
CISSP Domain 5 — Identity and Access Management
Domain 5 — Identity and Access Management
Powerful system accounts are obvious targets:
root on UNIX-family,
Administrator on Windows.
Built-in Windows accounts
The final number is what matters.
SID: S-1-5-21domain-500
Name: Administrator
SID of *-500 is Local Administrator, regardless of
any renaming.
SID: S-1-5-21domain-501
Name: Guest
Should be disabled, or carefully monitored
SID: S-1-5-21domain-512
Name: Domain Admins
More powerful, like Administrator
across several machines simultaneously.
Biometric failure modes
You either know the exact passphrase or you don't. Or, you have the needed physical token or you don't. But with biometrics, the system always has to conclude "close enough". So, there will be errors. You must know them by two sets of names.
False Rejection or Type I: Failure to recognize the legitimate user.
False Acceptance or Type II: Erroneously allowing an imposter in.
Crossover Error Rate: You have adjusted the thresholds so the False Rejection and False Acceptance error rates are equal.
Identity Assurance
- IAL1: Attributes are self-asserted and should not be trusted.
- IAL2: Either remote or in-person identity proofing is required.
-
IAL3:
In-person identity proofing is required.
Identifying attributes must be verified by an
authorized Credential Service Provider or cSP.
- Authenticator Assurance Level or AAL: Refers to the authentication process
- Federation Assurance Level or FAL: Refers to the strength of an assertion in a federated environment
IAM Protocols for Federated Environments
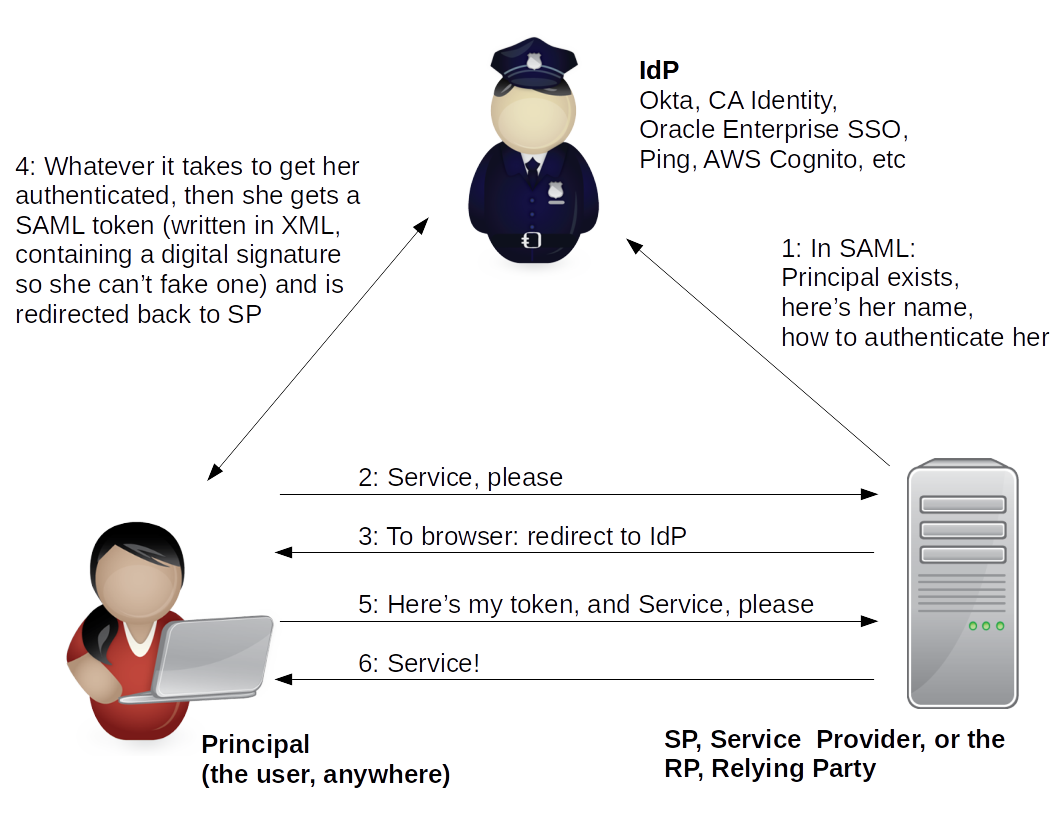
SAML defines an XML framework. It focuses on authentication (and some authorization).
Three roles:
Identity Provider or IdP
Service Provider or Relying Party
User or Principal
OAuth enables a 3rd-party application to obtain controlled access to an HTTP service. It focuses on authorization. This is what happens if you point your browser to Pinterest or Instagram, and that site offers the ability to sign in with your Google or Facebook credentials. Exam questions will probably focus on cases where social media is involved.
Four roles:
Resource owner
Resource server
Client application
Authorization server
Also know about OpenID and WS-Federation.
SAML and WS-Federation are more commonly used within an enterprise.
OAuth and OpenID are more commonly used across the Internet, between organizations.
As an example of how these web authentication mechanisms can work in general, I get email from the U.S. Postal Service from time to time. They are not using SAML, but...
The email message directs me to:
https://informeddelivery.usps.com/box/pages/secure/DashboardAction_input?keyword=mail
I copy that and paste it into the Chrome location bar.
I am redirected from informeddelivery.usps.com to
reg.usps.com, asking for the LoginAction_input resource
with two variables set, app and
appURL:
https://reg.usps.com/entreg/LoginAction_input?app=RMIN&appURL=https%3A%2F%2Finformeddelivery.usps.com%2Fbox%2Fpages%2Fsecure%2FDashboardAction_input%3Fkeyword%3Dmail : / / / / / / ? =
Notice that the appURL variable is set to the
original URL, with the ":", "/", "?", and "=" characters
encoded as
%3A,
%2F,
%3F, and
%3D respectively.
That takes me to a page with forms to enter my user name and password. With those successfully submitted, that page redirects me to the original destination:
https://informeddelivery.usps.com/box/pages/secure/DashboardAction_input?keyword=mail
Access Control Models
Know these:
Discretionary Access Control or DAC
Mandatory Access Control or MAC
Nondiscretionary Access Control or NDAC
(simply all except DAC)
Role-Based Access Control or RBAC
Rule-Based Access Control or RBAC
(confusing!)
Attribute-Based Access Control or ABAC
(can use attributes of the user, the resource,
the environment, etc)

