
Cybersecurity Basics:
Staying Safe Online
How To Stay Safe Online
The Internet is a dangerous place.
Criminal gangs steal and sell credit card numbers and
banking details.
"Crypto-locker" attacks take away all your personal data
and demand payment to restore it.
Email and Facebook accounts are hijacked,
and on and on.
This page aims to be a "just enough" starting point.
Basic, easy, important steps that anyone could use
to improve their security on the Internet.
Yes, there are sophisticated and complex defenses,
but start with these basics.
I do consulting work and I write and teach
training courses for U.S. government agencies and
their contractors, and I tell them the complicated parts.
This page isn't for them.
Everyone needs to:
The most important parts appear first. This is a long series of pages, I know that few people will read the entire thing. The further you go through these suggestions, the better, so let's start with the most important and practical defenses.
Stay Up To Date
The most important thing to do first is to keep your computers and phones updated. So many hacks and data thefts wouldn't have happened if people had only kept their systems up to date.
Yes, it feels tedious to do routine maintenance like updating your operating system and applications. Here's a cybersecurity insight:
Security and convenience interfere with each other.
That is, to make one go up you usually have to make the other go down. The goal of security is to make things impossible (or at least really difficult) for the bad guys. However, there is often some "collateral damage". Security improvements can inconvenience the good guys. But...
Good news: you can automate your updates!
On Windows, go to:
Start >
Settings >
Update & Security
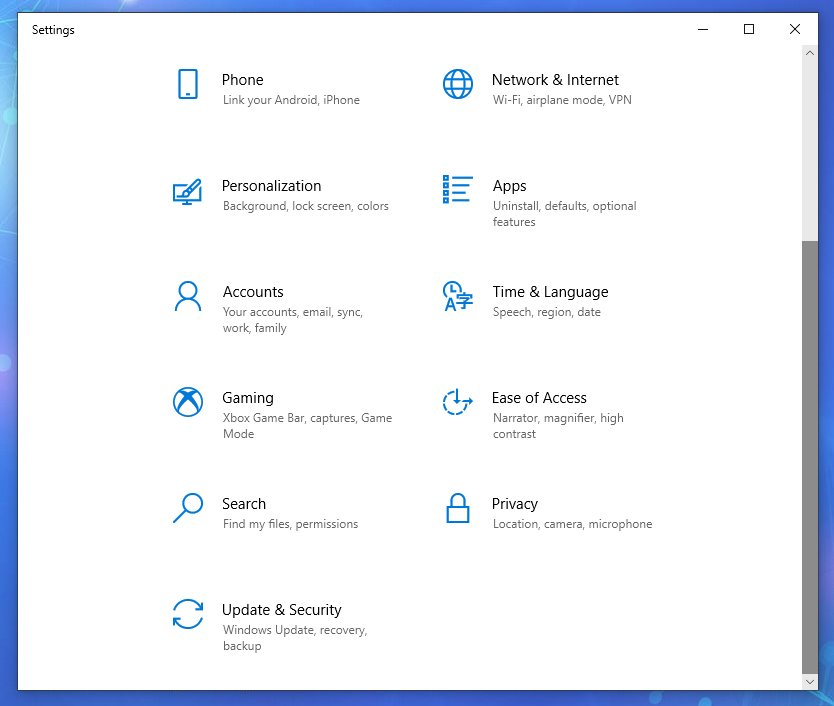
Click Start > Settings > Windows Update
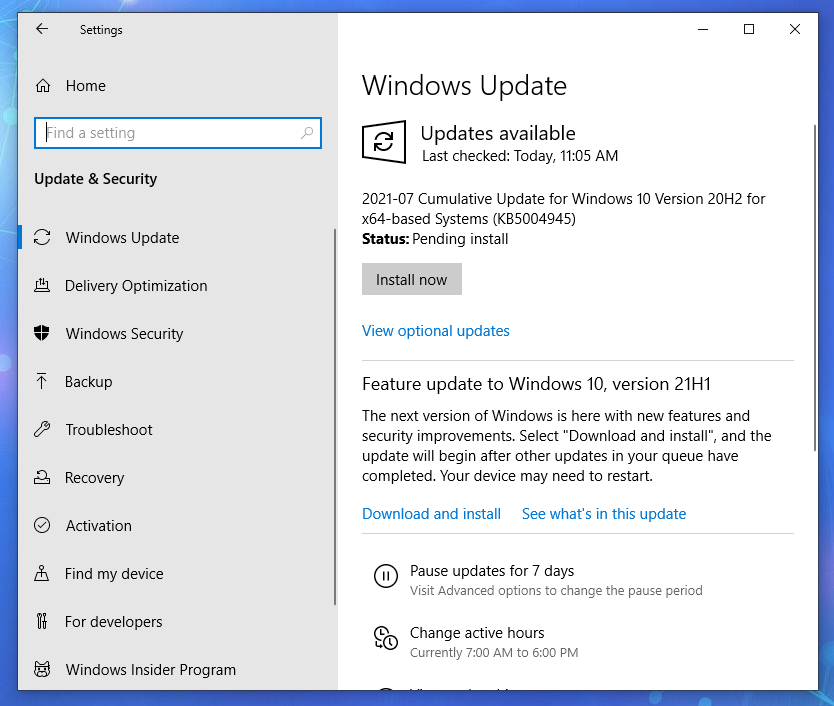
Within Windows Update you can install available updates, ask for further optional updates, and control automatic updating.
In Windows 7 this was more complicated. I think it was a good idea to simplify updates, to get people to install them more quickly.
I showed Windows updates first, but of course other operating systems have similar tools. Here is the Update Manager running on a Linux Mint desktop. It is going to update operating system components, user programs, and the third-party Chromium browser as soon as I click on the Install Updates button in the first picture below.
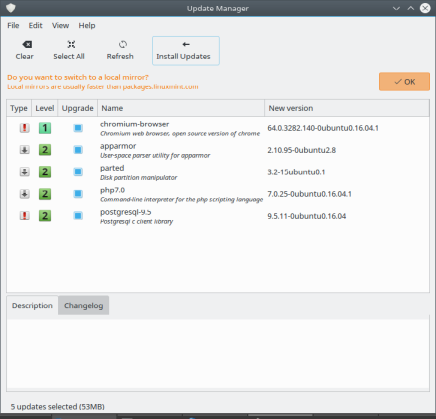
The Update Manager, actually the mintupdate
program, on the Mint distribution of Linux.
