How to Copy DVDs
DVD Copying Using Free Software on Free Operating Systems
We want to learn how to create a copy of a DVD that you already own. Yes, legally own, of course. Use this information responsibly. As with almost any form of knowledge, like "Hydrogen burns in the presence of oxygen!", it could be used to do something that might be illegal where you live.
Maybe you are going on a business trip and you would like to take along a DVD that you own. But you don't want to run the risk of forgetting it and leaving it in the DVD player in the hotel room, losing your only copy of what might have been difficult to find.
For example, the legendarily rare director's cut of Dünyayı Kurtaran Adam.
In recent years it has become quite common to use a video transfer service to preserve old VHS tapes on DVD discs. You can easily use a VHS to DVD converter or a digital capture device to preserve VHS tapes digitally.
Background — CSS, DeCSS, and libdvdcss
Almost all commercially produced DVDs use the Content Scramble System or CSS. It is a rather weak stream cipher system using a 40-bit key. A 40-bit keyspace is not all that large to start with, and the implementation makes the system even weaker by only using a much smaller subset of that keyspace. 450 MHz x86 processors are adequate for a brute force attack requiring only minutes.
To briefly explain the CSS architecture, a set of player keys is known to DVD drive manufacturers and, no surprise, also known to others.
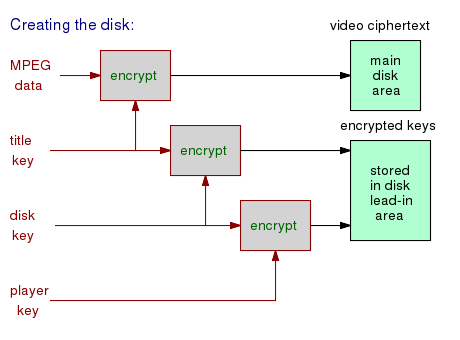
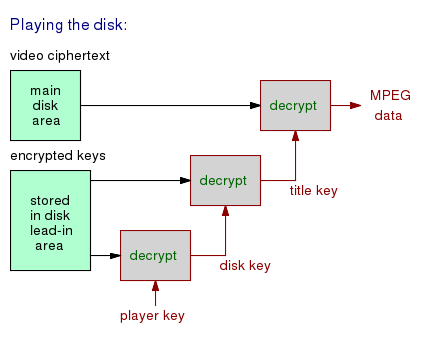
The lead-in area of the DVD has a disk key, and there will be at least one title key for the encrypted video file itself. Both the disk key and title keys are stored in ciphertext form. The title key is encrypted with the disk key, and the disk key is encrypted with the player key.

Do not look at these colors!
This gaudy "Free Speech Flag" embodies
a 16-byte number that we are not supposed to know
in the hexadecimal (R,G,B) values of
its five stripes followed by the byte 0xc0.
The disk and title keys are just five bytes long, 40 bits. The player keys are six bytes long, and are considered as trade secrets. Lawyers can insist on strange things that make no sense. See, for example, the AACS encryption key controversy and the strange legal concept that somehow there are numbers that are illegal for you to know or utter. There is a haiku description of the CSS algorithm and its reversal that reveals the use of these keys and even the value of one.
The DeCSS algorithm is based on a reverse engineered player key. If you accept the premise that laws can make it illegal to know certain numbers, then DeCSS should not be used as it's based on that forbidden knowledge.
An alternative is the libdvdcss library, which generates some possible player keys and then, if necessary, launches a brute force search of the very limited key space. It is available for Linux, BSD, Solaris, MacOS X, BeOS, and even Windows.
OK, That's More Than Enough Background, How Do I Copy a DVD?
You could just fire up K3b and select Copy a DVD from its menu — and that might work for you. It works in those cases where the libdvdcss library can quickly guess a working player key, and that seems to be well over 90% of the time! But if libdvdcss can't guess the key, K3b doesn't seem to allow it the chance to launch a brute force attack.
The tool of choice is
dvdbackup.
Use
dvdbackup
to copy the file system of the DVD onto
your file system, and then use
K3b
to burn the resulting directory structure to a DVD.
Simply put the DVD in the drive and call
dvdbackup.
