Hostile Data — The Stration.JH Worm
The header as received
Read the Received lines the correct
order, from bottom to top.
-
IP address
192.168.2.72,calling itselflqy,sent it to192.168.2.20.
That is part of a private IP address block, so it started behind an address-translating firewall. This could be:- Someone at home with a LinkSys or D-Link router or similar.
- Someone sending spam from work.
- Someone abusing the wireless router at a coffee shop, hotel, or similar.
- Someone abusing the wireless router at a company, parked out in their parking lot or on the street.
-
IP address
217.227.224.130, calling itselfDAVOR2although that IP address resolves topd9e3d082.dip.t-dialin.net,sent it to my ISP.
That IP address is assigned to Deutsche Telekom. - A couple of hops within my ISP.
From sec@fcradio.net Sat Oct 21 12:27:45 2006 Return-path: <sec@fcradio.net> Received: from mta0.manage.insightcom.com ([172.31.249.150]) by msb1.manage.insightcom.com (Sun Java System Messaging Server 6.2-6.01 (built Apr 3 2006)) with ESMTP id <0J7I00MYQSZU8TD0@msb1.manage.insightcom.com> for bob.cromwe11@insightbb.com; Sun, 22 Oct 2006 00:40:42 -0400 (EDT) Received: from asav05.insightbb.com ([172.31.249.123]) by mta0.manage.insightcom.com (Sun Java System Messaging Server 6.2-6.01 (built Apr 3 2006)) with ESMTP id <0J7I00MALSZTUP81@mta0.manage.insightcom.com> for bob.cromwe11@insightbb.com (ORCPT bob.cromwe11@insightbb.com); Sun, 22 Oct 2006 00:40:42 -0400 (EDT) Received: from pd9e3e082.dip.t-dialin.net (HELO DAVOR2) ([217.227.224.130]) by asav05.insightbb.com with SMTP; Sat, 21 Oct 2006 12:38:38 -0400 Received: (qmail 2638 invoked by uid 0); Sat, 21 Oct 2006 18:37:45 -0000) Received: from unknown (HELO lqy) (192.168.2.72) by 192.168.2.20 with SMTP; Sat, 21 Oct 2006 18:37:45 +0000 Date: Sat, 21 Oct 2006 18:27:45 +0200 From: sec@fcradio.net Subject: Mail server report. To: bob.cromwe11@insightbb.com Message-id: <5aoen5$blo75n@asav05.manage.insightbb.com> MIME-version: 1.0 Content-type: multipart/mixed; boundary=-----------C1A6D3F3CBA6C1D4 Original-recipient: rfc822;bob.cromwe11@insightbb.com
The clumsy message content
I have a ham radio license and
am interested in radio in general,
and so I am on a number of radio-related mailing lists.
One of them is a weekly report of geomagnetic activity
from the
US NOAA Space Environment Center.
So, the forged sender address sec@fcradio.net
caught my eye.
Was this worm sent to the addresses on an illicitly obtained
copy of this mailing list?
Maybe...
The message text was not written by anyone native-fluent in English. Among other things, see the botched use of the definite article "the", which is missing in some places it appears but extraneously appears in inappropriate places.
Mail server report.
Our firewall determined the e-mails containing worm copies
are being sent from your computer.
Nowadays it happens from many computers, because this is
a new virus type (Network Worms).
Using the new bug in the Windows, these viruses infect
the computer unnoticeably.
After the penetrating into the computer the virus harvests
all the e-mail addresses and sends the copies of itself
to these e-mail addresses
Please install updates for worm elimination and your
computer restoring.
Best regards,
Customers support service .
The attachment
This was followed by an attached zip file
named
Update-KB9453-x86.zip,
which contained a file named
Update-KB9453-x86.exe.
The executable contents
GNU utilities such as file, strings,
and hexdump are useful for
getting some limited idea about
what this malicious code might do.
The file utility reports that this executable
is:
MS-DOS executable (EXE), OS/2 or Windows
The following is partial output for running
hexdump -C Update-KB9453-x86.exe
under Linux or BSD.
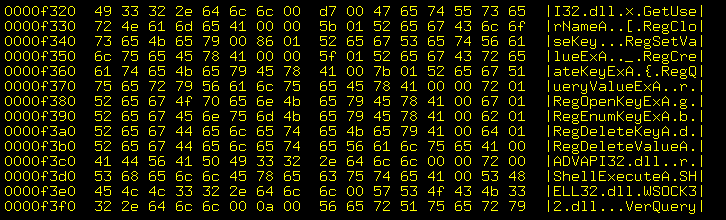
The interesting stuff appears, among many other places:
-
Around address
0x00001560where Windows library references appear. -
Around address
0x000015d0where suspicious strings appear. -
Around address
0x000021a0where Windows library references appear.