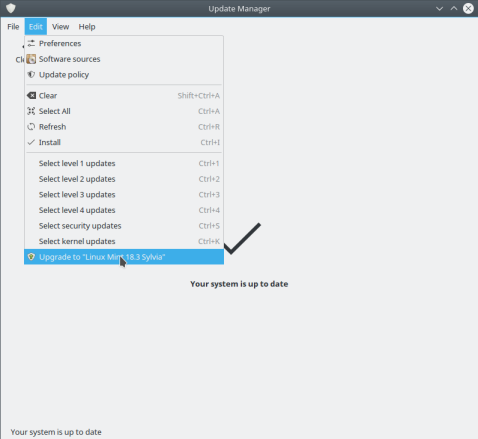
The Update Manager program upgrading to a new release of the Mint distribution of Linux.
You can even use the Update Manager to upgrade your system to newer versions of the distribution. Just click the Edit menu and see if an upgrade is available, as shown in the last picture above.
Updatinga Router
Make sure to register the router you use to connect to your ISP. Yes, then the vendor will send you email every week or two suggesting that you buy more equipment from them. But the important thing is that they will tell you when a firmware update is available.
Keep your router up to date! Install firmware updates!
In the first Screenshot below, the status page of my router, it is showing me that a firmware update is available.
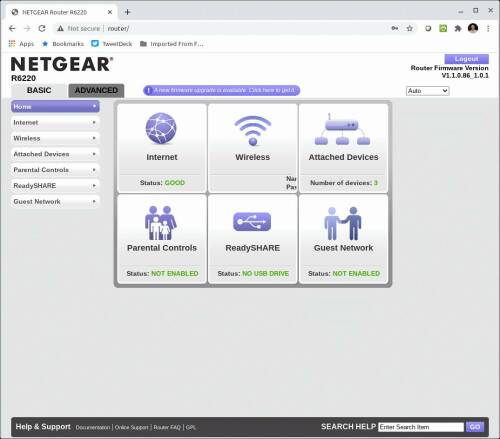

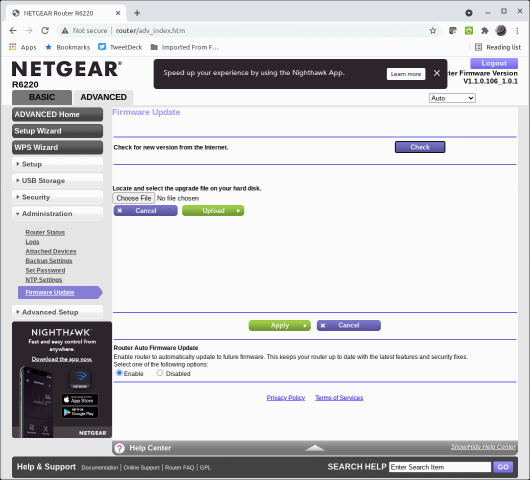
In the last screenshot above, I have gone to the Advanced tab and then selected Firmware Update and enabled automatic updates.
Never use these "online scanner" tools!
Shady operators like the "SafetyDetectives" site openly run scams. You load their page, there's a pause, and then it claims that it has detected dozens of vulnerabilities. Here's their "result" on a fully patched Linux system:
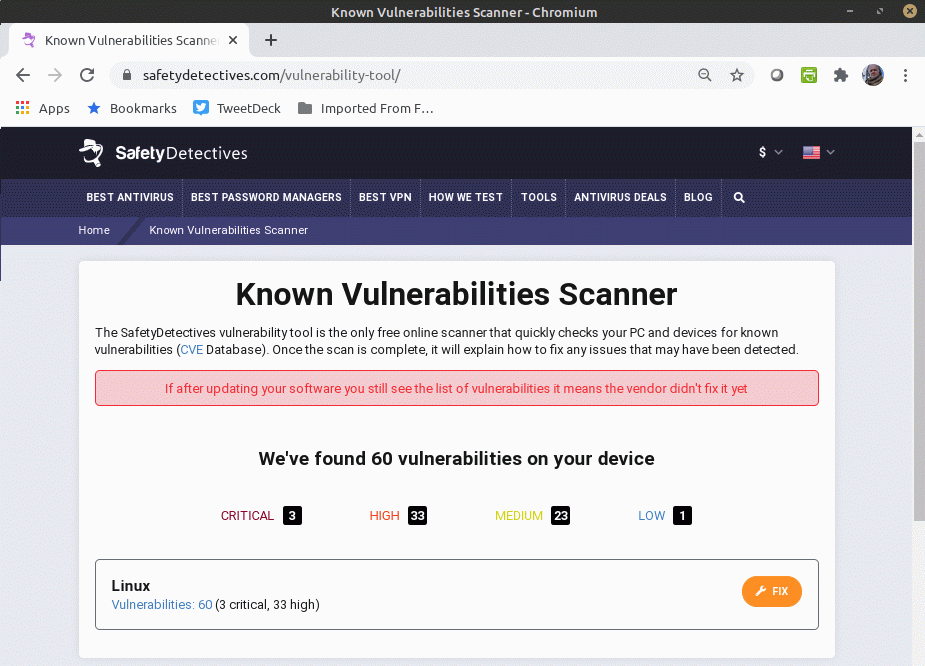
The claim of 60 vulnerabilities is a lie. So is the claim further down the page that their tool has analyzed my system's patching and configuration. They just make these things up.
On Linux, the orange "Fix" button just takes you to a
Google search for: upgrade linux
On Windows I expect it to install malware.
Never use these scam sites!
Updating will eventually mean moving to a newer operating system, which may require you to buy new hardware.
See how insecure IE 6 on Windows XP would beThis is an annoyance, but it's necessary. Older systems simply don't have what we now realize are required security features. It's like how cars didn't have seatbelts even as an optional add-on until the late 1940s into the mid 1950s.
Don't try to be safe on the Internet using outdated systems.
Simple Protection for Smart Phones and Tablets
Set up a strong PIN for identifying yourself when
you talk to your provider.