The -M option, for "mirror", does just that — it
creates a mirror or copy of the DVD file system structure
in the current working directory.
It creates a subdirectory, the title as found on the DVD.
Under there is the subdirectory VIDEO_TS
that must exist on a valid video DVD.
If it reports that it can't open the default device
/dev/dvd, tell it where the device is with
something like
-i /dev/sr0
on Linux or
-i /dev/cd0
on FreeBSD or
-i /dev/cd0c
on OpenBSD.
You may also need to add
-o .
to explicitly tell it to put the result in
the current directory.
% mkdir ~/work-area
% cd ~/work-area
% dvdbackup -i /dev/sr0 -M -o .
[ ... much output and some time ... ]
% tree ~/work-area
~/work-area
`-- DÜNYAYI_KURTARAN_ADAM
`-- VIDEO_TS
|-- VIDEO_TS.BUP
|-- VIDEO_TS.IFO
|-- VIDEO_TS.VOB
|-- VTS_01_0.BUP
|-- VTS_01_0.IFO
|-- VTS_01_0.VOB
|-- VTS_01_1.VOB
|-- VTS_01_2.VOB
|-- VTS_01_3.VOB
|-- VTS_01_4.VOB
|-- VTS_02_0.BUP
|-- VTS_02_0.IFO
|-- VTS_02_0.VOB
|-- VTS_02_1.VOB
|-- VTS_03_0.BUP
|-- VTS_03_0.IFO
|-- VTS_03_0.VOB
|-- VTS_03_1.VOB
[ ... and so on, as needed ... ]
Installing the Needed Software
Your operating system distribution may have its software packaged in such a way that it's fairly simple to add what you need:
-
Mageia Linux
—
# yum install dvdbackup libdvdcss2 k3b
-
CentOS and Red Hat Linux
—
First, add the RPMforge repository.
On older systems you would add the below lines to
the file
/etc/yum.conf, but on newer systems add it as a new file in the directory/etc/yum.repos.d, giving it a meaningful name likerpmforge.repo:### RPMforge Repository for Red Hat Enterprise 5 - dag - http://rpmforge.net/ [rpmforge] name = Red Hat Enterprise $releasever - RPMforge.net - dag baseurl = http://apt.sw.be/redhat/el5/en/$basearch/rpmforge mirrorlist = http://apt.sw.be/redhat/el5/en/mirrors-rpmforge enabled = 1 protect = 0 gpgkey = file:///etc/pki/rpm-gpg/RPM-GPG-KEY-rpmforge-dag gpgcheck = 1
With that in place, just run this command:
# yum install dvdbackup libdvdcss k3b
-
Ubuntu Linux
—
% sudo apt-get install dvdbackup libdvdread3-dev libdvdcss2 k3b
-
FreeBSD
—
# pkg install dvdbackup libdvdcss k3b
-
OpenBSD
—
# pkg_add dvdbackup libdvdcss k3b
Amazon
ASIN: B0B22TWT59
Amazon
ASIN: B01BO63KV4
You can always download the source code for libdvdcss, dvdbackup, and K3b and build them from source. Build libdvdcss first, so the other components can use it.
Error Messages — Don't Panic!