This appears to be precisely what it warns about — a worm that sends itself (plus, probably, loads of spam) on to addresses harvested from the target host. I don't see the usual calls to modify the target system's registry, so this worm might disappear at a reboot.
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............| 00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......| 00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000030 00 00 00 00 00 00 00 00 00 00 00 00 c8 00 00 00 |................|00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th| 00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno| 00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS | 00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|00000080 07 69 c2 dc 43 08 ac 8f 43 08 ac 8f 43 08 ac 8f |.i..C...C...C...| 00000090 c0 00 f1 8f 40 08 ac 8f 43 08 ad 8f 41 08 ac 8f |....@...C...A...| 000000a0 46 04 cc 8f 40 08 ac 8f af 03 f2 8f 42 08 ac 8f |F...@.......B...|000000b0 46 04 f6 8f 42 08 ac 8f 52 69 63 68 43 08 ac 8f |F...B...RichC...| 000000c0 00 00 00 00 00 00 00 00 50 45 00 00 4c 01 03 00 |........PE..L...| 000000d0 45 dd 38 45 00 00 00 00 00 00 00 00 e0 00 0f 01 |E.8E............|000000e0 0b 01 07 0a 00 20 00 00 00 10 00 00 00 50 00 00 |..... .......P..| [....] 00001540 34 5a 02 22 58 65 2f b2 d0 ae 59 66 3d 03 4c 18 |4Z."Xe/...Yf=.L.| 00001550 14 5c ca 46 51 01 0d 04 48 a8 08 ff 83 1c 04 3c |.\.FQ...H......<|00001560 01 4c 6f 61 64 4c 69 62 72 cf fe ff f2 61 72 79 |.LoadLibr....ary| 00001570 41 47 65 74 50 72 6f 63 41 64 64 72 65 73 73 22 |AGetProcAddress"|00001580 50 45 0f f2 6f 01 0e 01 03 00 45 dd 38 45 e0 00 |PE..o.....E.8E..| 00001590 0f f7 ec 0b f8 01 0b 01 07 0a 3b 0e 13 40 1a 04 |..........;..@..| 000015a0 b6 9c c5 5e 10 08 0d 0b 02 04 33 6c 49 37 0b 07 |...^......3lI7..| 000015b0 0c 60 1e 96 2c d9 ec 10 2b 07 06 03 84 9a 6f 39 |.`..,...+.....o9| 000015c0 8c 30 28 3a 50 09 44 03 59 17 08 64 0c 1e 2e d8 |.0(:P.D.Y..d....|000015d0 17 6c f3 74 65 78 74 f0 20 90 eb 04 23 c1 36 bf |.l.text. ...#.6.| 000015e0 5b 1a 60 2e 64 61 74 61 c8 02 fb f7 bb 85 7d 07 |[.`.data......}.|000015f0 26 27 16 c0 2e 72 73 72 63 fe a6 a4 e9 be c3 50 |&'...rsrc......P| 00001600 27 0a 28 40 00 00 f7 fd 1b c0 30 0d 2b 09 02 00 |'.(@......0.+...| [....] 00002160 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00002170 a0 89 00 00 8c 89 00 00 00 00 00 00 00 00 00 00 |................| 00002180 00 00 00 00 00 00 00 00 00 00 00 00 ac 89 00 00 |................| 00002190 ba 89 00 00 ca 89 00 00 da 89 00 00 00 00 00 00 |................|000021a0 4b 45 52 4e 45 4c 33 32 2e 44 4c 4c 00 00 4c 6f |KERNEL32.DLL..Lo| 000021b0 61 64 4c 69 62 72 61 72 79 41 00 00 47 65 74 50 |adLibraryA..GetP| 000021c0 72 6f 63 41 64 64 72 65 73 73 00 00 56 69 72 74 |rocAddress..Virt| 000021d0 75 61 6c 50 72 6f 74 65 63 74 00 00 45 78 69 74 |ualProtect..Exit| 000021e0 50 72 6f 63 65 73 73 00 00 00 00 00 00 00 00 00 |Process.........|000021f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00002200 ee ff ee ff |....| 00002204