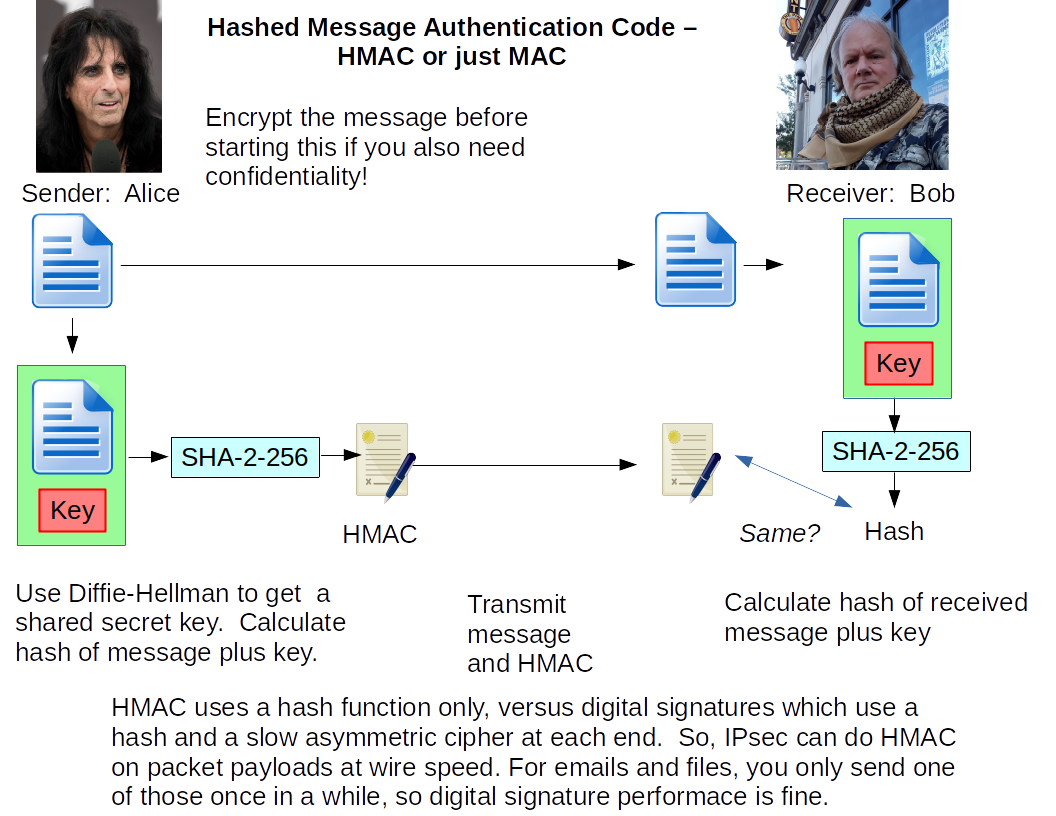
Know These!
Make sure that you can draw your own versions of these pictures.
Expect multiple questions about who uses which key first,
or which key last,
in these situations.
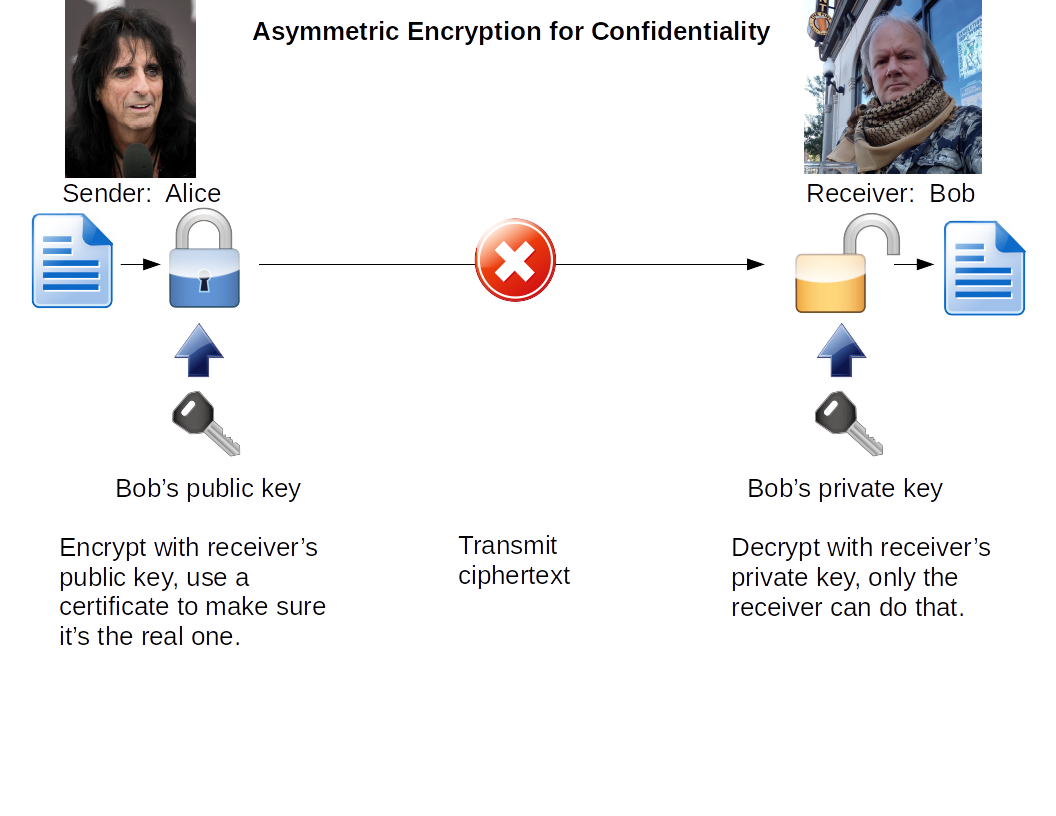
| Goal |
Sender uses |
Receiver uses |
| Confidentiality |