There is a form of attack where the criminals
transfer your phone to a different provider.
That's the first step in taking over your number,
so they can convince your bank that they are you.
The attack is called a "port-out" scam or "SIM swapping".
Contact your provider and say you want to
increase the security on your account.
Here are specific carriers' advice for protection.
Some, like Sprint, don't have much
useful information on-line:
AT&T
T-Mobile
Verizon
Sprint
Set up as long a PIN as you can, making it a random number that has nothing to do with your bank PIN or other authenticators. Use a password manager (details later) to generate and remember this for you. You shouldn't need to use it very often.
Set up a screen lock. Use a PIN, 8 digits if your phone supports it. Don't do this with a pattern you draw with your finger, that's the weakest form available! Turn this on in the Settings menu on either Android or iPhone. Also require a second method,
Face recognition sounds fantastic, but so far it's only so-so in performance. It has significant error rates, both false reject (locking you out of your own phone) and false accept (allowing access to someone else because they're "close enough").
Fingerprint recognition seems to be better, although arguments persist about the relative security of face versus fingerprint. An increasing percentage of phones include an in-screen fingerprint reader.
Protect Your Files
Patching, or applying updates, protects your computer — the operating system and programs. Now we need to protect the data, your personal files and pictures and so on.
My investigation of a "Police Scareware" or "Extortionware" attack"Crypto-locker" attacks are common. Some take the form of "scareware" or "extortionware". Generally speaking, the exploit goes like this:
The user wanders into a a bad corner of the Internet using an unpatched browser. Remember how I told you to update everything earlier?
They were enticed to look at the page through some clickbait about a funny video, or something amazing or outrageous or tempting, or, quite often, promises of porn. The malicious page may have actually contained a funny video, or a cute animal, or an embarrassed cheerleader, or naked people, but it also included some malware that took over their unpatched browser or video player.
The malware then encrypts or deletes all their data.
There goes every picture and every video and every file they have. All of their work. Every priceless picture and video and message from loved ones.
All they have left is a message in somewhat broken English claiming that if they pay from a few hundred to a few thousand dollars to some account in far eastern Europe, they may be able to get their pictures and videos and messages and work back again. The "scareware" or "extortionware" version adds the twist of claiming that national law enforcement has "seized" the computer for illegal activity.
If they simply had made backups, this would only be a minor annoyance.
And if they had kept their system up to date, it shouldn't have happened at all.
In Case of Emergency
No More Ransom Ransomware Prevention AdviceIf you do get hit with ransomware, there may be a simple fix. Free ransomware decryptors are available.
The No More Ransom website is an intiative by the National High Tech Crime Unit of the Netherlands' police, Europol's European Cybercrime Centre, Kaspersky, and MacAfee. In its 5th year of operation it had 121 tools that handle 151 varieties of ransomware.
Don't casually rely on these tools, assuming that they will fix any problem. But be aware of them just in case.
Protect Your Backup
The critical detail here is to keep your backups off-line. Don't leave it on an external disk connected to your PC. The crypto-locker malware immediately encrypts or deletes everything that it can find.
Copy your valuable data onto an external disk, and store that disk in a fireproof box.
How often should you do this? Do it once a year if you figure you can stand to lose the past year's data. Do it more often to further limit loss.
Be careful: Make sure that you haven't been hit by a crypto-locker before making a backup copy, as that will just be a version you can't use. If you have been hit by a crypto-locker, you need to recover data from your previous backup. Yes, this happens to people. Update your systems, and enable antivirus software. And try to resist that clickbait.
I keep duplicate copies of important data (pictures, work documents) on my desktop and laptop. When I get back from a trip, maybe to the coffeeshop, or maybe to another state or another country, I copy all the new files from my laptop to my desktop. Then I copy everything to an external disk every 6 to 12 months.
It's easy and cheap to use an external disk and a fireproof box.
Cloud CtorageThere are a lot of cloud storage services for backup. These are more complicated, really beyond the scope of this page.
Don't rely on free cloud storage offered by your Internet service provider. That might work out just fine. But, there are many examples of companies that offered free or extremely cheap online storage, and then took it away with very little notice.
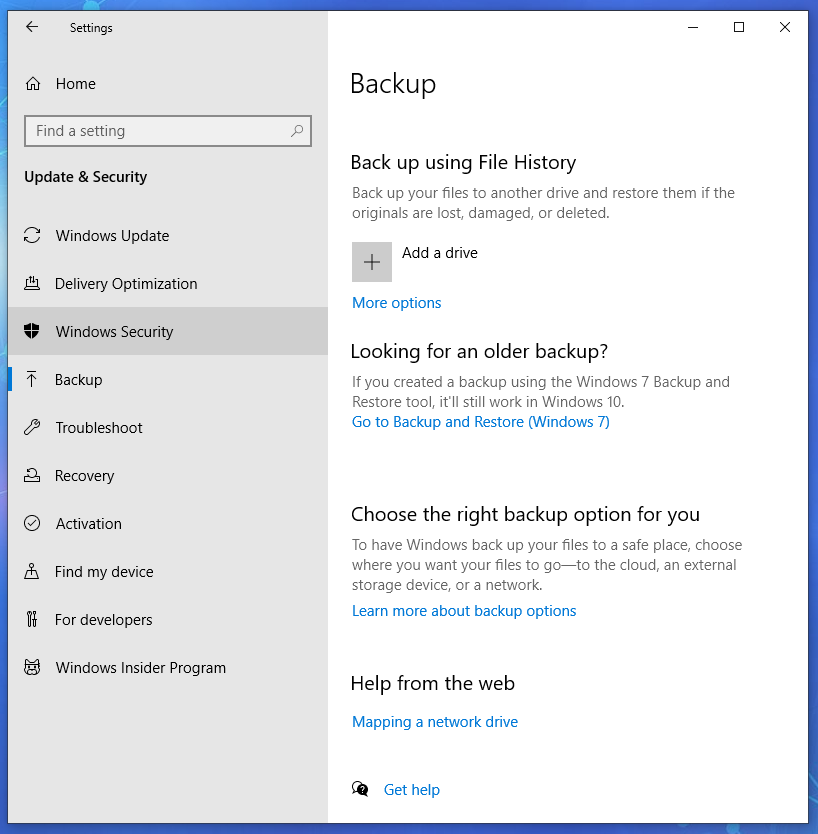
Also notice that Windows has an easy interface for backing up data:
Maintain Good Passwords
So now your software is up to date and your data is backed up. Now we have to deal with passwords.
