Hostile Data — Win.Trojan.Upatre, a.k.a. Trojan.Win32.Staser.ayze
The attachment
I got this sample from a large academic network. The attachment had already been quarantined, I don't have the original message header or content.
The attachment was a zip file with a name that suggested it contains a PDF file. However, it contains an executable SCR file. Let's look at the original file,
% /bin/ls -l
total 12
-rw-r--r-- 1 cromwell cromwell 11812 Feb 18 13:45 doc17823_pdf.zip
% file *
doc17823_pdf.zip: Zip archive data, at least v2.0 to extract
% unzip -l doc17823_pdf.zip
Archive: doc17823_pdf.zip
Length Date Time Name
--------- ---------- ----- ----
32512 02-12-2015 15:30 doc17823_pdf.scr
--------- -------
32512 1 file
% unzip doc17823_pdf.zip
Archive: doc17823_pdf.zip
inflating: doc17823_pdf.scr
% file *
doc17823_pdf.scr: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
doc17823_pdf.zip: Zip archive data, at least v2.0 to extract
Malware Detection
ClamAV detects this as Win.Trojan.Upatre-168. Kaspersky detects it as Trojan.Win32.Staser.ayze, McAfee detects it as Upatre-FAAR!78B91A5EAF37, Symantec detects it as Downloader.Upatre, and other names names are used by other AV vendors. "Upatre" is the closest to a common name.
% clamscan * doc17823_pdf.scr: Win.Trojan.Upatre-168 FOUND doc17823_pdf.zip: Win.Trojan.Upatre-168 FOUND ----------- SCAN SUMMARY ----------- Known viruses: 3746855 Engine version: 0.98.6 Scanned directories: 0 Scanned files: 2 Infected files: 2 Data scanned: 0.05 MB Data read: 0.04 MB (ratio 1.56:1) Time: 9.314 sec (0 m 9 s)
The executable contents
GNU utilities such as file, strings,
and hexdump are useful for
getting some limited idea about
what this malicious code might do.
The following is partial output for running
hexdump under Linux or BSD.
Like most downloader Trojans, this one doesn't have terribly interesting contents. See some of my other pages for worms that modify the registry and otherwise have more obviously harmful attributes.
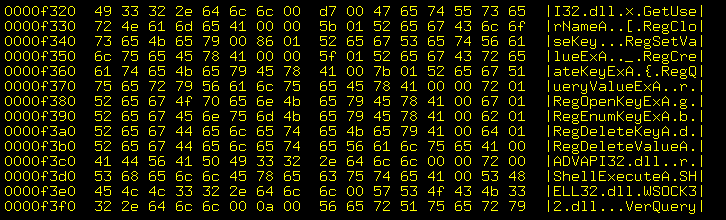
We do see some slightly unusual things here:
-
Around addresses
0x00001240through0x0000126f,0x000013e0through0x0000140f, and0x00001a10through0x00001a3fwhere there are references to keys and signing. -
At the end, around
0x00007330through0x0000751f,an XML file is embedded.
% hexdump -C doc17823_pdf.scr 00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............| 00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......| 00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000030 00 00 00 00 00 00 00 00 00 00 00 00 c8 00 00 00 |................| 00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th| 00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno| 00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS | 00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......| 00000080 07 cd ff db 46 ac 91 88 43 ac 91 88 43 ac 91 88 |....F...C...C...| 00000090 43 ac 91 88 47 ac 91 88 c0 b0 9f 88 42 ac 91 88 |C...G.......B...| 000000a0 cd b3 82 88 42 ac 91 88 52 69 63 68 43 ac 91 88 |....B...RichC...| 000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 000000c0 00 00 00 00 00 00 00 00 50 45 00 00 4c 01 04 00 |........PE..L...| 000000d0 7e 7d 56 54 00 00 00 00 00 00 00 00 e0 00 03 03 |~}VT............| [....] 00001210 00 00 00 00 c4 af 00 00 00 00 00 00 de af 00 00 |................