
CompTIA Security+ Guidance
CompTIA Security+ Compressed into Zen Koans
Here are my suggestions for preparing for the
CompTIA Security+ exam.
I have tried to compress my suggestions down as much
as possible.
Hopefully they can be succinct and thought-provoking
like koans.
Maybe the temple pictures can help.
How to prepare for, and pass, certification exams
Understand the test.
Realize that the test does not try to measure if
you are a skilled practitioner.
The test has to do with communication between
managers and technical experts.
It's a vocabulary test to see if you can use the right words
when one party in the conversation doesn't necessarily
know all that much about the topic.
Some very distinctive terms, phrases, and
sentences described below can help you easily
spot correct choices on the test.

The Exam as Ritual
I imagine that a safe at CompTIA headquarters contains a book made up of a few hundred sentences, plus "Memorize this table of TCP and UDP port numbers", plus "we assume you know these parts of Network+". If you could memorize that book of sentences, like memorizing some ritual, you would know the answers to almost all of the questions. I know the exact form of some of those sentences, and distinctive phrases out of others. For example:
Acceptable use policy is enforced by URL and content filtering.
Many are simple:
AES is the best symmetric cipher.
Kerberos is the best single-sign-on system.
Logs and audits enforce accountability.
Some have two parts.
Protect the keys with asymmetric cryptography,
protect the data with symmetric cryptography.
It can be helpful to know a little of the background:
Symmetric ciphers should be used on data. (Because they are efficient, and data can be large)
Asymmetric ciphers protect the negotiations and keys. (That is, they do the endpoint authentications and set up symmetric session keys)
CompTIA Security+ Philosophy
These aren't necessarily the answers themselves, but guidance for dealing with the exam questions.
A mile wide and an inch deep, go no deeper.
Pick the simple answer for the common case. No scenario is for you, it's for the mythical test-taker.
Reality helps with concepts, but not specifics.
He who says "At work we must do X and Y so that Z can then happen" has strayed from the path of wisdom.
He who says "I can imagine a scenario where X and then Y could lead to Z" has gone even further off the path.
Even a silly sounding policy is always correct.
Involve management.
Protocol analyzers have many important security uses.
Be able to put things into order.
"What is the first step in this process? And the last?"
"Which is the most intrusive vulnerability analysis? And the least?"
"Which is the most volatile forensic data? And the least?
Be able to put things into categories
within sets.
Detective, Preventative, Corrective
Technical, Management, Operational
Symmetric, Asymmetric
Encrypting, Encoding, Hashing
Authenticating, Authorizing, Auditing
and so on.
When you are told the name, job title, department, and the often-irrelevant current task of every player in a little story, read past those quickly. They're there to slow you down.
CompTIA Wants You To Know Some Specific Sayings
I don't know exactly what CompTIA means by some of these distinctive phrases. But that doesn't matter because all I need to know is that these are the right answers.
"Business Continuity" means "3-4 days after and continuing from there."
"Contingency Planning" is for one very specific problem.
"The first step in Disaster Recovery Planning is a Business Impact Analysis."
"Job rotation" is preventative.
"Enforced vacation" is detective.
"Job rotation" might have kept Nixon and Agnew in office.
Impersonation is when a person pretends to be another person.
Warm sites can start in under a week.
Hot sites are always ready right now, so they're expensive.
Both behavior-based and anomaly-based IDS must observe for a while to learn the local baseline. They mention "exceptions or broken protocol rules" when they're talking about anomaly-based.
Privilege escalation is used to mean two very different things, use the context to figure out which one they're talking about:
- During an annual review of user rights, you notice someone has accumulated privileges while rotating through jobs. There's no attack, but they no longer need some of those privileges.
- During an attack, the intruder is replaying captured privileges or running a buffer overflow to transition from low-privileges user to sysadmin.
When they ask "What would be the very best way...",
they are often implying
"...if expense and complexity don't matter."
For example: diesel generators, HSMs, Kerberos,
biometric door locks, and SELinux in full enforcing mode.
Kerberos and SELinux are free software, but complex to manage.