Passwords Passwordcracking
As I said, I work in cybersecurity. If you really want to know how passwords are stored and analyzed, or even how to crack passwords, I have plenty of details on other pages.
But our goal here is "just enough" for the typical user to be safer on the Internet. What do you really need to know? It's time for another cybersecurity insight:
If one human can think up and remember a password, another human can guess it.
This is especially so when the attacker uses ever-growing dictionaries along with password-cracking programs that have been tuned and improved since the late 1980s.
So, the solution is to use highly random passwords that no person could possibly remember, and use a different password for every account.
This sounds hard but it's easy: Use a password manager. Have it generate arbitrarily long and random password strings. Copy and paste those crazy strings into graphical and command-line password interfaces.
You don't have to type the long and complex passwords. Just copy and paste! You don't even see what they contain unless you ask the password manager to show them to you.
I use
KeePass.
It works on Linux, macOS, Windows, BSD, Android, and Apple iOS,
and you can copy its encrypted database from one platform
to another to keep all your devices in sync.
And, it's completely free:
KeePass
Alternatives include:
Free:
LastPass
Encryptr
Mitto
Pasaffe
Password Safe
Built into the graphical desktop environment —
included with the operating system:
Keychain (macOS)
KWallet (Linux, BSD)
Seahorse (Linux, BSD)
Revelation (Linux, BSD)
"Freemium" — free for limited
functionality, pay for all features:
Dashlane
Enpass
Intuitive Password
Keeper
Proprietary — you must pay:
1Password
mSecure
SafeWallet
These tools store everything in an encrypted database, and so you have to enter a master password to decrypt and access the database (more on this below). That way, if you lose or someone steals your smart phone or tablet or laptop, no one has access to your password and PIN database.
Here's what KeePass looks like on a computer. There's a much simpler view on a smart phone.
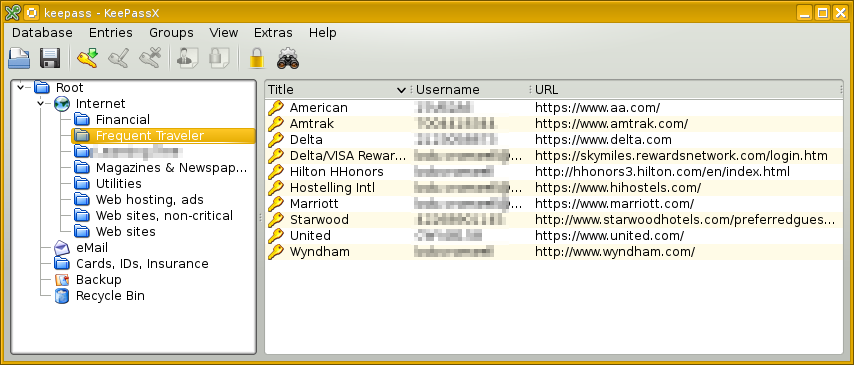
I can create new categories and sub-categories. I can move entries to other locations with simple drag and drop.
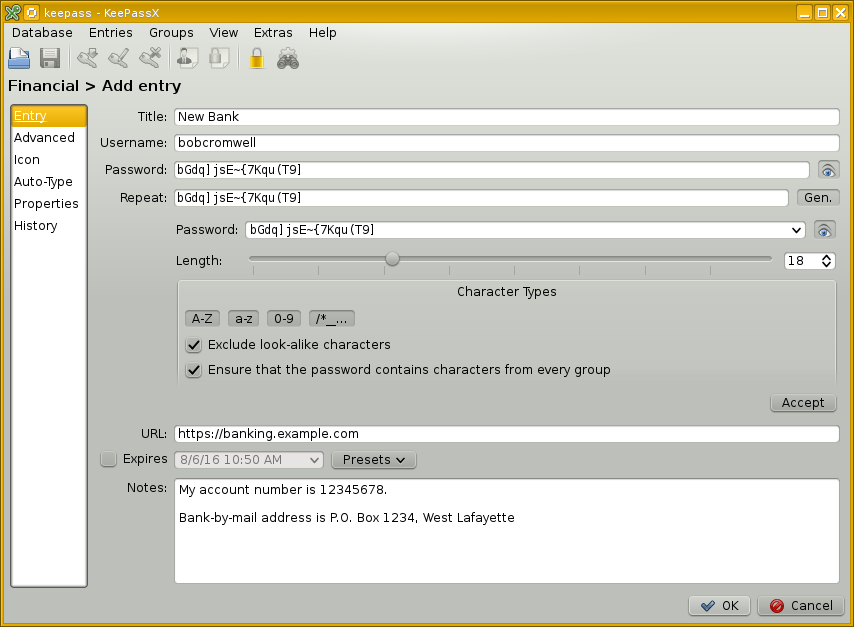
For the below example I went into the Financial area and created a new entry. I asked it to generate a random password. I can make that longer and shorter, and I can select the character classes it uses. Normally the password contents are hidden, I have clicked on the "eye" buttons to show what it has done.
You can also make entries that exist just for their "Notes" areas. I have an entry named "Credit Cards". Its "Notes" block contains the number, expiration date, CVV number, PIN, and 24-hour customer service telephone number for each of my cards. The "Username" and "Password" fields are empty, the data is all down in the "Notes" field.
As for website passwords, both Chrome and Firefox include password managers. You can ask your web browser to remember your passwords for sites. If you do that, set a master password. Unless, of course, it's on a computer you never take out of your house, and you trust everyone in the house.
Nothing is perfect
A password manager doesn't eliminate the security risk, it changes it.
Now you must enter one master password to access the collection of stored passwords. That master password must be adequately strong.
What does "adequately strong" mean? Well, that depends!
In order to try to guess your master password for either a password manager like KeePass or your browser, the attacker must have physical access to your computer, or be able to run hostile programs on it.
