,000.
1 The Ephraimites were called up for battle and crossed over to Zaphon. They said to Jephthah, "Why did you cross over to fight the Ammonites and not call us to go with you? We're going to burn down your house over you!" 2 Jephthah replied to them, "My people and I were in a great conflict with the Ammonites. But when I cried out to you, you didn't rescue me from their power. 3 When I saw that you weren't going to rescue me, I risked my own life and crossed over against the Ammonites, and the Lord handed them over to me. So why have you marched against me today to fight me?" 4 So Jephthah gathered all the men of Gilead and fought the Ephraimites. The Gileadites defeated the Ephraimites, because they had said, "You are fugitives from Ephraim! Gilead stands within Ephraim and Manasseh." 5 The Gileadites took control of the Jordan's crossing points into Ephraim. Whenever one of the Ephraimite fugitives said, "Let me cross," the Gileadites would ask him, "Are you an Ephraimite?" If he said, "No," 6 they would tell him, "Then say shibboleth." But he would say, "sibboleth," because he couldn't pronounce it correctly. So they would seize him and kill him at the Jordan's crossing points. Forty-two thousand of the Ephraimites fell at that time.
Judges 12:1-6
Today we have circled back to Things You Know, passwords or pass phrases or PINs. As you'll see below, passwords aren't nearly as useful as we would like to think they are.
Just Once, or Every Time?
Within an organization, you might have a few dozen systems that you must authenticate to during one work day. Single Sign-On or SSO becomes the goal. SSO (or ESSO, for Enterprise SSO, and not the Canadian gasoline company) requires the user to authenticate just once each morning with a password or pass phrase. It then automatically presents proof of that at every subsequent authentication. The user doesn't notice the later authentication events, they are automatically handled by something within their session.
Building an Active Directory server with SambaKerberos is a prominent example of a trusted single sign-on system. It's very widely used, as it is one of the components of Active Directory (along with DNS and LDAP). Microsoft is responsible for the popularity of Active Directory, but you don't have to run Windows to have an AD server. The Samba package included in free operating systems including Linux and FreeBSD provides full Active Directory service. See my page explaining how to build an Active Directory server using free software on a free operating system.
Kerberos or another SSO makes things easier for the user. Organized carefully, it can make things easier for the administrators. But it isn't magic. An SSO can make security far worse if it isn't used cautiously.
Single sign-on puts all your eggs into one basket. If just one password or pass phrase is stolen or guessed, then all resources and identities are compromised. Every user must be extremely careful when designing and protecting that single password or pass phrase.
You can limit exposure by using unique passwords or pass phrases on every system. If one is compromised, then only that one resource is exposed.
It's a trade-off: convenience versus security. If one goes up, the other must go down.
Use a password manager like KeePass.
Physical Tokens
Below is a proximity card or just a "prox card" for short, and a similar key-fob-like proximity device. These are unpowered RFID systems. You hold the device against a reader to unlock an outer door, or to command an elevator outside normal operating hours to do anything other than go to the lobby.
Proximity devicesin capsule hotels
in Japan
I've been told that if you find one of these,
you can call Datawatch Systems at the toll-free
number listed on the card, read off the code
number printed on it, and they will tell you
where it can be used.
+1-800-899-9872, 301-39731,
and 234-56540 11101450973-1
if you're trying to read these examples.



Smart Phone Apps Make Your Phone a Token
In 2015 the Hilton chain of hotels began to deploy a "digital key" system in which your smart phone can serve as your room key.
You have to install the Hilton HHonors app and tell it your HHonors number and password. Then, once your room is ready, data will be available the next time you start the app.
I had assumed it would use NFC (or Near-Field Communication), easier to integrate with the proximity sensors already in use at some hotels. On those you hold the key card near the disk on the door exterior, there is no slot in which to dip it.
But this phone-based system uses Bluetooth to communicate with what look like conventional hotel door locks with slots for magnetic key cards. The bottom of the lock mechanism has the usual coaxial DC power connector and 1/8" jack for over-riding with a handheld device.
The app says to get within five feet, but it would usually detect the door and work within ten to fifteen feet. The app has detected a door that it knows how to unlock, and shows you which it is — "My Room" or "Concierge Lounge". You press the circle: blinking, wait, blinking, wait, after about 5 seconds the door unlocks. The green LED on the door lights, and the app shows "Unlocked!"
