Hostile Data — Trojan.Exchanger.DL
The attachment
A message arrived with an attached file named
video1.exe.
The message was the usual social engineering attempt to
interest the human on the receiving end with promises of
scandalous news.
The executable contents
GNU utilities such as file, strings,
and hexdump are useful for
getting some limited idea about
what this malicious code might do.
The file utility reports that this executable
is:
PE32 executable for MS Windows (GUI) Intel 80386 32-bit
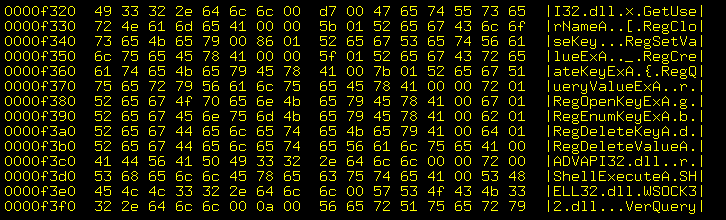
The following is partial output for running
hexdump -C video1.exe
under Linux or BSD.
The interesting stuff appears near the very end, where you
see shared library calls including, among others:
URLOpenPullStreamW()
URLDownloadToFileA()
CoInternetCreateSecurityManager()
URLOpenStreamA()
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............| 00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......| 00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000030 00 00 00 00 00 00 00 00 00 00 00 00 e8 00 00 00 |................|00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|00000080 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000090 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 000000a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|000000e0 00 00 00 00 00 00 00 00 50 45 00 00 4c 01 04 00 |........PE..L...|000000f0 78 35 e2 47 00 00 00 00 00 00 00 00 e0 00 03 01 |x5.G............| [....] 000001d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|000001e0 2e 74 65 78 74 00 00 00 27 df 00 00 00 10 00 00 |.text...'.......|000001f0 00 a4 00 00 00 10 00 00 00 00 00 00 00 00 00 00 |................|00000200 00 00 00 00 20 00 00 60 2e 72 64 61 74 61 00 00 |.... ..`.rdata..|00000210 70 39 00 00 00 f0 00 00 00 1c 00 00 00 b4 00 00 |p9..............| [....] 00018ee0 1a 1a 02 00 00 00 00 00 00 00 00 00 8e 19 02 00 |................| 00018ef0 1a 1a 02 00 7a 19 02 00 00 00 00 00 00 00 00 00 |....z...........| 00018f00 30 19 02 00 7a 19 02 00 c0 1a 02 00 00 00 00 00 |0...z...........| 00018f10 00 00 00 00 36 1a 02 00 c0 1a 02 00 00 00 00 00 |....6...........| 00018f20 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|00018f30 55 53 45 52 33 32 2e 44 4c 4c 00 00 00 4d 65 73 |USER32.DLL...Mes|00018f40 73 61 67 65 42 6f 78 41 00 00 00 43 61 6c 6c 4d |sageBoxA...CallM|00018f50 73 67 46 69 6c 74 65 72 41 00 00 00 41 64 6a 75 |sgFilterA...Adju|00018f60 73 74 57 69 6e 64 6f 77 52 65 63 74 00 00 00 43 |stWindowRect...C|00018f70 72 65 61 74 65 49 63 6f 6e 00 3b 19 02 00 49 19 |reateIcon.;...I.|00018f80 02 00 5a 19 02 00 6d 19 02 00 00 00 00 00 55 52 |..Z...m.......UR|00018f90 4c 4d 4f 4e 2e 44 4c 4c 00 00 00 48 6c 69 6e 6b |LMON.DLL...Hlink|00018fa0 47 6f 46 6f 72 77 61 72 64 00 00 00 55 52 4c 4f |GoForward...URLO|00018fb0 70 65 6e 50 75 6c 6c 53 74 72 65 61 6d 57 00 00 |penPullStreamW..|00018fc0 00 42 69 6e 64 41 73 79 6e 63 4d 6f 6e 69 6b 65 |.BindAsyncMonike|00018fd0 72 00 00 00 55 52 4c 44 6f 77 6e 6c 6f 61 64 54 |r...URLDownloadT|00018fe0 6f 46 69 6c 65 41 00 00 00 43 6f 49 6e 74 65 72 |oFileA...CoInter|00018ff0 6e 65 74 43 72 65 61 74 65 53 65 63 75 72 69 74 |netCreateSecurit|00019000 79 4d 61 6e 61 67 65 72 00 00 00 55 52 4c 4f 70 |yManager...URLOp|00019010 65 6e 53 74 72 65 61 6d 41 00 99 19 02 00 aa 19 |enStreamA.......|00019020 02 00 bf 19 02 00 d2 19 02 00 e7 19 02 00 09 1a |................|00019030 02 00 00 00 00 00 57 49 4e 49 4e 45 54 2e 44 4c |......WININET.DL|00019040 4c 00 00 00 49 6e 74 65 72 6e 65 74 4f 70 65 6e |L...InternetOpen|00019050 41 00 00 00 46 74 70 43 72 65 61 74 65 44 69 72 |A...FtpCreateDir|00019060 65 63 74 6f 72 79 57 00 00 00 47 6f 70 68 65 72 |ectoryW...Gopher|00019070 47 65 74 41 74 74 72 69 62 75 74 65 41 00 00 00 |GetAttributeA...|00019080 49 6e 63 72 65 6d 65 6e 74 55 72 6c 43 61 63 68 |IncrementUrlCach|00019090 65 48 65 61 64 65 72 44 61 74 61 00 00 00 49 6e |eHeaderData...In|000190a0 74 65 72 6e 65 74 43 6f 6d 62 69 6e 65 55 72 6c |ternetCombineUrl|000190b0 41 00 00 00 46 74 70 47 65 74 46 69 6c 65 41 00 |A...FtpGetFileA.|000190c0 42 1a 02 00 52 1a 02 00 68 1a 02 00 7e 1a 02 00 |B...R...h...~...| 000190d0 9c 1a 02 00 b2 1a 02 00 00 00 00 00 00 00 00 00 |................| 000190e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 00019600