If you're careful about "malware" or malicious software, as I'll explain later, all we need to worry about is the physical access, and so...
Especially if you are trying to protect your privacy and/or personal identity from a potentially jealous or suspicious spouse or lover, or from dangerously curious children or siblings or parents or roommates, or any other threat with access to your devices, realize that the master password for your password manager or browser is truly the master key to everything.
My advice for do-it-yourself password design
Let's say you share a home with nosy people. You need a strong master password, one that you can remember but someone else can't guess even with high-speed password cracking software.
Think of a sentence. You have to remember this sentence, but no one else should be able to guess it. So do not use your personal slogan or a quote from your favorite movie or TV show or music or literature or scripture or anything that someone who knows you or knows about you would ever guess. Good luck with that.
Convert each word of the sentence to a character (or a few). Make some of them digits, or punctuation marks, or just drop the vowels. You can easily generate and remember a very long and complicated passsword. Something like this:
Sentence: This should not be too difficult.
Password: Tsnb2d.
Beware: password-cracking software tries combinations of two or three words with the vowels dropped, so don't rely entirely on that.
Replace some letters with "look-alike" characters: "3" instead of "E", "5" instead of "s", "!" instead of "i", "6" instead of "b", and so on.
Replace some words with "sound-alike" characters: "2" instead of "to" or "two" or "too", "@" instead of "at", and so on.
Replace other words with "means-the-same" characters: "=" instead of "is", "(" instead of "open", ")" instead of "close", and so on. If "^" can mean "up", then "v" can mean "down".
Make a game of concealing a phrase or sentence you can easily remember. How clever can you be? Maybe something like this:
Sentence: "Up, up, and away!"
Password: ^^&away!
More cautious:
Sentence: Superman says, "Up, up, and away!"
Password: SMs,^^&away!
Or, more extreme:
Sentence: Fools to the left, fools to the right,
stuck in the middle with you.
Password: F2t<,f2t>,sNtmw/U.
Be careful with this. You can easily devise and remember a sequence that you can't type accurately when you can't see what you're typing.
Don't lock yourself out!
If you forget your password or delete your only copy of the database, you lose access to everything.
Keep a backup copy of the password database. I keep copies of my KeePass file on my main desktop computer at home, and on my laptop, and on my smart phone. That way I don't have to go find the other device or wait until I get home to access sensitive data. And, if one device is damaged or lost or stolen, I still have all my passwords.
Record your master password somewhere. Or, if you're thinking up individual passwords yourself record all of them somewhere. (but why not use a password manager?) Depending on your situation, it might make sense to record your personal master password at your workplace. Or, on a slip of paper you keep with your cash.
A student in a class I once taught worked at the CIA. They were instructed to keep one-time password lists for Agency systems with their cash. Nothing is perfect, but you tend to be most careful with your personal cash, so your wallet or purse is probably the least dangerous place to keep something.
Separate your identities
Now that you have a tool that can generate and maintain highly complex passwords, take advantage of it. Use a different password on every site. "Compartmentalize your identities", to use the fancy terminology.
Or at least for the sites that matter.
Sure, if the local newspaper requires that you "register an
account" with your email address and a password just to see
the local weather forecast, use "password"
as your silly password on that silly site.
But if a site has any security or identity issues or sensitivity, use your password manager to generate and remember a complex password for it.
Be especially careful with your primary email identity. We have, perhaps unintentionally, perhaps without realizing it, drifted into a situation where your primary email address is the key to all your identities. It's the "recovery address" for your bank accounts, your health insurance, your utility payments, and much more.
Should I change my passwords every 90 days? 60? 30?
Don't bother changing your passwords every so often.
I have much more detail here and here. The short version: In the early 1970s, some U.S. Department of Defense contractors did some back-of-the-envelope calculations based on speculation about Soviet computing technology of the era. They figured that monthly changes would be helpful. Their wild guess became fossilized as U.S. government policies.
Policy is slowly becoming more reasonable.
The Chief Technologist for the U.S. Federal Trade Commission recently wrote about how mandatory password changes are harmful. I have links to more background here. Studies have shown that policies that enforce password change lead to weaker passwords.
Meanwhile, the author of the U.S. government policy dictating password complexity requirements has now retired. He has admitted that he wrote that guidance without knowing much about information security or how passwords work. See the articles in Wall Street Journal and Gizmodo.
So:
- Use a password manager.
- Use it to generate your passwords, each one a long jumble of all character types.
- Have a unique password, a different complex jumble, for every account.
- Copy-and-paste them into place, good ones are hard to type accurately.
- Generate and remember a strong master password with my sentence trick above.
- Change a password when you have to.
- Definitely change a password if you suspect that their site may have been breached.
Never Sign In On Shared Computers
Never use a computer you do not own to sign in to any account, especially computers in hotel lobbies or other public settings.
Seriously. Just don't.
Using the earlier advice about password managers, you should have your many accounts compartmentalized, each with its own unique and complex password. But you don't want to give away bits and pieces of your collection of accounts, even the "less important" ones.
Shared computers are frequently infected with key-logging software that collects all accounts and passwords and sends them to criminal gangs.
Sure, use the hotel's computer. Check the weather forecast. Print out Google maps or Wikipedia explanations of what you're going to see in your day's explorations from the hotel. Just don't ever sign in to any account from a shared PC in the hotel lobby.
See the safe Road Warrior section later for how to safely sign in when you're away from home.
Email and Browse Safely
So your software is up to date, your passwords are impractical for anyone to guess, and you have unique passwords for every account that you easily access with a password manager. Now you're ready to get on the Internet!
Email tools
This isn't nearly as important as other items on this list, but it sure seems to me that a standalone mail program has multiple security advantages over web mail, which is to say viewing your mail in a web browser.
Personally, I prefer Thunderbird for reasons of both security and ease of use. Alternatives include SeaMonkey and Mailbird.
Yes, there is Microsoft Outlook, but its history of security and intercompatibility problems makes me very leery. I suppose standalone email with Outlook is a little better than web mail with Explorer, but you can do better than either.
Email format
It is safer to view email in plain text mode. There are exploits that only work when you view email as HTML.
