Hostile Data — The Bagel.Z Worm
The header as received
This was one of the earlier worms that forged the
"From" and "From:" fields
using the recipient's account and a
random (but perhaps similar) domain.
As you can see from the "Received:" line,
it really came from an infected Windows machine on a
DSL line in Brazil — read the Received
blocks from bottom to top:
From cromwe11@moose.cs.indiana.edu Sat Oct 9 05:54:31 2004
Received: from levee.ecn.purdue.edu (levee.ecn.purdue.edu [128.46.154.29])
by rvl3.ecn.purdue.edu (8.12.11/8.12.11) with ESMTP id i99AsUpU026018
(version=TLSv1/SSLv3 cipher=EDH-RSA-DES-CBC3-SHA bits=168 verify=NOT)
for <cromwe11@rvl3.ecn.purdue.edu>; Sat, 9 Oct 2004 05:54:30 -0500 (EST)
Received: from MSHOME.net (200-140-065-183.gnace7004.dsl.brasiltelecom.net.br [200.140.65.183])
by levee.ecn.purdue.edu (8.13.1/8.12.11) with SMTP id i99AsP9X028423
for <cromwe11@ecn.purdue.edu>; Sat, 9 Oct 2004 05:54:26 -0500 (EST)
Date: Sat, 09 Oct 2004 07:52:03 -0300
To: "Cromwell" <cromwe11@ecn.purdue.edu>
From: "Cromwell" <cromwe11@moose.cs.indiana.edu>
Subject: RE: Message Notify
Message-ID: <lqeraodxznxppacvbet@ecn.purdue.edu>
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="--------jotksssvnjvymhkgeysg"
Status: R
Content-Length: 31968
The clumsy message content
It is foolish to allow your mail interface to render HTML. Among other things, this is used by spammers to create "web bugs" that report back to them if you read their message, guaranteeing that you will get far more spam. Using mail safely, it should appear precisely as below:
----------jotksssvnjvymhkgeysg Content-Type: text/html; charset="us-ascii" Content-Transfer-Encoding: 7bit <html><body> <br>In order to read the attach you have to use the following password: <img src="cid:wnufcufljb.bmp"><br> <br> </body></html>
The attachments
This was followed by two attachments: an image and a zip file. The intent was to avoid automated virus detection by encrypting the zip file with a randomly selected pass phrase (apparently always a 5-digit number), and describing the pass phrase by showing a picture of it.
The image in this message was the following, which I have converted from buggy BMP to PNG format for display here, and which is being shown at twice normal resolution. It is extremely difficult to read, but it shows the digits "87338" in green against a varying background. I think this was intended to be easy to read, but the worm code is buggy:

It seems that the worm randomly varies several aspects of the mail. I bothered to save six copies, and I saw the following variation:
-
The name and size of the image file,
always a buggy BMP image, but not always hard to read:
wnufcufljb.bmp ( 56 x 16 pixels)vrpuivnxmr.bmp (119 x 15 pixels)logifxsgbv.bmp (117 x 18 pixels)fpavnzwajj.bmp ( 55 x 18 pixels)ttislpfwue.bmp ( 62 x 17 pixels)upimotswul.bmp ( 58 x 15 pixels)
-
The text that the image attempts to show:
87338
Pass - 26393
Password: 08064
15031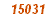
97399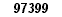
26148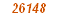
-
The name of the zip file, presumably taken from
a list.
Smoke.zipInfo.zipthe_message.zipYour_money.zipReadme.zipLoves_money.zip
-
The name of the executable and accompanying file
contained in the zip file.
The executable varied in size from 20173 to 21187 bytes.
The accompanying file has a randomly chosen
extension other than
.exebut always contains a random 6-character ASCII string not terminated by a newline. And I'm assuming here that they really are random:-
feslmuwwv.exe
fgxyu.dllcontaining the stringztmeoc -
dhdtcbe.exe
jzuuwwf.syscontaining the stringqpgorn -
cgbbcoo.exe
uoqvhfvbk.datcontaining the stringhlmqoz -
iuobtn.exe
kygokrs.idxcontaining the stringavriib -
jlwqwij.exe
zuuecti.dllcontaining the stringqiujvo -
rlffxs.exe
uiebx.idxcontaining the stringxmvjel
-
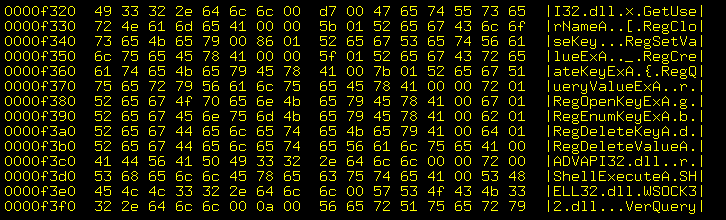
The executable contents
GNU utilities such as file, strings,
and hexdump are useful for
getting some limited idea about
what this malicious code might do.
The file utility reports that these executables
are each:
PE executable for MS Windows (GUI) Intel 80386 32-bit, UPX compressed
The following is partial output from running
hexdump -C feslmuwwv.exe
under Linux or BSD.