Expect to see some error messages, but then expect the automated cryptanalysis to find the needed keys:
% time dvdbackup -M libdvdread: Using libdvdcss version 1.2.10 for DVD access libdvdread: Attempting to retrieve all CSS keys libdvdread: This can take a _long_ time, please be patient libdvdread: Get key for /VIDEO_TS/VIDEO_TS.VOB at 0x000001a0 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_01_0.VOB at 0x00005a20 libdvdread: Elapsed time 3 libdvdread: Get key for /VIDEO_TS/VTS_01_1.VOB at 0x00006c40 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_02_0.VOB at 0x001a0d40 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_02_1.VOB at 0x001a0d60 libdvdread: Error cracking CSS key for /VIDEO_TS/VTS_02_1.VOB (0x001a0d60)!! libdvdread: Elapsed time 9 libdvdread: Get key for /VIDEO_TS/VTS_03_0.VOB at 0x001ab560 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_03_1.VOB at 0x001ab580 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_04_0.VOB at 0x001b8820 libdvdread: Elapsed time 1 libdvdread: Get key for /VIDEO_TS/VTS_04_1.VOB at 0x001be5a0 libdvdread: Elapsed time 9 libdvdread: Get key for /VIDEO_TS/VTS_03_0.VOB at 0x001ab560 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_03_1.VOB at 0x001ab580 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_04_0.VOB at 0x001b8820 libdvdread: Elapsed time 1 libdvdread: Get key for /VIDEO_TS/VTS_04_1.VOB at 0x001be5a0 libdvdread: Error cracking CSS key for /VIDEO_TS/VTS_04_1.VOB (0x001be5a0)!! libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_05_0.VOB at 0x001be6e0 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_05_1.VOB at 0x001c6420 libdvdread: Error cracking CSS key for /VIDEO_TS/VTS_05_1.VOB (0x001c6420)!! libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_06_0.VOB at 0x001c6560 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_06_1.VOB at 0x001c9280 libdvdread: Error cracking CSS key for /VIDEO_TS/VTS_06_1.VOB (0x001c9280)!! [ ... and so on ... ] libdvdread: Get key for /VIDEO_TS/VTS_18_0.VOB at 0x0035d240 libdvdread: Elapsed time 0 libdvdread: Get key for /VIDEO_TS/VTS_18_1.VOB at 0x0035d260 libdvdread: Error cracking CSS key for /VIDEO_TS/VTS_18_1.VOB (0x0035d260)!! libdvdread: Elapsed time 109 libdvdread: Found 18 VTS's libdvdread: Elapsed time 662 180.839u 103.750s 34:32.04 13.7% 0+0k 44768192+16338792io 0pf+0w
In that specific run of dvdbackup, 10-15 minutes was required to recover all the keys and the remaining 20-25 minutes for the data transfer of about 7.8 GB. The result played just fine.
I think that what we see in the output are warnings that the initial and fairly trivial attempt to guess a file's key failed, and then it was found after some automated cryptanalysis requiring the reported number of seconds.
You may not notice this, but one result of this process
is a directory ~/.dvdcss/TITLE
containing a set of files.
Each file's name comes from the hexadecimal ID,
and it contains the key for that file.
Later runs of a libdvdcss program could simply read
and use those keys.
The last component reported for that above example,
is the VOB (Video OBject) container file VTS_18_1.VOB,
associated with hexadecimal ID 0x0035d260.
We can see what its encryption key was with the following:
% cat ~/.dvdcss/DÜNYAYI_KURTARAN_ADAM/000035d240 ce:72:42:2c:f9
Some DVDs use the same key for every file, some pick a new key for every two or three files, some have a unique key for each file. In many cases the keys differ by only a single byte, possibly just incrementing from one to the next.
Here are the results you're looking for, the data structure to be burned onto a DVD:
% ls -shR ~/work-area DÜNYAYI_KURTARAN_ADAM: total 4.0K 4.0K VIDEO_TS/ DÜNYAYI_KURTARAN_ADAM/VIDEO_TS: total 7.8G 28K VIDEO_TS.BUP 472K VTS_04_1.VOB 20K VTS_10_0.BUP 20K VTS_15_0.IFO 28K VIDEO_TS.IFO 20K VTS_05_0.BUP 20K VTS_10_0.IFO 33M VTS_15_0.VOB 45M VIDEO_TS.VOB 20K VTS_05_0.IFO 18M VTS_10_0.VOB 472K VTS_15_1.VOB 76K VTS_01_0.BUP 63M VTS_05_0.VOB 472K VTS_10_1.VOB 20K VTS_16_0.BUP 76K VTS_01_0.IFO 472K VTS_05_1.VOB 20K VTS_11_0.BUP 20K VTS_16_0.IFO 9.1M VTS_01_0.VOB 20K VTS_06_0.BUP 20K VTS_11_0.IFO 27M VTS_16_0.VOB 1.1G VTS_01_1.VOB 20K VTS_06_0.IFO 19M VTS_11_0.VOB 472K VTS_16_1.VOB 1.1G VTS_01_2.VOB 23M VTS_06_0.VOB 472K VTS_11_1.VOB 72K VTS_17_0.BUP 1.1G VTS_01_3.VOB 472K VTS_06_1.VOB 20K VTS_12_0.BUP 72K VTS_17_0.IFO 209M VTS_01_4.VOB 20K VTS_07_0.BUP 20K VTS_12_0.IFO 900K VTS_17_0.VOB 20K VTS_02_0.BUP 20K VTS_07_0.IFO 33M VTS_12_0.VOB 1.1G VTS_17_1.VOB 20K VTS_02_0.IFO 33M VTS_07_0.VOB 472K VTS_12_1.VOB 1.1G VTS_17_2.VOB 32K VTS_02_0.VOB 472K VTS_07_1.VOB 20K VTS_13_0.BUP 851M VTS_17_3.VOB 84M VTS_02_1.VOB 20K VTS_08_0.BUP 20K VTS_13_0.IFO 40K VTS_18_0.BUP 20K VTS_03_0.BUP 20K VTS_08_0.IFO 33M VTS_13_0.VOB 40K VTS_18_0.IFO 20K VTS_03_0.IFO 32M VTS_08_0.VOB 472K VTS_13_1.VOB 32K VTS_18_0.VOB 32K VTS_03_0.VOB 472K VTS_08_1.VOB 20K VTS_14_0.BUP 1.1G VTS_18_1.VOB 106M VTS_03_1.VOB 20K VTS_09_0.BUP 20K VTS_14_0.IFO 69M VTS_18_2.VOB 20K VTS_04_0.BUP 20K VTS_09_0.IFO 33M VTS_14_0.VOB 20K VTS_04_0.IFO 68M VTS_09_0.VOB 472K VTS_14_1.VOB 47M VTS_04_0.VOB 472K VTS_09_1.VOB 20K VTS_15_0.BUP
What About K3b Burning Errors?
For some reason, my old Pioneer DVR-110D DVD-RW drive had
no problems burning DVDs, including dual-layer DVDs,
but it failed with CD-R media some of the time.
I get a cryptic "Error code 254" reported from K3b,
which got it from cdrecord.
There's a simple workaround.
Maybe you want to use K3b to create the image.
Just create the image ISO file, and then burn it with
cdrecord after discovering the device name.
See how I use "4,0,0" in the command after discovering that
it is correct for my system — you will have to discover
your own device designation:
% cdrecord -scanbus scsibus1: 4,0,0 400) 'HP ' 'DVD Writer 1140r' 'FH25' Removable CD-ROM 4,1,0 401) * 4,2,0 402) * 4,3,0 403) * 4,4,0 404) * 4,5,0 405) * 4,6,0 406) * 4,7,0 407) * % cdrecord -v dev=4,0,0 whatever.iso
What's the real cause of the error?
I suppose I could look through the K3b diagnostic output
and see how it's misapplying cdrecord and then
go into the K3b setup and force it to work differently.
Or, just as easily if not more so, simply type the above
command...
The program will try to find a drive specific speed by
looking in /etc/wodim.conf,
the environment variable CDR_SPEED,
and then querying the drive, in that order.
If you have write errors and need to specify the speed,
do it like this:
% cdrecord -v speed=4 dev=1,1,0 whatever.iso
Sony DVDs, Extra Programs, and Root Kits
Sony is notorious for having inserted malicious root kits in CDs, see the excellent detailed analysis by Mark Russinovich for background on this. The Sony malware is secretly installed and run without your knowledge or consent, and a hacker could use it to gain and maintain access to your computer. If the Sony malware is installed on a Windows computer, attempts to remove it will damage or destroy your operating system.
The dvdbackup tool creates a subdirectory named
for the DVD volume name, and then it creates two subdirectories
within that, AUDIO_TS and VIDEO_TS.
The AUDIO_TS directory will be empty.
Some Sony DVDs, however, contain more.
Executable files in the root of the file system
and subdirectory JACKET_P
contain what appear to be three small MPEG files,
and files contains one executable.