The problem, however, is that many organizations simply do not send messages that you can make any sense of without HTML viewing turned on. For example, airline and hotel loyalty programs. Sure, most of their messages are attempts to sign you up for American Express credit cards. But once in a while there's actually something important in there. Depending on how you use email, plaintext message viewing may be impractical.
Learn to be safely skeptical
If it's "Too good to be true", then it isn't true.
Take this "Phishing IQ Test".
They show you a series of email messages and ask you to
select "Legitimate" or "Phishing" (that is, a scam)
for each.
Then the best part is that they explain the
tell-tale warning signs for every example.
SonicWALL Phishing IQ Test
Take the "Banks Never Ask That!" quiz:
Banks Never Ask That!
Also see the overview from PayPal and the additional
quiz from the Washington Post.
PayPal: Recognize fraudulent emails and websites
Washington Post phishing quiz
Safe browsing
Of course, keep your browser up to date! As I mentioned earlier, your browser updates may be separate from the operating system itself. So, set up automatic updates on your browser.
Understand what your browser window is showing you
Learn how to make sense of the URL, that Internet address
in the box near the top of the browser window
specifying the page you're looking at.
Also pay attention to the URLs you see at the bottom
when you hover over a link.
Hover your mouse over that green "Updating Google Chrome"
button above.
You should see at the bottom of your browser that clicking
there would take you to a page at a server named
support.google.com, which is a part of
google.com, which is the company that runs
the Google search engine and
maintains the Chrome browser.
So, a click there should take you to a trustworthy source
of information on updating that browser.
Look at the URL at the top of this browser window.
This page is either:
https://cromwell-intl.com/cybersecurity/basics/06-safe-email-and-web.html
or, if you're looking at the all-in-one version:
https://cromwell-intl.com/cybersecurity/basics/all.html
The first part
is the protocol.
It's https
for this page, meaning two forms of security.
The server is authenticated, meaning that you can
be certain you're really getting the page from
that specific server.
Also, the connection is encrypted, meaning
that if you're on an insecure network at a hotel, someone
could capture the traffic but they would see nothing but
encrypted gibberish.
If it were plain old http
then you wouldn't really know which server you had
connected to, and all communication would be plaintext,
or unencrypted.
The second part
is the server.
It's cromwell-intl.com
for this page.
That probably doesn't mean anything in particular to you,
and that's fine for a page you are reading simply for
information or entertainment.
But if a page looked like the login screen for your bank,
and the server name had nothing to do with your bank,
that would be a very bad sign!
The third part
is the specific resource from that site.
It's either
/cybersecurity/basics/06-safe-email-and-web.html
or
/cybersecurity/basics/all.html
for this page.
That part might be helpful to figure out how the site is
organized or what this page is related to.
I have organized my site with
cybersecurity pages under /cybersecurity/,
Linux and related pages under /open-source/,
travel pages under /travel/,
and so on, but that's just organization
and it doesn't have anything to do with security.
Be careful about clicking on links on pages you don't have reason to trust, and especially in email from people you don't know.
If a web site prompts you to install a viewer to watch a video, or view a slideshow, or listen to something, STOP and do not install anything as this is a scam.
Completely clean up after banking
When you finish your session of on-line banking (or any similarly sensitive activity), click the "Logout" button and also terminate all your browser tabs and windows. Don't just minimize the window, click the "X" in the upper right corner of every browser window and fully end that browser session.
This is one of these inconveniences we unfortunately need in order to be safe on line. Remember that trade-off?
Don't install Flash
This is about the Flash video standard and
the Adobe software for viewing it.
Flash RAM memory as found in USB thumb drives
is entirely different.
Adobe, the company that developed it, has given up on the Flash video format.
It seemed important in the early 2000s. But starting about 2007, video for the web started moving away from Flash format
Much of what you now see about "You must install Flash to view this content" is actually an attempt to trick you into installing malware instead.
Beware of Browser Extensions and Add-Ons
It is far too easy to unintentionally install some extension or add-on that takes advantage of you. These may replace your home page, or force all searches to be done through their interface. Fix this:
Chrome:
3-dot menu → Extensions → Manage Extensions
Firefox:
3-linemenu → Add-ons → Extensions
Also click Plugins to see what's listed.
It's a good idea to check these once in a while, just in case.
Be Careful On Social Media
Everything you post on social media sites is now out of your control and it belongs to the social media companies.
Oh, you might be able to delete it or change it some of the time. But generally speaking, all of your postings belong to the social media company, who is free to sell it or repost it or do whatever they want with your data.
It gets worse.
The more you post on Facebook and other social media sites, the easier you make it for criminal gangs to steal your identity. Most Facebook users share information that makes it easy to answer the "security questions" used on many websites. Criminal gangs download and analyze Facebook content to figure out who knows who and what interests they share. They then use that to generate convincing scam emails.

Many people seem to use Facebook and other social media
for nothing but forwarding hoaxes.
Use Snopes
and
Politifact
and
OpenSecrets
and
FactCheck.org
and
Climate Feedback
to find the truth.
There are also
Bad Satire Today
and
Hoax-Slayer
Snopes.com
Politifact.com
OpenSecrets
FactCheck.org
Climate Feedback
When you give Facebook access to your contact list,
they sell it to marketing companies.
Then the "People you may know" suggestions can
expose sensitive information including:
Medical and psychiatric history
Family secrets
Other sensitive information
What About Deleting Your Facebook Account?
That seems like a good idea.
I did it.
Here's how:
How to Delete Your Facebook, Twitter, Instagram,
and TikTok
How to Delete Your Facebook Account
Facebook's Explanation
You might want to remove your listings from "aggregators", web sites that provide search interfaces for their collections of data scraped from many public sources. See my physical security page for some details.
Avoid Viruses, Spyware, and Other Malware
Make sure that any anti-virus software is enabled, and that it is constantly updated.
You Don't Need to Buy Antivirus SoftwareThe Windows operating system itself now includes Windows Defender, leave it have turned on. At that point most personal users are fine and you don't need to buy antivirus software for your personal systems. That sounds like heresy, but read this article for the details on how Windows Defender is adequate, and added antivirus software is at best an unnecessary expense, and at worst it can make security worse. If you want to add something, the free version of Malwarebytes is probably your best choice.