The interesting stuff appears down
around address 0x00004cd8, where we find
several calls to the Windows API
for networking and messing with the registry:
00000000 4d 5a 00 00 01 00 00 00 02 00 00 00 ff ff 00 00 |MZ..............| 00000010 40 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |@.......@.......| 00000020 b4 4c cd 21 00 00 00 00 00 00 00 00 00 00 00 00 |.L.!............| 00000030 00 00 00 00 00 00 00 00 00 00 00 00 90 00 00 00 |................| 00000040 a9 26 dd 13 ed 47 b3 40 ed 47 b3 40 ed 47 b3 40 |.&...G.@.G.@.G.@| 00000050 ed 47 b3 40 ee 47 b3 40 63 58 a0 40 6d 47 b3 40 |.G.@.G.@cX.@mG.@| 00000060 11 67 a1 40 ec 47 b3 40 2a 41 b5 40 ec 47 b3 40 |.g.@.G.@*A.@.G.@| 00000070 52 69 63 68 ed 47 b3 40 00 00 00 00 00 00 00 00 |Rich.G.@........| 00000080 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000090 50 45 00 00 4c 01 03 00 cc 0f 90 40 00 00 00 00 |PE..L......@....| [....] 00004ca0 90 f5 00 00 00 00 00 00 9e f5 00 00 00 00 00 00 |................| 00004cb0 ae f5 00 00 00 00 00 00 b8 f5 00 00 00 00 00 00 |................| 00004cc0 cc f5 00 00 00 00 00 00 d8 f5 00 00 00 00 00 00 |................|00004cd0 e8 f5 00 00 00 00 00 00 4b 45 52 4e 45 4c 33 32 |........KERNEL32|00004ce0 2e 44 4c 4c 00 61 64 76 61 70 69 33 32 2e 64 6c |.DLL.advapi32.dl|00004cf0 6c 00 67 64 69 33 32 2e 64 6c 6c 00 6f 6c 65 33 |l.gdi32.dll.ole3|00004d00 32 2e 64 6c 6c 00 53 48 45 4c 4c 33 32 2e 64 6c |2.dll.SHELL32.dl|00004d10 6c 00 73 68 6c 77 61 70 69 2e 64 6c 6c 00 75 72 |l.shlwapi.dll.ur|00004d20 6c 6d 6f 6e 2e 64 6c 6c 00 75 73 65 72 33 32 2e |lmon.dll.user32.|00004d30 64 6c 6c 00 77 69 6e 69 6e 65 74 2e 64 6c 6c 00 |dll.wininet.dll.|00004d40 77 73 6f 63 6b 33 32 2e 64 6c 6c 00 00 00 4c 6f |wsock32.dll...Lo|00004d50 61 64 4c 69 62 72 61 72 79 41 00 00 47 65 74 50 |adLibraryA..GetP|00004d60 72 6f 63 41 64 64 72 65 73 73 00 00 45 78 69 74 |rocAddress..Exit|00004d70 50 72 6f 63 65 73 73 00 00 00 52 65 67 43 6c 6f |Process...RegClo|00004d80 73 65 4b 65 79 00 00 00 44 65 6c 65 74 65 44 43 |seKey...DeleteDC|00004d90 00 00 43 6f 49 6e 69 74 69 61 6c 69 7a 65 00 00 |..CoInitialize..|00004da0 53 68 65 6c 6c 45 78 65 63 75 74 65 41 00 00 00 |ShellExecuteA...|00004db0 53 74 72 44 75 70 41 00 00 00 55 52 4c 44 6f 77 |StrDupA...URLDow|00004dc0 6e 6c 6f 61 64 54 6f 46 69 6c 65 41 00 00 77 73 |nloadToFileA..ws|00004dd0 70 72 69 6e 74 66 41 00 00 00 49 6e 74 65 72 6e |printfA...Intern|00004de0 65 74 4f 70 65 6e 41 00 00 00 62 69 6e 64 00 00 |etOpenA...bind..|00004df0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00004e00 16 81 86 61 00 35 0b 3a 7a ba 55 97 1e 2b 27 0b |...a.5.:z.U..+'.| 00004e10 3f 44 8c 24 81 be 90 12 3e 28 21 2a 31 c2 55 c6 |?D.$....>(!*1.U.| 00004e20 98 98 b9 31 48 4c 1c a6 b2 bd 6e 3a 0f 48 b5 0c |...1HL....n:.H..| 00004e30 3e 7d 5a 80 4d 3a 10 8b 09 75 95 39 a9 a0 be 92 |>}Z.M:...u.9....| 00004e40 18 9b 90 1d 3a 68 a1 57 1a b4 14 c6 38 46 3b 4f |....:h.W....8F;O| 00004e50 c3 97 00 43 86 70 35 bf 0e 78 72 a8 5e 5e 92 1a |...C.p5..xr.^^..| 00004e60 0a 2e 6a 34 2e 10 9d b6 53 81 84 c7 a1 16 61 68 |..j4....S.....ah| 00004e70 a5 b6 25 90 06 39 90 68 97 55 2e 6d 8e 87 2e 05 |..%..9.h.U.m....| 00004e80 0e a5 99 91 21 c4 04 4e 13 02 2e 69 8e 48 0d 26 |....!..N...i.H.&| 00004e90 55 57 3a 29 5e 6e 17 8e 7f 31 83 bf 1d 1a 5f 4a |UW:)^n...1...._J| 00004ea0 63 15 9f 49 0b 9d 68 3f bc 61 87 02 bc 09 c1 39 |c..I..h?.a.....9| 00004eb0 14 82 8a 44 c1 8d 58 70 7b 7b 9d 56 12 6e a0 4a |...D..Xp{{.V.n.J| 00004ec0 bd 54 94 56 63 01 24 12 35 bf 87 8e 0c |.T.Vc.$.5....| 00004ecd