This is the result of using the K3b "Copy Medium"
operation and simply creating an image file:
% /bin/ls -lF . JACKET_P files .: total 7776 dr-xr-xr-x 2 4294967295 4294967295 40 2010-10-26 18:15 AUDIO_TS/ -r-xr-xr-x 1 4294967295 4294967295 34 2006-03-29 12:58 AUTORUN.INF* dr-xr-xr-x 2 4294967295 4294967295 196 2010-10-26 18:16 JACKET_P/ -r-xr-xr-x 1 4294967295 4294967295 4171126 2009-08-20 20:41 MAC_clickme* -r-xr-xr-x 1 4294967295 4294967295 3775838 2009-08-19 16:23 PC_clickme.exe* dr-xr-xr-x 2 4294967295 4294967295 5032 2010-10-26 18:24 VIDEO_TS/ dr-xr-xr-x 2 4294967295 4294967295 88 2010-08-12 20:52 files/ JACKET_P: total 26 -r-xr-xr-x 1 4294967295 4294967295 20480 2010-10-26 18:16 J00___5L.MP2* -r-xr-xr-x 1 4294967295 4294967295 4096 2010-10-26 18:16 J00___5M.MP2* -r-xr-xr-x 1 4294967295 4294967295 2048 2010-10-26 18:16 J00___5S.MP2* files: total 56 -r-xr-xr-x 1 4294967295 4294967295 57344 2001-05-02 22:57 go.exe* Those huge UID and GID values? 4294967295 = 2^32 - 1
Let's see what those extra files are:
% cat AUTORUN.INF [autorun] open = PC_Clickme.exe % cat -A AUTORUN.INF [autorun]^M$ open = PC_Clickme.exe^M$ % file MAC_clickme PC_clickme.exe JACKET_P/* files/* MAC_clickme: header for PowerPC PEF executable PC_clickme.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit JACKET_P/J00___5L.MP2: MPEG sequence, v2, program multiplex JACKET_P/J00___5M.MP2: MPEG sequence, v2, program multiplex JACKET_P/J00___5S.MP2: MPEG sequence, v2, program multiplex files/go.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
J00___5L.MP2 is 720x480 pixels,
J00___5M.MP2 is 176x112 pixels,
and
J00___5S.MP2 does not seem to contain video data.
As for the program PC_clickme.exe,
which is automatically run if your Windows OS honors
the AUTORUN.INF file,
it contains some code which modifies your registry.
Why does this program call
RegSetValueEx()
and
RegCreateKeyEx()?
% hexdump -C PC_clickme.exe | less [ ... many lines of output deleted ... ] 0001fd00 4a be 00 00 58 be 00 00 6a be 00 00 7c be 00 00 |J...X...j...|...| 0001fd10 8c be 00 00 00 00 00 00 75 01 47 65 74 4d 6f 64 |........u.GetMod| 0001fd20 75 6c 65 46 69 6c 65 4e 61 6d 65 41 00 00 a8 03 |uleFileNameA....| 0001fd30 5f 6c 63 6c 6f 73 65 00 aa 03 5f 6c 6c 73 65 65 |_lclose..._llsee| 0001fd40 6b 00 ab 03 5f 6c 6f 70 65 6e 00 00 ac 03 5f 6c |k..._lopen...._l| 0001fd50 72 65 61 64 00 00 ef 00 46 72 65 65 4c 69 62 72 |read....FreeLibr| 0001fd60 61 72 79 00 48 02 4c 6f 61 64 4c 69 62 72 61 72 |ary.H.LoadLibrar| 0001fd70 79 41 00 00 a9 03 5f 6c 63 72 65 61 74 00 c9 01 |yA...._lcreat...