Other good free anti-virus / anti-malware software
includes the following.
ZoneAlarm incorporates spyware detection and
removal software.
Avira
AVG
ZoneAlarm
ClamAV
ClamXav
I used to recommend Avast!, but then it was fined US$ 16.5 million for selling users' browsing data.
As for non-free products, I have been very impressed with Kaspersky products. My mobile phone runs Android, and I have been happy with the free entry-level Kaspersky tool for Android. I would use Kaspersky anti-malware software on my other computers if they ran Windows. I use Linux almost exclusively, rendering this moot for myself.
KasperskyRescue Disk
The Kaspersky Rescue Disk lets you safely boot and clean infected Windows systems that can't be cleaned with the normal tools.
Yes, sure, if you're an NSA employee who very inappropriately takes home NSA offensive software, and you install that on your Windows PC, on which you had also installed Kaspersky software, then bad things might happen. But that went wrong in several ways at once that were not Kaspersky's doing. See New York Times and Washington Post stories for details.
Don't Fall for Scams
Popup messages warning you about malware are scams.
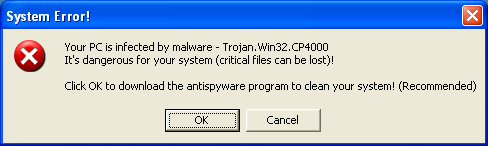
This popup is a scam trying to infect your computer and steal your credit card number. Ignore this bogus "warning"!
Do not click to "download antispyware", do not click to "update Windows antivirus", do not call the phone number.
These are just as bogus as the phone calls claiming to be from Microsoft or your ISP. They want you to install spyware or give them your credit card number.
Hang up on those phone calls. Ignore these popups.
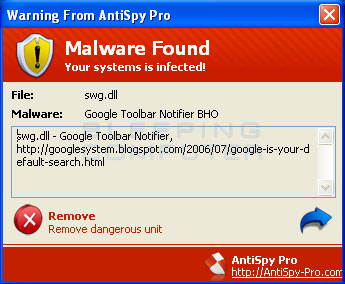
This popup is yet another scam trying to infect your computer and steal your credit card number. Ignore this!
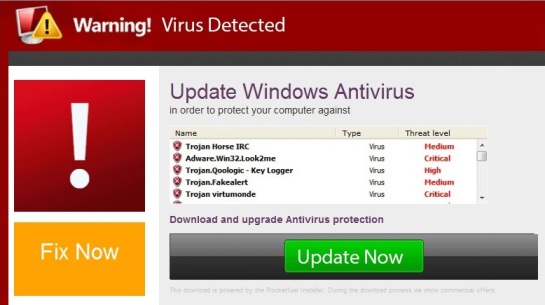
This popup is also a scam trying to infect your computer and steal your credit card number. Ignore this scam!
How can you clean up?
Close all your browser windows. Make sure to close all of them, it may have also opened a small window that "popped under" an existing window so you don't notice it.
Once in a while it will be worse, it will keep re-opening a new window. Browsers shouldn't do that any more, see the earlier page about updating your software.
If you can't kill off the browser process, on Linux or other UNIX-family operating systems, run whichever of these commands corresponds to the misbehaving browser:
$ pkill chrome $ pkill chromium $ pkill firefox
On Windows, right-click on the task bar, start the
Task Manager, and find and terminate the browser processes.
Beware: iexplorer.exe is a browser,
while explorer.exe is the desktop itself.
Why do these popups appear?
You have looked at a hostile page with your browser. How did that happen?
Maybe you simply wandered into the hostile page.
For quite a long time, the forbes.com site
for Forbes magazine was hosting ads
with hostile content.
I'm not sure, it still may be.
Look at the Forbes website, and you might
be bothered with popup scams.
Maybe the site was hacked, its content replaced with something that tries to trick people with popups
You may have clicked on a link in an email that you thought came from a friend. Many Facebook users connect their entire "Contacts" database to Facebook. Even if you don't use Facebook, someone who knows you may have done this. Attackers "scrape" sites like Facebook to build databases of email addresses and connections between people.
I know someone who apparently only uses Facebook, he doesn't seem to use email. I haven't received an actual email from him for a number of years now. But at least once a week on average, I get an email that appears to be from him.
The "From" field has his name. As for the source address, sometimes it has the username of his actual email account with a number added to the end. Sometimes it's something randomly different. Then it's at some random domain. Here's a screenshot of the list in my Trash folder:
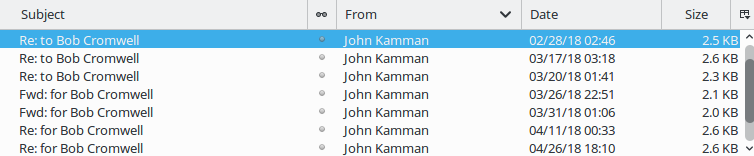
Looking at those messages, the "From" fields are:
John Kamman <john.kamman313@song.ocn.ne.jp>
John Kamman <john.kamman68@grace.ocn.ne.jp>
John Kamman <info@floridaforextrading.com>
John Kamman <dhoit@waynetownship.net>
John Kamman <tjaros@iyvaa.com>
John Kamman <john.kamman205@song.ocn.ne.jp>
John Kamman <john.kamman465@coffee.ocn.ne.jp>
The Subject is either "Re: to" or "Fwd: for", then my name.
The body is simple text, something like:
when you have a few minutes you my want to have a look at this
or:
I hope all is well. Just thought you may want to have a look at this
or:
Hope you're having a great day. I thought you might appreciate this
or:
When you have a minute or two you may want to have a look at this
or:
I thought you would appreciate it
or:
Just wanted to share what I ran into the other day. You would probably want to have a look
or:
When I found this page the other day I though of you. So I decided to share it with you
That is then followed by a URL. Looking at the headers, these messages are sent from IP addresses that have nothing to do with me, the purported sender, or the claimed "From" email address.
Be a Cautious "Road Warrior"
First, as mentioned earlier, never sign in to any account on a shared computer in a hotel lobby.
Second, realize that hotel networks, wireless or wired, are entirely insecure. Yes, there is an illusion of security as you have to enter a password or PIN for the router to forward your packets.