| 00001220 00 00 00 00 fa af 00 00 00 00 00 00 1e b0 00 00 |................| 00001230 34 b0 00 00 4a b0 00 00 60 b0 00 00 74 b0 00 00 |4...J...`...t...| 00001240 00 00 00 00 00 00 50 76 6b 50 72 69 76 61 74 65 |......PvkPrivate| 00001250 4b 65 79 4c 6f 61 64 00 6d 73 73 69 67 6e 33 32 |KeyLoad.mssign32| 00001260 2e 64 6c 6c 00 00 00 00 4d 54 78 4f 63 69 49 6e |.dll....MTxOciIn| 00001270 69 74 00 00 6d 74 78 6f 63 69 2e 64 6c 6c 00 00 |it..mtxoci.dll..| 00001280 00 00 43 72 65 61 74 65 4c 6f 67 46 69 6c 65 00 |..CreateLogFile.| 00001290 6d 73 6f 65 72 74 32 2e 64 6c 6c 00 00 00 4e 44 |msoert2.dll...ND| 000012a0 64 65 47 65 74 54 72 75 73 74 65 64 53 68 61 72 |deGetTrustedShar| 000012b0 65 41 00 00 6e 64 64 65 61 70 69 2e 64 6c 6c 00 |eA..nddeapi.dll.| 000012c0 00 00 43 6f 6e 76 65 72 74 49 4e 65 74 52 65 73 |..ConvertINetRes| 000012d0 65 74 00 00 6d 6c 61 6e 67 2e 64 6c 6c 00 00 00 |et..mlang.dll...| 000012e0 52 65 70 6c 61 63 65 46 69 6c 65 41 00 00 00 00 |ReplaceFileA....| 000012f0 47 65 74 41 43 50 00 00 00 00 52 74 6c 4d 6f 76 |GetACP....RtlMov| 00001300 65 4d 65 6d 6f 72 79 00 00 00 53 65 74 43 6f 6d |eMemory...SetCom| 00001310 70 75 74 65 72 4e 61 6d 65 41 00 00 00 00 51 75 |puterNameA....Qu| 00001320 65 72 79 44 6f 73 44 65 76 69 63 65 41 00 00 00 |eryDosDeviceA...| 00001330 43 72 65 61 74 65 4a 6f 62 4f 62 6a 65 63 74 57 |CreateJobObjectW| 00001340 00 00 00 00 52 65 61 64 43 6f 6e 73 6f 6c 65 4f |....ReadConsoleO| 00001350 75 74 70 75 74 57 00 00 00 00 52 65 67 69 73 74 |utputW....Regist| 00001360 65 72 57 6f 77 45 78 65 63 00 00 00 42 65 65 70 |erWowExec...Beep| 00001370 00 00 00 00 5f 6c 6f 70 65 6e 00 00 00 00 47 65 |...._lopen....Ge| 00001380 74 50 72 6f 66 69 6c 65 49 6e 74 57 00 00 00 00 |tProfileIntW....| 00001390 54 65 72 6d 69 6e 61 74 65 50 72 6f 63 65 73 73 |TerminateProcess| 000013a0 00 00 00 00 54 65 72 6d 69 6e 61 74 65 50 72 6f |....TerminatePro| 000013b0 63 65 73 73 00 00 00 00 47 65 74 53 79 73 74 65 |cess....GetSyste| 000013c0 6d 44 69 72 65 63 74 6f 72 79 41 00 00 00 52 65 |mDirectoryA...Re| 000013d0 61 64 46 69 6c 65 00 00 6b 65 72 6e 65 6c 33 32 |adFile..kernel32| 000013e0 2e 64 6c 6c 00 00 00 00 50 76 6b 50 72 69 76 61 |.dll....PvkPriva| 000013f0 74 65 4b 65 79 4c 6f 61 64 00 6d 73 73 69 67 6e |teKeyLoad.mssign| 00001400 33 32 2e 64 6c 6c 00 00 00 00 4d 54 78 4f 63 69 |32.dll....MTxOci| 00001410 49 6e 69 74 00 00 6d 74 78 6f 63 69 2e 64 6c 6c |Init..mtxoci.dll| 00001420 00 00 00 00 43 72 65 61 74 65 4c 6f 67 46 69 6c |....CreateLogFil| 00001430 65 00 6d 73 6f 65 72 74 32 2e 64 6c 6c 00 00 00 |e.msoert2.dll...| 00001440 4e 44 64 65 47 65 74 54 72 75 73 74 65 64 53 68 |NDdeGetTrustedSh| 00001450 61 72 65 41 00 00 6e 64 64 65 61 70 69 2e 64 6c |areA..nddeapi.dl| 00001460 6c 00 00 00 50 64 68 43 6c 6f 73 65 4c 6f 67 00 |l...PdhCloseLog.| [....] 000019f0 50 64 68 45 6e 75 6d 4f 62 6a 65 63 74 73 48 57 |PdhEnumObjectsHW| 00001a00 00 00 00 00 50 64 68 45 6e 75 6d 4f 62 6a 65 63 |....PdhEnumObjec| 00001a10 74 73 57 00 70 64 68 2e 64 6c 6c 00 00 00 50 76 |tsW.pdh.dll...Pv| 00001a20 6b 50 72 69 76 61 74 65 4b 65 79 4c 6f 61 64 00 |kPrivateKeyLoad.| 00001a30 6d 73 73 69 67 6e 33 32 2e 64 6c 6c 00 00 00 00 |mssign32.dll....| 00001a40 4d 54 78 4f 63 69 49 6e 69 74 00 00 6d 74 78 6f |MTxOciInit..mtxo| 00001a50 63 69 2e 64 6c 6c 00 00 00 00 43 72 65 61 74 65 |ci.dll....Create| 00001a60 4c 6f 67 46 69 6c 65 00 6d 73 6f 65 72 74 32 2e |LogFile.msoert2.