| 0001fd80 47 65 74 54 65 6d 70 46 69 6c 65 4e 61 6d 65 41 |GetTempFileNameA| 0001fd90 00 00 ad 03 5f 6c 77 72 69 74 65 00 be 03 6c 73 |..-._lwrite...ls| 0001fda0 74 72 6c 65 6e 41 00 00 49 03 53 6c 65 65 70 00 |trlenA..I.Sleep.| 0001fdb0 94 01 47 65 74 50 72 69 76 61 74 65 50 72 6f 66 |..GetPrivateProf| 0001fdc0 69 6c 65 53 74 72 69 6e 67 41 00 00 ad 01 47 65 |ileStringA..-.Ge| 0001fdd0 74 53 68 6f 72 74 50 61 74 68 4e 61 6d 65 41 00 |tShortPathNameA.| 0001fde0 c5 00 46 69 6e 64 43 6c 6f 73 65 00 c9 00 46 69 |..FindClose...Fi| 0001fdf0 6e 64 46 69 72 73 74 46 69 6c 65 41 00 00 77 01 |ndFirstFileA..w.| 0001fe00 47 65 74 4d 6f 64 75 6c 65 48 61 6e 64 6c 65 41 |GetModuleHandleA| 0001fe10 00 00 4b 45 52 4e 45 4c 33 32 2e 64 6c 6c 00 00 |..KERNEL32.dll..| 0001fe20 85 02 53 65 74 57 69 6e 64 6f 77 54 65 78 74 41 |..SetWindowTextA| 0001fe30 00 00 11 01 47 65 74 44 6c 67 49 74 65 6d 00 00 |....GetDlgItem..| 0001fe40 c6 00 45 6e 64 44 69 61 6c 6f 67 00 9e 00 44 69 |..EndDialog...Di| 0001fe50 61 6c 6f 67 42 6f 78 50 61 72 61 6d 41 00 a3 01 |alogBoxParamA...| 0001fe60 49 73 44 6c 67 42 75 74 74 6f 6e 43 68 65 63 6b |IsDlgButtonCheck| 0001fe70 65 64 00 00 bc 00 44 72 61 77 54 65 78 74 41 00 |ed....DrawTextA.| 0001fe80 91 02 53 68 6f 77 57 69 6e 64 6f 77 00 00 45 01 |..ShowWindow..E.| 0001fe90 47 65 74 50 61 72 65 6e 74 00 d5 02 77 73 70 72 |GetParent...wspr| 0001fea0 69 6e 74 66 41 00 a1 00 44 69 73 70 61 74 63 68 |intfA...Dispatch| 0001feb0 4d 65 73 73 61 67 65 41 00 00 a9 02 54 72 61 6e |MessageA....Tran| 0001fec0 73 6c 61 74 65 4d 65 73 73 61 67 65 00 00 ff 01 |slateMessage....| 0001fed0 50 65 65 6b 4d 65 73 73 61 67 65 41 00 00 21 01 |PeekMessageA..!.| 0001fee0 47 65 74 4b 65 79 53 74 61 74 65 00 8e 00 44 65 |GetKeyState...De| 0001fef0 66 57 69 6e 64 6f 77 50 72 6f 63 41 00 00 01 02 |fWindowProcA....| 0001ff00 50 6f 73 74 4d 65 73 73 61 67 65 41 00 00 29 02 |PostMessageA..).| 0001ff10 52 65 6c 65 61 73 65 44 43 00 0c 01 47 65 74 44 |ReleaseDC...GetD| 0001ff20 43 00 55 02 53 65 74 46 6f 63 75 73 00 00 56 02 |C.U.SetFocus..V.| 0001ff30 53 65 74 46 6f 72 65 67 72 6f 75 6e 64 57 69 6e |SetForegroundWin| 0001ff40 64 6f 77 00 99 00 44 65 73 74 72 6f 79 57 69 6e |dow...DestroyWin| 0001ff50 64 6f 77 00 de 01 4d 65 73 73 61 67 65 42 6f 78 |dow...MessageBox| 0001ff60 41 00 bd 01 4c 6f 61 64 49 63 6f 6e 41 00 cd 02 |A...LoadIconA...| 0001ff70 57 61 69 74 4d 65 73 73 61 67 65 00 60 00 43 72 |WaitMessage.`.Cr| 0001ff80 65 61 74 65 57 69 6e 64 6f 77 45 78 41 00 15 02 |eateWindowExA...| 0001ff90 52 65 67 69 73 74 65 72 43 6c 61 73 73 41 00 00 |RegisterClassA..