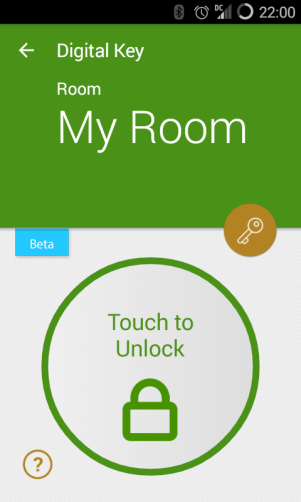
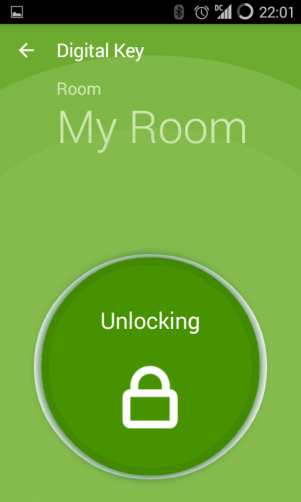
I got "My Room" and "Concierge Lounge" when near those two places, but the phone also successfully discovered "Main" in the lobby near the elevators. I could apparently unlock whatever this was, getting the successful "Unlocked!" indication on the phone, but no secret doorway swung open. I tried it a number of times in the area, but couldn't see anything happening and I couldn't figure out where the signal was coming from.
I don't really have high expectations for hotel door lock security to start with, so I don't see this as making things any worse. The standard Onity hotel locks were spectacularly hacked a few years ago.
This system is not just something you know. It's something you have, and have charged, and on which you have booted the OS, and started the app, and the app has found the stored keys, and the app has checked for updates from the network. And talk about applying ridiculous amounts of computing power to solve a simple problem... Even my old phone has about 1.6 times the compute power and 16 times the memory of a Cray X-MP, the world's fastest supercomputer from 1983-1985.
Windows Authentication
Microsoft has a very nice page describing Credentials Management in Windows Authentication.
Securus Global has a nice article on dumping Windows credentials. Once you have SYSTEM level access, you may have better things to do than dump user credentials. But it's possible that credentials on a poorly secured host could lead to far more useful credentials elsewhere.
First, save the SYSTEM, SECURITY, and SAM hives to your USB drive:
C:\> mkdir e:\collection C:\> reg.exe save hklm\sam e:\collection\sam.save C:\> reg.exe save hklm\security e:\collection\security.save C:\> reg.exe save hklm\system e:\collection\system.save
Then, collect the hashes of the passwords for local accounts, cached domain credentials, and LSA secrets using secretsdump.py.
Attack those with password cracking tools or use a Pass the Hash attack.
How to Create Strong Passwords
Here is a very good essay on how to choose good passwords. Explanations of why common schemes generate passwords that are hard to remember but easy for automated attacks to find, suggestions for making very strong passwords that can be remembered.
Well-Known Default Passwords
Many systems come with well-known default passwords
which go unchanged by lazy admins.
Here are lists, do you have any remaining risks?:
phenoelit-us.org
cirt.net
defaultpassword.com
The "What's My Pass?" page
claims to list
"The Top 500 Worst Passwords of All Time",
but there is no explanation of where they got that data.
Since admin isn't even on the list despite being
the default password on lots of network gear, I don't think
the list is very authoritative.
But it's kind of interesting.
Studies of real-world passwords and PINS
PIN studyBruce Schneier wrote about a study of real-world passwords chosen by MySpace users. Distributions of lengths, character mixes, especially common passwords.
An excellent PIN analysis studied a collection of almost 3.4 million user-selected four-digit PINs and found that:
-
Nearly 11% were
1234, over 6% were1111, and nearly 2% were0000. -
If you try guessing just the top 5 most popular you
will get over 20%:
1234at 10.713%,1111at 6.016%,0000at 1.881%,1212at 1.197%, and7777at 0.745% add up to 20.552% out of all 10,000 possible 4-digit PINs in the collection. -
Many are effectively just two-digit PINs.
Repeated couplets such as
7878or1414account for 17.8% of the collection. -
Many people use memorable years,
or dates such as birthdays in
MMDDorDDMMformat, or life events inMMYY. Those formats greatly constrain the set of possible choices. -
Numerical runs like
2345and9876are very popular, as is the straight-line keypad sequence2580. -
Even numbers are a little more popular, so
2468is used more often than1357.
Researchers at Microsoft and Carleton University did a
nice study of how people use passwords,
"An Administrator's Guide to Internet Password Research".
See their
presentation
and read their
paper.
They conclude that password strength meters and most
suggestions for constructing strong passwords are
almost completely useless.
An important conclusion is that people
usually put accounts into different categories based on
the impact of account compromise, and that's a good thing.