The others cost a lot of money.
Know Cryptography Fundamentals
CryptographyFlowcharts
If you can drawn your own versions of how some fundamental cryptographic operations work, you will easily answer many of the exam questions. If you can't, you're likely to fail the exam. Look at my diagrams, and draw your own. You need to know how all these work:
- Symmetric encryption for confidentiality
- Asymmetric encryption for confidentiality
- Asymmetric encryption for authentication
- Asymmetric encryption for confidentiality and authentication
- Digital signatures
- HMAC
Here's a SAML Picture
You need to know a little about SAML for Security+, here's how it works.
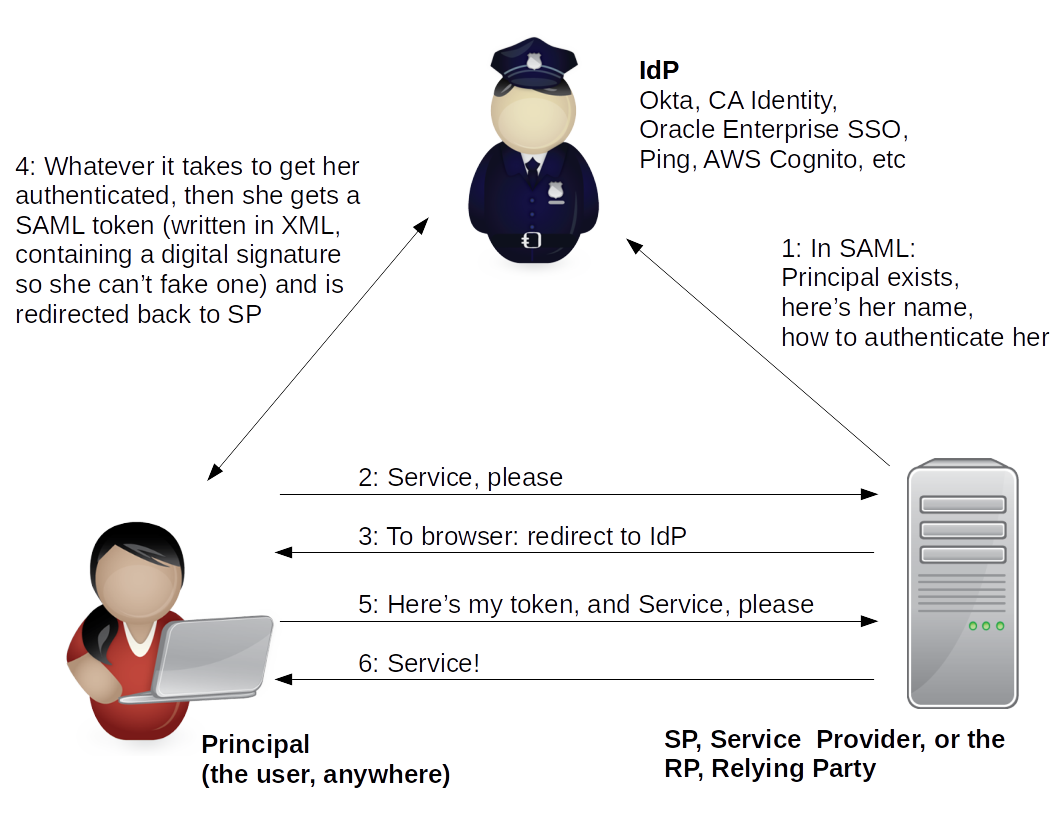
Shibboleth is based on SAML, it works the same way, but SAML is used by companies with for-profit identity providers. Shibboleth is much more about academia using it for themselves.
What Color Is The Sky in the CompTIA Universe?
CompTIA consistently insists that a number of things are not the way they are in the real world. Shrug and mark the correct answer.
All routers have ACLs and all are default deny. Always.
The entire Internet contains nothing but Windows desktops,
plus a few Windows servers.
Except for once in a while Linux appears out of the blue:
ssh / scp / sftp, root,
SELinux (a.k.a. NSA Security-Enhanced Linux),
/etc/passwd and /etc/shadow,
plus the above about file system tampering.