| 00001a70 64 6c 6c 00 00 00 4e 44 64 65 47 65 74 54 72 75 |dll...NDdeGetTru| 00001a80 73 74 65 64 53 68 61 72 65 41 00 00 6e 64 64 65 |stedShareA..ndde| 00001a90 61 70 69 2e 64 6c 6c 00 00 00 43 6f 6e 76 65 72 |api.dll...Conver| [....] 00007310 00 00 00 00 00 00 00 00 02 03 04 05 06 07 08 09 |................| 00007320 0a 0b 0c 0d 0e 0f 10 11 12 13 14 15 16 17 18 19 |................| 00007330 1a 1b 1c 1d 1e 1f 20 21 22 3c 3f 78 6d 6c 20 76 |...... !"<?xml v| 00007340 65 72 73 69 6f 6e 3d 22 31 2e 30 22 20 65 6e 63 |ersion="1.0" enc| 00007350 6f 64 69 6e 67 3d 22 55 54 46 2d 38 22 20 73 74 |oding="UTF-8" st| 00007360 61 6e 64 61 6c 6f 6e 65 3d 22 79 65 73 22 3f 3e |andalone="yes"?>| 00007370 0d 0a 3c 61 73 73 65 6d 62 6c 79 20 78 6d 6c 6e |..<assembly xmln| 00007380 73 3d 22 75 72 6e 3a 73 63 68 65 6d 61 73 2d 6d |s="urn:schemas-m| 00007390 69 63 72 6f 73 6f 66 74 2d 63 6f 6d 3a 61 73 6d |icrosoft-com:asm| 000073a0 2e 76 31 22 20 6d 61 6e 69 66 65 73 74 56 65 72 |.v1" manifestVer| 000073b0 73 69 6f 6e 3d 22 31 2e 30 22 3e 0d 0a 3c 61 73 |sion="1.0">..<as| 000073c0 73 65 6d 62 6c 79 49 64 65 6e 74 69 74 79 20 76 |semblyIdentity v| 000073d0 65 72 73 69 6f 6e 3d 22 31 2e 30 2e 30 2e 30 22 |ersion="1.0.0.0"| 000073e0 0d 0a 70 72 6f 63 65 73 73 6f 72 41 72 63 68 69 |..processorArchi| 000073f0 74 65 63 74 75 72 65 3d 22 58 38 36 22 0d 0a 6e |tecture="X86"..n| 00007400 61 6d 65 3d 22 4e 61 6d 65 22 0d 0a 74 79 70 65 |ame="Name"..type| 00007410 3d 22 77 69 6e 33 32 22 2f 3e 0d 0a 3c 64 65 73 |="win32"/>..<des| 00007420 63 72 69 70 74 69 6f 6e 3e 4e 61 6d 65 20 28 4c |cription>Name (L| 00007430 61 75 6e 63 68 65 72 29 3c 2f 64 65 73 63 72 69 |auncher)</descri| 00007440 70 74 69 6f 6e 3e 0d 0a 3c 74 72 75 73 74 49 6e |ption>..<trustIn| 00007450 66 6f 20 78 6d 6c 6e 73 3d 22 75 72 6e 3a 73 63 |fo xmlns="urn:sc| 00007460 68 65 6d 61 73 2d 6d 69 63 72 6f 73 6f 66 74 2d |hemas-microsoft-| 00007470 63 6f 6d 3a 61 73 6d 2e 76 32 22 3e 0d 0a 3c 73 |com:asm.v2">..<s| 00007480 65 63 75 72 69 74 79 3e 0d 0a 3c 72 65 71 75 65 |ecurity>..<reque| 00007490 73 74 65 64 50 72 69 76 69 6c 65 67 65 73 3e 0d |stedPrivileges>.| 000074a0 0a 3c 72 65 71 75 65 73 74 65 64 45 78 65 63 75 |.<requestedExecu| 000074b0 74 69 6f 6e 4c 65 76 65 6c 0d 0a 6c 65 76 65 6c |tionLevel..level| 000074c0 3d 22 61 73 49 6e 76 6f 6b 65 72 22 0d 0a 75 69 |="asInvoker"..ui| 000074d0 41 63 63 65 73 73 3d 22 66 61 6c 73 65 22 2f 3e |Access="false"/>| 000074e0 0d 0a 3c 2f 72 65 71 75 65 73 74 65 64 50 72 69 |..</requestedPri| 000074f0 76 69 6c 65 67 65 73 3e 0d 0a 3c 2f 73 65 63 75 |vileges>..</secu| 00007500 72 69 74 79 3e 0d 0a 3c 2f 74 72 75 73 74 49 6e |rity>..</trustIn| 00007510 66 6f 3e 0d 0a 3c 2f 61 73 73 65 6d 62 6c 79 3e |fo>..</assembly>| 00007520 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 00007f00
The XML file would be:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<assemblyIdentity version="1.0.0.0"
processorArchitecture="X86"
name="Name"
type="win32"/>
<description>Name (Launcher)</description>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges>
<requestedExecutionLevel
level="asInvoker"
uiAccess="false"/>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
Many more details are available here about the file's internals.