| 0001ffa0 3a 02 53 65 6e 64 4d 65 73 73 61 67 65 41 00 00 |:.SendMessageA..| 0001ffb0 e3 00 46 69 6e 64 57 69 6e 64 6f 77 41 00 1b 00 |..FindWindowA...| 0001ffc0 43 61 6c 6c 57 69 6e 64 6f 77 50 72 6f 63 41 00 |CallWindowProcA.| 0001ffd0 eb 01 4d 6f 76 65 57 69 6e 64 6f 77 00 00 78 01 |..MoveWindow..x.| 0001ffe0 47 65 74 57 69 6e 64 6f 77 54 65 78 74 4c 65 6e |GetWindowTextLen| 0001fff0 67 74 68 41 00 00 f6 00 47 65 74 43 6c 61 73 73 |gthA....GetClass| 00020000 49 6e 66 6f 41 00 74 01 47 65 74 57 69 6e 64 6f |InfoA.t.GetWindo| 00020010 77 52 65 63 74 00 82 02 53 65 74 57 69 6e 64 6f |wRect...SetWindo| 00020020 77 50 6f 73 00 00 55 53 45 52 33 32 2e 64 6c 6c |wPos..USER32.dll| 00020030 00 00 0e 02 53 65 6c 65 63 74 4f 62 6a 65 63 74 |....SelectObject| 00020040 00 00 a5 01 47 65 74 53 74 6f 63 6b 4f 62 6a 65 |....GetStockObje| 00020050 63 74 00 00 f3 01 52 65 61 6c 69 7a 65 50 61 6c |ct....RealizePal| 00020060 65 74 74 65 00 00 0f 02 53 65 6c 65 63 74 50 61 |ette....SelectPa| 00020070 6c 65 74 74 65 00 6b 01 47 65 74 44 65 76 69 63 |lette.k.GetDevic| 00020080 65 43 61 70 73 00 45 00 43 72 65 61 74 65 50 61 |eCaps.E.CreatePa| 00020090 6c 65 74 74 65 00 8f 00 44 65 6c 65 74 65 4f 62 |lette...DeleteOb| 000200a0 6a 65 63 74 00 00 47 44 49 33 32 2e 64 6c 6c 00 |ject..GDI32.dll.| 000200b0 c1 02 73 74 72 6e 63 70 79 00 99 02 6d 65 6d 73 |..strncpy...mems| 000200c0 65 74 00 00 48 01 5f 6d 61 6b 65 70 61 74 68 00 |et..H._makepath.| 000200d0 b9 01 5f 73 70 6c 69 74 70 61 74 68 00 00 ac 00 |.._splitpath....| 000200e0 5f 63 68 64 69 72 00 00 a8 02 72 65 6d 6f 76 65 |_chdir....remove| 000200f0 00 00 3e 02 61 74 6f 6c 00 00 be 02 73 74 72 6c |..>.atol....strl| 00020100 65 6e 00 00 ba 02 73 74 72 63 70 79 00 00 4d 53 |en....strcpy..MS| 00020110 56 43 52 54 2e 64 6c 6c 00 00 5e 02 66 72 65 65 |VCRT.dll..^.free| 00020120 00 00 0f 01 5f 69 6e 69 74 74 65 72 6d 00 91 02 |...._initterm...| 00020130 6d 61 6c 6c 6f 63 00 00 9d 00 5f 61 64 6a 75 73 |malloc...._adjus| 00020140 74 5f 66 64 69 76 00 00 55 00 5f 5f 64 6c 6c 6f |t_fdiv..U.__dllo| 00020150 6e 65 78 69 74 00 86 01 5f 6f 6e 65 78 69 74 00 |nexit..._onexit.| 00020160 49 4d 4c 33 32 2e 64 6c 6c 00 44 49 52 41 50 49 |IML32.dll.DIRAPI| 00020170 2e 64 6c 6c 00 00 cb 01 47 65 74 54 65 6d 70 50 |.dll....GetTempP| 00020180 61 74 68 41 00 00 45 00 43 72 65 61 74 65 44 69 |athA..E.CreateDi| 00020190 72 65 63 74 6f 72 79 41 00 00 4d 00 43 72 65 61 |rectoryA..M.Crea| 000201a0 74 65 46 69 6c 65 41 00 ba 02 52 65 6d 6f 76 65 |teFileA...Remove| 000201b0 44 69 72 65 63 74 6f 72 79 41 00 00 d3 00 46 69 |DirectoryA....Fi| 000201c0 6e 64 4e 65 78 74 46 69 6c 65 41 00 7c 00 44 65 |ndNextFileA.