Hostile Data — The Downloader.Tibs.Gen-1 Trojan
The header as received
These come in from infected Windows PCs. Some of the header fields are diagnostic, highlighted below:
From rkii@andaremarketing.com Sun Feb 4 06:16:53 2007 Received: from levee.ecn.purdue.edu (levee.ecn.purdue.edu [128.46.154.29]) by rvl4.ecn.purdue.edu (8.13.8/8.13.8) with ESMTP id l14BGqQj001958 (version=TLSv1/SSLv3 cipher=DHE-RSA-AES256-SHA bits=256 verify=NOT) for <cromwe11@rvl4.ecn.purdue.edu>; Sun, 4 Feb 2007 06:16:53 -0500 (EST) Received: from pytz ([218.148.158.102]) by levee.ecn.purdue.edu (8.13.6/8.13.6) with SMTP id l14BGNg2005928 for <cromwe11@sclera.ecn.purdue.edu>; Sun, 4 Feb 2007 06:16:44 -0500 (EST) Received: from [108.168.66.158] (helo=egnxv) by pytz with smtp (Exim 4.43) id 1HDfM4-0006hL-Tr; Sun, 4 Feb 2007 20:16:20 +0900 Message-ID: <45C5BFD4.3060507@andaremarketing.com> Date: Sun, 4 Feb 2007 20:13:24 +0900 From: nasally <rkii@andaremarketing.com> User-Agent: Thunderbird 1.5.0.9 (Windows/20061207) MIME-Version: 1.0 To: cromwe11@ecn.purdue.edu Subject: Will You? Content-Type: multipart/related; boundary="------------030603090004090109020307" Status: R Content-Length: 68695
All of these that I have noticed contain the claim that the user-agent is Thunderbird 1.5.0.9 Windows/20061207. I don't know if this is a bogus claim made by the Trojan itself, or if the Trojan uses Thunderbird to forward itself.
As far as the network path of this one, it seems
to have started at 108.168.66.158 (read the headers
from bottom to top).
As per whois,
that is a reserved block of IP addresses and
probably is a spoofed header entry.
The "next hop", probably where it really started from,
is a machine claiming a hostname of pytz
at IP address 218.148.158.102.
As per whois,
that's a machine at the Korean NIC!
From there it takes one hop across the Purdue network,
from the mail gateway levee.ecn.purdue.edu
to the server where my mail is held,
rvl4.ecn.purdue.edu.
The attachment
I haven't noticed any text message, just an attached
executable named
"Postcard.exe"
or
"Flash Postcard.exe".
This Trojan attachment could easily be
spotted by virus-scanning software.
The attack relies on two things:
- New variants appear in the wild frequently, and there will be windows of opportunity for the attacker before a virus-detection signature list is updated.
- Some people who use Windows are foolish enough to just click on a plainly-labeled executable received from an unknown address for no apparent reason.
Clearly the attack works, as these keep showing up.
The executable contents
GNU utilities such as file, strings,
and hexdump are useful for
getting some limited idea about
what this malicious code might do.
The file utility reports that this executable
is:
PE executable for MS Windows (GUI) Intel 80386 32-bit, UPX compressed
The following is partial output for running
hexdump -C Postcard.exe
under Linux or BSD.
Like most downloader Trojans, this one doesn't have terribly interesting contents. See some of my other pages for worms that modify the registry and otherwise have more obviously harmful attributes We do see here:
-
Around addresses
0x00000040through0x000003efwhere the usual signs of Windows executables appear. -
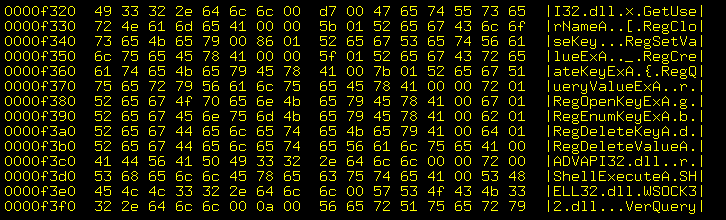
Around addresses
0x0000c4e0through0x0000c56f,where references to the Windows API appear.