Receiver's public key |
Receiver's private key |
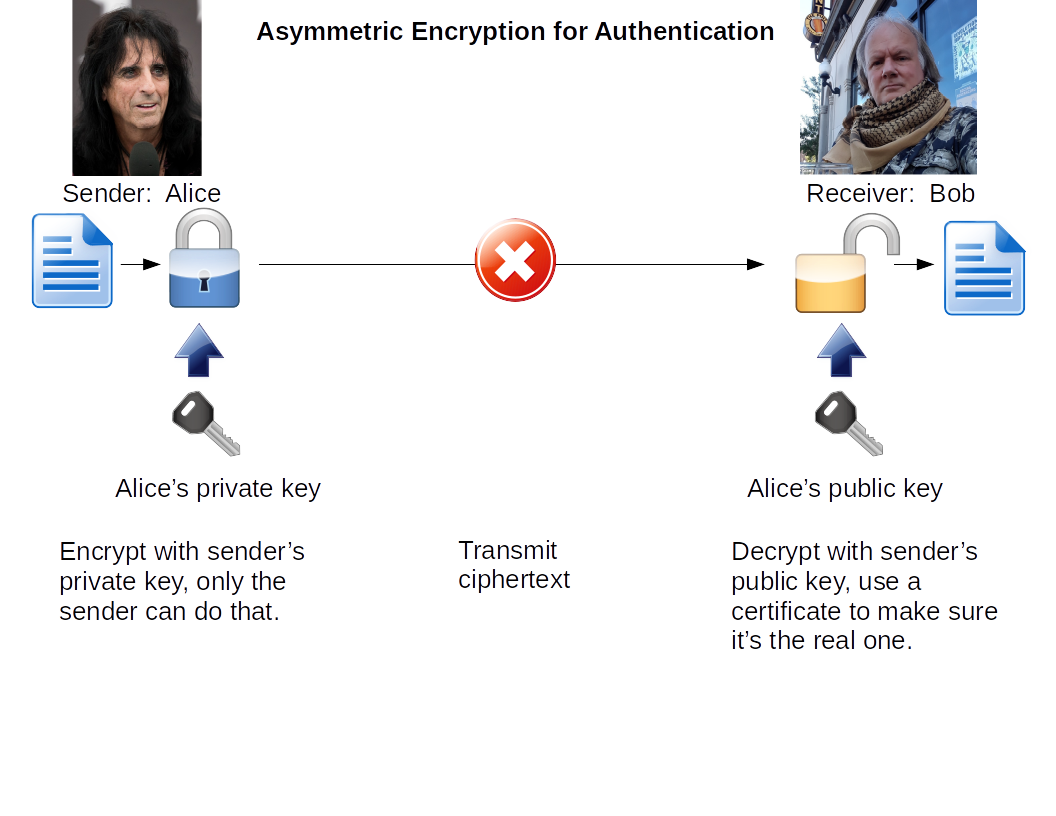
| Authentication |
Sender's private key |
Sender's public key |
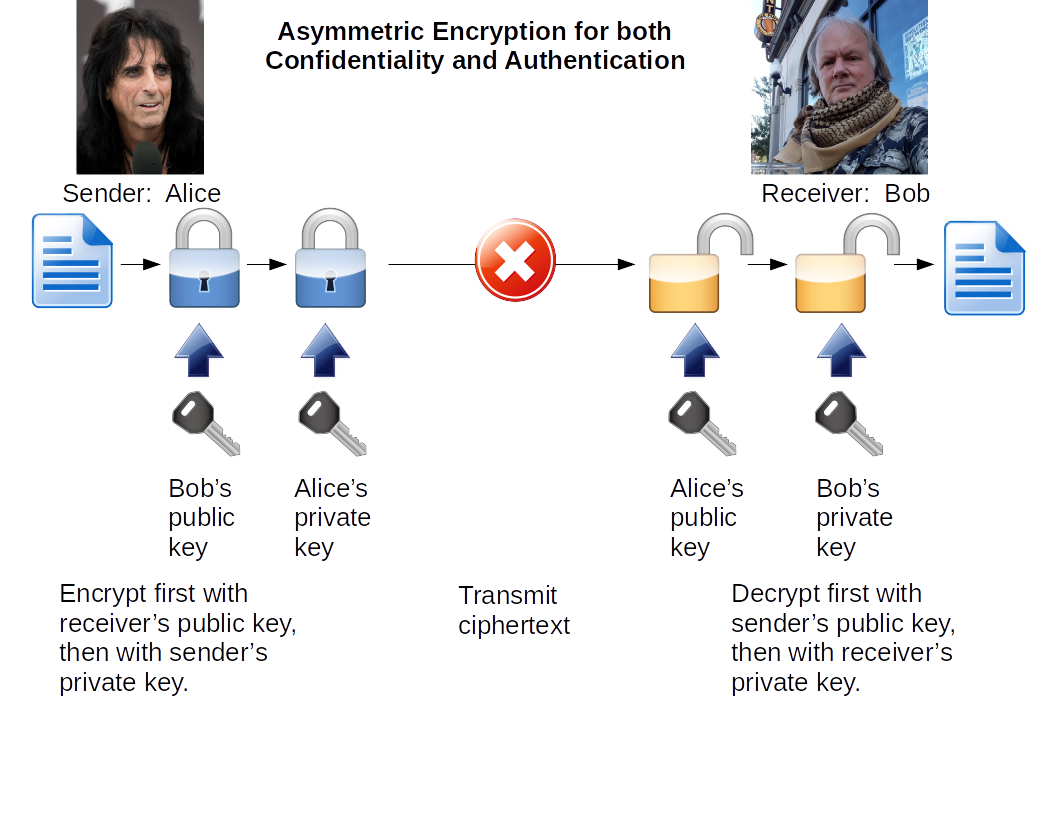
Confidentiality
& Authentication |
Receiver's public key
Sender's private key |
Sender's public key
Receiver's private key |