Use silly passwords like literal "password"
and "123456"
for silly situations like the magazine or newspaper that
requires you to create an account to view their web site.
Just don't use the same password for accounts in different
sensitivity categories.
Mandatory Password Changes are Harmful
The Chief Technologist for the U.S. Federal Trade Commission wrote about how mandatory password changes are harmful. She cited a 2009 U.S. NIST publication "Guide to Enterprise Password Management" (SP 800-118), a 2009–2010 University of North Carolina study of password expiration, "The Security of Modern Password Expiration: An Algorithmic Framework and Empirical Analysis", a 2013 Carnegie Mellon University study "Measuring Password Guessability for an Entire University", a 2015 Carleton University study, "Quantifying the Security Advantage of Password Expiration Policies". These studies discovered that policies that enforce password change lead to weaker passwords. Password change reduces the impact of a successful password-guessing attack, but it makes such an attack more likely to succeed. NIST wrote (and has since retired) a draft document, SP 800-118, Guide to Enterprise Password Management, criticizing passwords for the small amount of security provided given the level of frustration they cause.
The physical world analogy would be an airbag system for cars that made crashes more likely to happen.
Old U.S. Government Requirements are Useless
U.S. NIST published SP 800-63-3, "Digital Identity Guidelines", in which they made three points:
Password complexity rules are harmful. When you require a mix of character types, people can't remember them or type them accurately. And, they don't really improve security against practical attacks. The author of the original NIST document insisting that they were a good idea has confessed that he didn't know what he was writing about.
Password expiration is harmful. See above, and also see this SANS Security Awareness Blog.
Use a password manager like KeePass.
In October 2016 the National Cyber Security Centre, part of GCHQ, the British parallel to the NSA, advised the public that a passphrase of three random words is better than trying to remember a complex jumbled of mixed characters. In August 2021 they repeated that advice.
Passwords
See these pages:
How Passwords Work How to Crack Passwords
Password Tools
If you have too many passwords on multiple systems, you need a secure means to store them on one system:
- Use KeePass. It works on Linux, Android, iOS, BSD, and Windows.
- LastPass runs on Mac, Linux, and Windows, with plugins for all the browsers.
- Password Gorilla is a secure graphical tool based on pwsafe for any Unix-like OS, plus Windows.
- Password Safe is a secure open-source tool which unfortunately is only available for Windows. Yubico has announced that their YubiKey two-factor authentication works with Password Safe.
KeePass LastPass Password Gorilla Password Safe
Also see the page on system configuration testing and auditing for several password cracking and password testing packages.
Use the pam_passwdqc or pam_pwquality PAM module for enforcing password quality on Linux, BSD, Solaris, HP-UX, and possibly elsewhere.
Two one-time password systems are S/KEY and OPIE ("One-Time Passwords in Everything"). OPIE is available to everyone from inner.net, and to .mil and .gov users only at ftp.nrl.navy.mil. S/KEY is available from ftp.cert.dfn.de.
In the late 1990s into the early 2000s S/KEY and specifically OPIE were used for remote authentication into servers. There were Linux PAM modules and everything. These days it makes far more sense to use cryptographic authentication into SSH for server administration.
But, S/KEY and OPIE are back. There are S/KEY libraries in various web APIs. With those, users can use S/KEY authentication into web-based front ends.
Good static passwords are essential. First, educate your users. Second, validate their actions with password cracking tests. See the system auditing page and especially the page on how to break passwords.
Kerberos
Get good documents from the source at MIT.
See my page on building an Active Directory server and integrating UNIX hosts into it. "Active Directory" is really just Microsoft's term for their bundle of DNS, LDAP, and Kerberos service onto a single host.
Note very carefully that Microsoft ships something that they label as "Kerberos", although it does not follow the open standard, and Microsoft considers their alterations to be proprietary.
Handheld Password Tokens
See a list of technologies and vendors at the Wikipedia page, or here are some:
- Aladdin Knowledge Systems
- Chrysalis ITS
- CRYPTOCard +1-800-307-7042
- Digital Pathways, Inc., +1-415-964-0707
- Entrust
- Gemalto
- iButton
- Keyware Technologies, Inc.
- RSA SecurID
- Secure Computing Corporation, +1-612-628-2700
- VASCO Data Security, +1-630-932-8844
- Verisign
Biometric Authentication
Fingerprints
Fingerprint readers are weaker than expected.
Yes, there have been
demonstrations of stolen and fake fingerprints
since the early 2000s.
More recent work has shown that you can find "MasterPrints",
synthetic (or real) partial fingerprints that happen to
match one or more of the stored templates for significant
fractions of users on a system.