|.De| 000201d0 6c 65 74 65 46 69 6c 65 41 00 2e 00 43 6c 6f 73 |leteFileA...Clos| 000201e0 65 48 61 6e 64 6c 65 00 b9 01 47 65 74 53 79 73 |eHandle...GetSys| 000201f0 74 65 6d 44 69 72 65 63 74 6f 72 79 41 00 98 01 |temDirectoryA...| 00020200 47 65 74 50 72 6f 63 41 64 64 72 65 73 73 00 00 |GetProcAddress..| 00020210 0a 03 53 65 74 45 72 72 6f 72 4d 6f 64 65 00 00 |..SetErrorMode..| 00020220 56 01 47 65 74 46 69 6c 65 41 74 74 72 69 62 75 |V.GetFileAttribu| 00020230 74 65 73 41 00 00 69 01 47 65 74 4c 61 73 74 45 |tesA..i.GetLastE| 00020240 72 72 6f 72 00 00 6f 6c 65 33 32 2e 64 6c 6c 00 |rror..ole32.dll.| 00020250 c9 01 52 65 67 43 6c 6f 73 65 4b 65 79 00 ec 01 |..RegCloseKey...| 00020260 52 65 67 51 75 65 72 79 56 61 6c 75 65 45 78 41 |RegQueryValueExA| 00020270 00 00 e2 01 52 65 67 4f 70 65 6e 4b 65 79 45 78 |....RegOpenKeyEx| 00020280 41 00 f9 01 52 65 67 53 65 74 56 61 6c 75 65 45 |A...RegSetValueE| 00020290 78 41 00 00 cd 01 52 65 67 43 72 65 61 74 65 4b |xA....RegCreateK| 000202a0 65 79 45 78 41 00 41 44 56 41 50 49 33 32 2e 64 |eyExA.ADVAPI32.d| 000202b0 6c 6c 00 00 56 45 52 53 49 4f 4e 2e 64 6c 6c 00 |ll..VERSION.dll.| 000202c0 0f 00 3f 3f 32 40 59 41 50 41 58 49 40 5a 00 00 |..??2@YAPAXI@Z..| 000202d0 10 00 3f 3f 33 40 59 41 58 50 41 58 40 5a 00 00 |..??3@YAXPAX@Z..| 000202e0 b6 02 73 74 72 63 61 74 00 00 b8 02 73 74 72 63 |..strcat....strc| 000202f0 6d 70 00 00 49 00 5f 5f 43 78 78 46 72 61 6d 65 |mp..I.__CxxFrame| 00020300 48 61 6e 64 6c 65 72 00 b2 02 73 70 72 69 6e 74 |Handler...sprint| 00020310 66 00 c8 02 73 74 72 74 6f 6c 00 00 00 00 00 00 |f...strtol......| 00020320 00 00 00 00 00 00 00 00 34 fc 3f 41 00 00 00 00 |........4.?A....| 00020330 32 c2 00 00 01 00 00 00 01 00 00 00 01 00 00 00 |2...............| 00020340 28 c2 00 00 2c c2 00 00 30 c2 00 00 f4 52 00 00 |(...,...0....R..| 00020350 3b c2 00 00 00 00 50 72 6f 6a 2e 64 6c 6c 00 50 |;.....Proj.dll.P| 00020360 72 6f 6a 65 63 74 6f 72 4d 61 69 6e 00 00 00 00 |rojectorMain....| 00020370 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| [ ... many lines of output deleted ... ]
I found that a copy of this DVD made with the K3b "Copy Medium" operation would not play in my Samsung DVD-1080P9.
However, a copy made by using dvdbackup and
then burning a DVD with just the full VIDEO_TS
and empty AUDIO_TS directories would
play just fine.
My conclusion: The added programs and/or the lack of some data not copied in the K3b "Copy Medium" operation make for unplayable copies.