NetStumbler is the only way to discover WLANs,
and AirSnort is the only way to break WEP.
Role-Based Access Control is an easy hierarchical way to
administer authorizations.
(Because CompTIA thinks that Windows group policies
are real RBAC)
CompTIA Likes to Confuse You
Here are some confusingly similar or overlapping topics ideal for setting up tricky multiple-choice questions:
CompTIA uses the phrase Rule-Based Access Control just so they can confuse you about Role-Based Access Control, which is what the rest of the world means by RBAC.
OTP stands for both One-Time Password (at first login you must change it) and One-Time Pad (the only truly secure cipher). MAC stands for three very different security concepts.
| People in hats: | White | Grey | Black |
| Techniques in boxes: | White | Grey | Black (with Fuzzing) |
| IDS and anti-malware errors: | False Positive | False Negative |
| Biometric authentication errors: | False Acceptance | False Rejection |
| Behavior upon an error: | Fail Safe | Fail Open |
What do digital certificates contain?
server's public key, or
server's private key, or
CA's public key, or
CA's private key.
With lost phone questions, are we trying to track down and recover the hardware asset, or remotely wipe the data, or keep the finder from making calls on our bill? Or some combination of those goals?
This isn't trickiness, but many questions are effectively two or more questions in one. For example:
Julie, a left-handed Episcopalian network engineer
in the software development department, needs
to encrypt some large files containing sensitive
customer data in order to fulfill compliance
requirements.
Her manager is emphasizing the importance because
these are medical records.
What should she use?
RSA
AES
DES
ECC
Once you have waded through the intentionally distracting and time-wasting clutter, you have the real question: How to encrypt large data sets? First part: The general answer is Symmetric ciphers but that isn't a choice. Second part: Now you have to look through the list for examples of those: AES and DES. Third part: Realize that AES is (by far) the better choice.
What about a study book?
The least bad one is the CompTIA Security+ Study Guide: Exam SY0-601 by Sybex. It's based on CompTIA's material, but that means that it only tells you some of the truth. I haven't noticed anything in that book that contradicts what they want you to say on the test, but:
- Some material on the test is not covered in the book.
- Some material in the book is not included in the test.
So you will waste some time, energy, and memory on things you don't really need to know, and you won't have seen some of the topics you need to know. And this is the best book available...
What About Other On-Line Practice Exams?
How to prepare for, and pass, certification examsSee my page about preparing for certification exams for some suggestions and dire warnings about these.
Exam Versions
Be aware that CompTIA pretends that one major release of their exam is a long-term static document. They say that after over 3 years of the SY0-301 exam being the Security+ exam, in a form that never changed, the SY0-401 exam appeared and suddenly was the only form of the exam for the following four and a half years.
No. Not at all.
They release a major upgrade, such as SY0-301 to SY0-401, to SY0-501, every 3 to almost 5 years. But during that 3 to nearly 5 years of a given exam, it evolves through a series of entirely unannounced and unacknowledged updates.
My rant about how horribly bad the SY0-401 exam wasThese "mid-course adjustments" may be minor tweaks to what the exam covers, or they may be more significant. As a general rule, a given exam major release gets progressively worse during the time CompTIA says it's "the" current version.
SY0-501 was a much better exam than its predecessor, at least when it first came out.
See my detailed rant if you want to know just how bad the SY0-401 exam was. You had to memorize historical trivia that hadn't mattered for over two decades, and much of the rest of the exam required you to recite fiction.
Good luck!
Now you know a little more about how to think about the awful questions on this test.
You're on your way to making your own one-page crib sheet. The smaller your study guide or crib sheet becomes, the more you already know and the less you have to be reminded of.
Re-do the Short Quiz A versions to see how it's going. Then read sections of the textbook or look back through the acronyms or whatever as needed. When Short Quiz A becomes too easy, try Short Quiz B. Then "All Questions" for that domain.
Let us know how you did! Especially let us know if there were any surprises on the exam, any questions on topics we don't yet realize we need to cover.