Unveiling Intra-Person Fingerprint Similarity Via Deep Contrastive Learning
MasterPrint: Exploring the Vulnerability of Partial
Fingerprint-based Authentication Systems
"That Fingerprint Sensor on Your Phone Is Not
as Safe as You Think", New York Times
Fingerprints are not as reliable as we think.
At the very least, they need to be interpreted by a human.
"Fingerprinting's Reliability Draws Growing
Court Challenges",
New York Times
"Study questions reliability of fingerprint evidence"
The Guardian
"Accuracy and reliability of forensic
latent fingerprint decisions",
Proceedings of the National Academy of Sciences
"Effects of Human Factors on the Accuracy
of Fingerprint Analysis",
National Institute of Justice,
U.S. Department of Justice
Hand Shape
A number of companies have hand geometry systems,
it looks like Honeywell bought Schlage and Ingersoll Rand's
product lines.
Honeywell — HandKey
Voice
Several companies market voice authentication systems.
That is, authentication, deciding who the speaker
is, and not recognition, deciding what the speaker is saying.
Vendors include:
Nice
Nuance
Microsoft
VoiceVault
Blood vessel pattern recognition —
"The technology has been more widely accepted than fingerprinting in Asia mainly for cultural reasons", says Michelle Shen of ePolymath Consulting in Toronto. "In Japan, they are very concerned about hygiene. They're reluctant with fingerprinting because they have to touch the sensor." (quoted in Technology Review, Dec 2003 / Jan 2004, pg 22).
Get hardware from Techsphere of Seoul, South Korea, distributed by Identica, of Toronto, Canada. It's in use at the Toronto and Ottawa airports to authenticate ground crew, who often have dirty hands that don't work with fingerprinting.
Hitachi is working on this. "Finger vein authentication, introduced widely by Japanese banks in the last two years [2006-2008], is claimed to be the fastest and most secure biometric method" because blood vessels are invisible to the eye, extremely difficult to forge and simulate.
It uses near-IR absorption by hemoglobin. Fujitsu uses a similar approach but on a palm scanner rather than a fingertip, and its system has been installed at Carolina HealthCare System in Charlotte NC. See the story in the London Times.
Bionics Co., Ltd. is also working on the technology.
M2sys has published a case study of their system.
Buttock Pressure Map (yes, really)
A group at Purdue was working on this several years ago. A friend worked in that lab and was looking for test subjects. Here are my buttock pressure maps! The one at left is when sitting upright, the one at right is when intentionally slouching and leaning to one side as directed. They were doing pose recognition, not authentication.
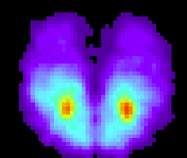
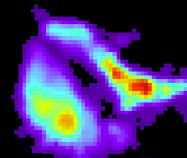
Some ten years later, a group at the Advanced Institute of Industrial Technology in Tokyo was working on a project to put 360 pressure sensors in the bucket seat of a car, claiming 98% accuracy in allowing only recognized people to start the car. See their presentation, and also see descriptions in Mobile Magazine, TechCrunch, and Wall Street Journal.
It could be worse. A research group at Stanford University, Seoul Song Do Hospital, Case Western Reserve University, Leiden University, Pohang University, the Catholic University of Korea, and Salesforce Research developed a health-monitoring toilet with biometric user recognition.
Comparing Biometric Methods
Here's a table from "Beyond Fingerprinting", Anil K Jain and Sharath Pankanti, Scientific American Sep 2008 pp 78-81, drawing from US NIST studies. They bring up an issue I hadn't seen before, technology will be less likely to be used if it is unsuitable as evidence in a court of law. Because iris recognition is based on complicated statistical analysis of subtle image features, "no known human experts can determine whether or not two iris images match. Hence, the data are unsuitable for evidence in a court of law."
| Measurement | Fingerprint | Face | Iris | Voice |
| Distinctiveness | High | Low | High | Low |
| Permanence | High | Medium | High | Low |
| How well trait can be sensed | Medium | High | Medium | Medium |
| Speed and cost efficiency of system | High | Low | High | Low |
| Willingness of people to have trait used | Medium | High | Low | High |
| Difficulty of spoofing the trait | High | Low | High | Low |
| False rejection rate | 0.4% | 1.0—2.5% | 1.1—1.4% | 5—10% |
| False acceptance rate | 0.1% | 0.1% | 0.1% | 2—5% |
Body Shape and Motion
The authors of "FreeSense: Indoor Human Identification with WiFi Signals" worked to identify individuals based on the ways that body shape and motion interact with indoor WiFi signals. They get about 90% accuracy with single-digit numbers of users. They were looking to solve the problem of distinguishing between 2 to 6 family members in a 6×5 meter "smart home environment". I had a hard time getting past the idea of to 6 people living in a 6×5 meter space, and how they extended their experiment to 9 people. The research was done at Northwestern Polytechnic University in Xi'an, People's Republic of China, where things are packed tighter than I'm used to. Anyway, they got about 94.5% accuracy with just 2 people, down to 88.9% with 6 and 75.5% with 9.
