
Drawings
Proxy Encryption
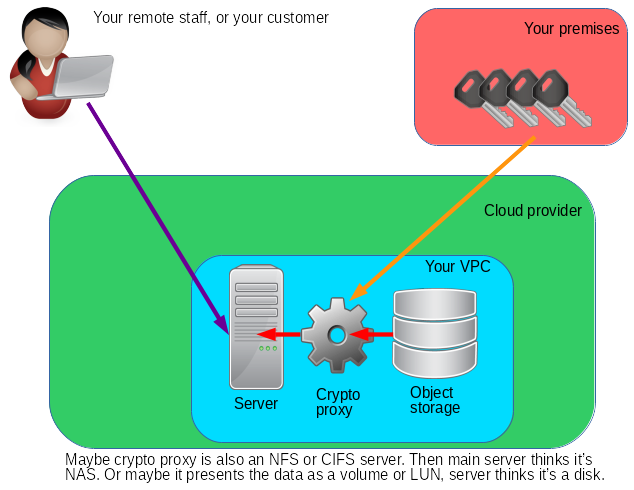
SDN or Software Defined Networking
This might be called NFV or Network Function Virtualization, but SDN is used more often.
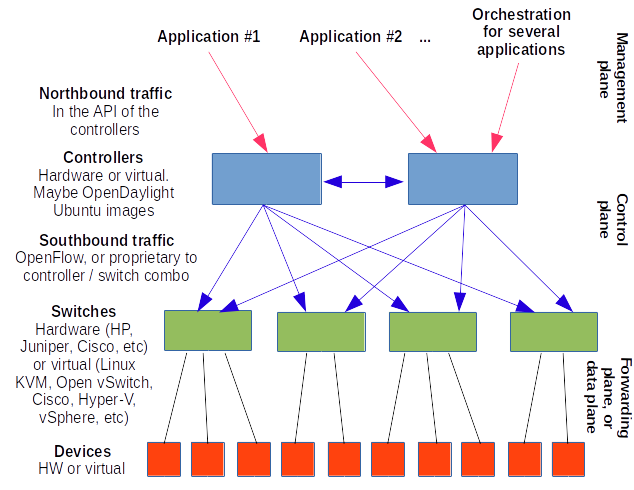
VPC or Virtual Private Cloud
SAML
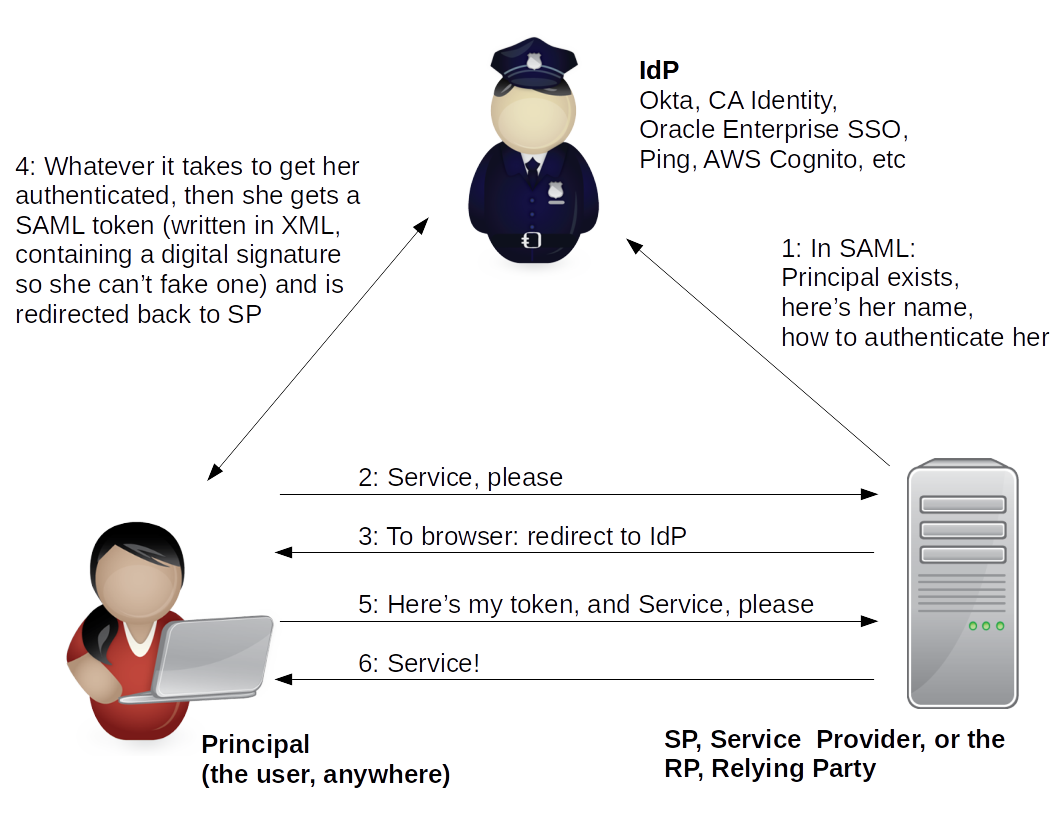
As an example of how these web authentication mechanisms can work in general, I get email from the U.S. Postal Service from time to time. They are not using SAML, but...
The email message directs me to:
https://informeddelivery.usps.com/box/pages/secure/DashboardAction_input?keyword=mail
I copy that and paste it into the Chrome location bar.
I am redirected from informeddelivery.usps.com to
reg.usps.com, asking for the LoginAction_input resource
with two variables set, app and
appURL:
https://reg.usps.com/entreg/LoginAction_input?app=RMIN&appURL=https%3A%2F%2Finformeddelivery.usps.com%2Fbox%2Fpages%2Fsecure%2FDashboardAction_input%3Fkeyword%3Dmail : / / / / / / ? =
Notice that the appURL variable is set to the
original URL, with the ":", "/", "?", and "=" characters
encoded as
%3A,
%2F,
%3F, and
%3D respectively.
That takes me to a page with forms to enter my user name and password. With those successfully submitted, that page redirects me to the original destination:
https://informeddelivery.usps.com/box/pages/secure/DashboardAction_input?keyword=mail