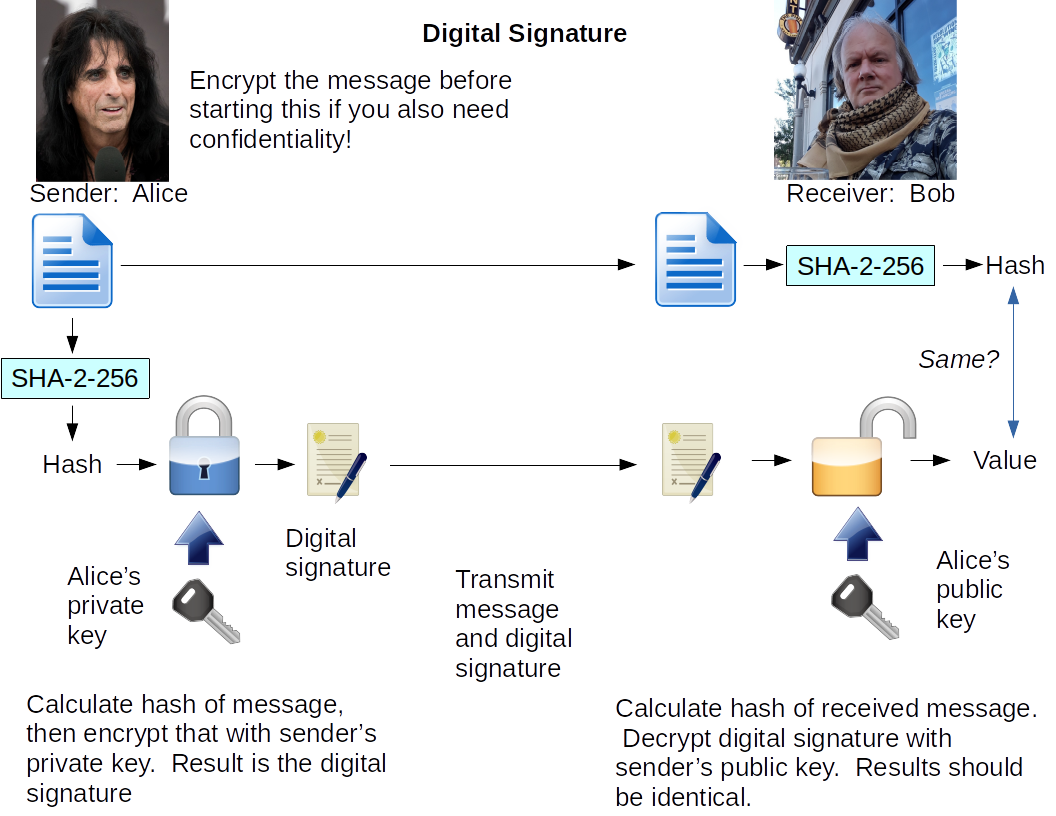
| Digital Signature |
Sender's private key |
Sender's public key |
| HMAC |
Shared secret key |
Shared secret key |
Use certificates (thus PKI) so you can trust the
validity of public keys.
Use Diffie-Hellman to negotiate a shared secret.
To the Cybersecurity Page