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............| 00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......| 00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000030 00 00 00 00 00 00 00 00 00 00 00 00 d8 00 00 00 |................|00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|00000080 87 d3 28 03 c3 b2 46 50 c3 b2 46 50 c3 b2 46 50 |..(...FP..FP..FP| 00000090 00 bd 1b 50 c8 b2 46 50 c3 b2 47 50 91 b2 46 50 |...P..FP..GP..FP| 000000a0 e4 74 3b 50 c2 b2 46 50 e4 74 28 50 ca b2 46 50 |.t;P..FP.t(P..FP| 000000b0 e4 74 3e 50 c2 b2 46 50 52 69 63 68 c3 b2 46 50 |.t>P..FPRich..FP| 000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|000000d0 00 00 00 00 00 00 00 00 50 45 00 00 4c 01 03 00 |........PE..L...|000000e0 1c c1 c4 45 00 00 00 00 00 00 00 00 e0 00 03 01 |...E............| 000000f0 0b 01 08 00 00 c0 00 00 00 10 00 00 00 f0 14 00 |................| 00000100 00 b8 15 00 00 00 15 00 00 c0 15 00 00 00 40 00 |..............@.| 00000110 00 10 00 00 00 02 00 00 04 00 00 00 00 00 00 00 |................| 00000120 04 00 00 00 00 00 00 00 00 d0 15 00 00 10 00 00 |................| 00000130 00 00 00 00 02 00 00 04 00 00 10 00 00 10 00 00 |................| 00000140 00 00 10 00 00 10 00 00 00 00 00 00 10 00 00 00 |................| 00000150 00 00 00 00 00 00 00 00 80 c6 15 00 64 00 00 00 |............d...| 00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 00000190 00 00 00 00 00 00 00 00 6f c7 15 00 18 00 00 00 |........o.......| 000001a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| *000001d0 55 50 58 30 00 00 00 00 00 f0 14 00 00 10 00 00 |UPX0............|000001e0 00 00 00 00 00 04 00 00 00 00 00 00 00 00 00 00 |................|000001f0 00 00 00 00 80 00 00 e0 55 50 58 31 00 00 00 00 |........UPX1....|00000200 00 c0 00 00 00 00 15 00 00 ba 00 00 00 04 00 00 |................| 00000210 00 00 00 00 00 00 00 00 00 00 00 00 40 00 00 e0 |............@...|00000220 55 50 58 32 00 00 00 00 00 10 00 00 00 c0 15 00 |UPX2............|00000230 97 07 00 00 00 be 00 00 00 00 00 00 00 00 00 00 |................| 00000240 00 00 00 00 40 00 00 c0 00 00 00 00 00 00 00 00 |....@...........| 00000250 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 000003d0 00 00 00 00 00 00 00 00 00 00 00 32 2e 39 31 00 |...........2.91.|000003e0 55 50 58 21 0d 09 08 08 59 97 bc 68 b4 13 15 76 |UPX!....Y..h...v|000003f0 1c 95 15 00 ff b7 00 00 00 e0 00 00 26 00 00 31 |............&..1| 00000400 be f0 de e0 d0 9d 3c 20 ec 82 cd 95 07 64 94 fc |......< .....d..| [....] 0000c4b0 00 00 00 00 ec c6 15 00 e4 c6 15 00 4a c7 15 00 |............J...| 0000c4c0 00 00 00 00 00 00 00 00 52 c7 15 00 4a c7 15 00 |........R...J...| 0000c4d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|0000c4e0 00 00 00 00 f7 c6 15 00 00 00 00 00 55 53 45 52 |............USER|0000c4f0 33 32 2e 44 4c 4c 00 00 00 44 64 65 49 6e 69 74 |32.DLL...DdeInit|0000c500 69 61 6c 69 7a 65 41 00 1d c7 15 00 00 00 00 00 |ializeA.........|0000c510 43 4f 4d 43 54 4c 33 32 2e 44 4c 4c 00 00 00 4d |COMCTL32.DLL...M|0000c520 61 6b 65 44 72 61 67 4c 69 73 74 00 40 c7 15 00 |akeDragList.@...|0000c530 00 00 00 00 53 48 45 4c 4c 33 32 2e 44 4c 4c 00 |....SHELL32.DLL.|0000c540 00 00 53 74 72 53 74 72 41 00 5d c7 15 00 00 00 |..StrStrA.].....|0000c550 00 00 55 53 45 52 33 32 2e 44 4c 4c 00 00 00 43 |..USER32.DLL...C|0000c560 61 6c 6c 57 69 6e 64 6f 77 50 72 6f 63 41 00 8f |allWindowProcA..|0000c570 c7 55 00 93 c7 55 00 8b c7 55 00 87 c7 55 00 00 |.U...U...U...U..| 0000c580 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 0000c590 00 00 00 00 00 00 00 |.......| 0000c597