DNA
DNA evidence is not infallible. The assumption that DNA evidence always led to perfect decisions began to be questioned starting around 2015. See the coverage by PBS Frontline, The Atlantic, New Scientist, Science and Justice, and the Pittsburgh Post-Gazette.
But meanwhile, FBI and local law enforcement are trying to force private companies to archive genetic data.
Active Authentication
DARPA is running an Active Authentication project. They describe this work as:
The current standard method for validating a user's identity for authentication on an information system requires humans to do something that is inherently unnatural: create, remember, and manage long, complex passwords. Moreover, as long as the session remains active, typical systems incorporate no mechanisms to verify that the user originally authenticated is the user still in control of the keyboard. Thus unauthorized individuals may improperly obtain extended access to information system resources if a password is compromised or if a user does not exercise adequate vigilance after initially authenticating at the console.
The Active Authentication program seeks to address this problem by developing novel ways of validating the identity of the person at the console that focus on the unique aspects of the individual through the use of software based biometrics. Biometrics are defined as the characteristics used to uniquely recognize humans based on one or more intrinsic physical or behavioral traits. This program focuses on the behavioral traits that can be observed through how we interact with the world. Just as when you touch something your finger you leave behind a fingerprint, when you interact with technology you do so in a pattern based on how your mind processes information, leaving behind a "cognitive fingerprint."
The first phase of the program will focus on researching biometrics that do not require the installation of additional hardware sensors, rather the program will look for research on biometrics that can be captured through the technology we already use looking for aspects of this "cognitive fingerprint." These could include, for example, how the user handles the mouse and how the user crafts written language in an e-mail or document. A heavy emphasis will be placed on validating any potential new biometrics with empirical tests to ensure they would be effective in large scale deployments.
When Apple released their iPhone 5s with a fingerprint scanner they seemed to be working on this technology. A New Yorker story reported that in the week before the iPhone 5s release, Apple was awarded a patent for gesture based authentication.
Researchers have found that they could identify drivers based on how they use the controls of a vehicle. Read the Wired overview or the researchers' paper "Automobile Driver Fingerprinting".
Three researchers at the University of Padova in Italy have reported something similar to active authentication, as they are using mouse movement timing and patterns assess the confidence with which questions are answered. However, I think this is more of a method to tell how well a would-be identity thief has done their research. See: "The detection of faked identity using unexpected questions and mouse dynamics", PLOS One, 18 May 2017, https://doi.org/10.1371/journal.pone.0177851, and a short Science article describing the research.
Protect Sysadmin Authentication With sudo
Don't just hand out the system administrator's password!
Allow certain users to run only certain commands with sysadmin
privileges, with the
sudo tool.
TCP Wrappers and xinetd for
Host Authentication
TCP Wrapper and xinetd are weak, as they trust DNS, but they can do double DNS lookups and require consistency. Xinetd gives you finer control over access such as time-sensitive access rules, limitations on maximum simultaneous connections, throttling connection rates, and more. To be honest, these won't keep the bad guys out, and you will realize what a sloppy and imcomplete job many places do with the PTR records.
Also, with systemd replacing and modifying much of the Linux boot and service control mechanisms, xinetd seems to have been retired from Linux.
Some organizations use TCP Wrapper for warning and explanatory banners for compliance, and do access control in service-specific ways.
Software Authentication/Piracy
Software piracy (kinda) falls under authentication. Authenticate your software, make sure it's legitimate.
Why audit yourself? If your site has pirated software, you may incur huge fines. Disgruntled employees will turn you in for rewards from SPA and BSA (Software Publishers Association and Business Software Alliance), who shows up with federal agents and search warrants. Fines in the $100,000-200,000 range are common, and can go into the millions. Autodesk, maker of AutoCAD, recovered more than US$ 35 million from North American copyright infringers in 1989-1999 (SC Magazine, April 1999, pg 18). The SPAudit tool is available for free. It audits what software is installed where, and also inventories hardware and system boot files.