But this is just a "captive portal" system. It makes the hotel's liability lawyers happy and it increases revenue if you have to pay for the access. There is absolutely no security for the user in a hotel network. Anyone else in the hotel could be capturing all your data, including passwords and data content.
Only use a hotel network for entirely non-critical traffic (browsing random websites) or for communication encrypted end-to-end through a carefully configured TLS connection or SSH, or through a corporate VPN (that is, a Virtual Private Network).
Travel provides more chances of losing your electronic devices. See the next section for how to encrypt data stored on phones, tablets, and laptops.
A mobile hotspot may be worthwhile. Yes, mobile phone networks can be hacked, but they're far safer than hotel networks.
Advanced topic: see how a $25 per night hostel has far better network security than a business hotel costing at least ten times as much.
Even more advanced topic: you could carry an entire virtualized computer on a USB stick.
Clean and Optimize Your Windows Computers
This is very simple. Follow the excellent advice found here.
That's on the great Decent Security site.
Consider Encrypting Smart Phones and Tablets
Consider encrypting the storage on phones and tablets. I don't, because I don't use my phone for email and I don't store any sensitive data on it. Yes, I use the KeePass password manager, but remember that it stores its database in encrypted form.
But if you store any sensitive data on your phone, and this might include pictures (and please don't tell me the details of your pictures you don't want anyone to see), you should encrypt the phone's storage.
Be careful about installing apps. Especially on Android where there is less checking, but people have sneaked in malicious iPhone app activity at times.
And, of course, install all updates for your phone's operating system and your apps.
Maybe Encrypt Your Laptop
Finally, consider your threat environment. What do you store on your laptop? (Don't forget about email messages) And how likely is it that someone will steal your laptop, or otherwise try to access data stored on it?
You might want to encrypt your laptop's disk. However, this makes periodic backup of the plaintext version much more important.
Microsoft has BitLocker, MacOs has FileVault, and Linux supports a variety of disk encryption systems.
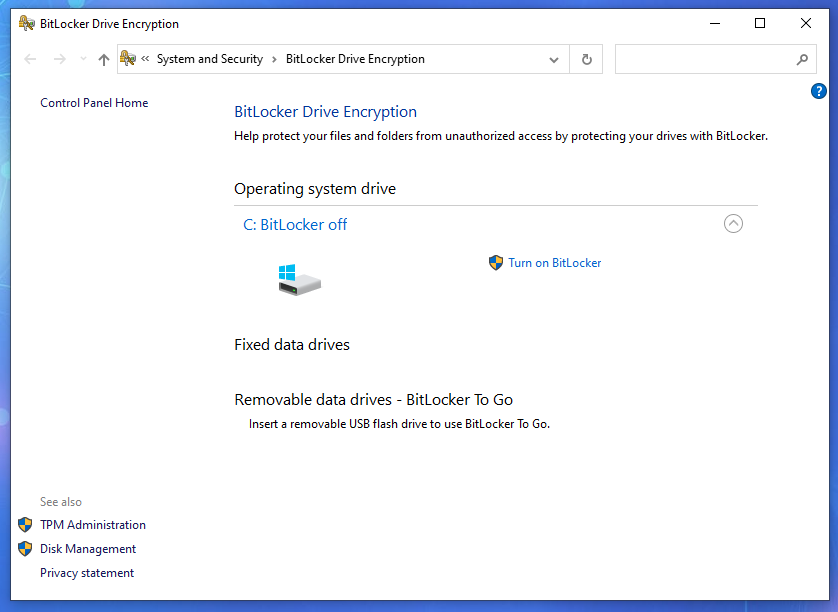
Notice the BitLocker choice.
Encrypting External Media
Many USB memory sticks and some high-capacity external disks now include encryption software.
The software they include is generally Windows-only. On Windows you may not be able to avoid using it. That's good for very high-security settings, but it's an annoyance at best for the typical home user. On Linux or other operating systems, it's a distraction. A second storage device appears, but you can't use it.
Some of these devices are marketed with silly "Military-Grade" claims that don't really mean anything.
Encryption Can Lead to Loss
Information security professionals talk about CIA, standing for Confidentiality, Integrity, and Availability. The more obvious terms for non-specialists are Secrecy, Accuracy, and Reliability, but those doesn't make for a catchy acronym. And now we reach the last insight for this series of pages:
Confidentiality and availability conflict with each other. The harder you try to keep secrets, the greater your chances of losing access to your own information. And the more backup copies you store in the interest of availability (or reliability), the more likely one of them will get out.
It's another one of those trade-offs. If one is to go up or get better, the other must go down or get worse. Let's say you encrypt your backup copies of your files, or you simply make a backup copy of the entire encrypted disk. You could easily forget or lose the key by the time you finally need to recover and decrypt the data.
The Integrity part can also cause trouble when you're decrypting data. A single bit error within an encrypted file will corrupt the entire result of trying to decrypt it.
Think about the secrets you are trying to maintain. If no one else should ever know it, and if you don't really need it, then don't keep it. Many corporate and government problems are caused by trying and failing to protect sensitive information that shouldn't have been collected in the first place.
Do You Want To Learn More About Information Security?
Bruce Schneier has developed several cryptographic algorithms, both ciphers and hash functions. But while he's brilliant at math and logic, he also does a very good job of explaining complex topics. He has more recently become very interested in psychological issues of how we perceive and handle risk. His monthly Crypto-Gram newsletter is a very readable review of information security news. Information security issues surround us, but we don't always recognize them as such. Bruce points them out, and makes them about as clear as they can be for the masses.
If you think you might be getting interested in the details
of computer and network security, keep reading the
Crypto-gram but also check out
Brian Krebs, Dark Reading, and the Kaspersky Lab blog.
Brian Krebs and Dark Reading should be readable by most
anyone, they have pointers to the real details.
Kaspersky's blog is a mix of overview and detailed analysis.
Krebs On Security
Dark Reading
Kaspersky Lab blog
Help Net Security
Information Week
Ars Technica,
Wired,
The Atlantic (especially some of James Fallows'
articles from when he worked in China),
and other publications include cybersecurity stories
aimed at the educated general public.
Forbes sometimes carries good articles on
information security,
but the irony is that the forbes.com site is notorious for
pushing malicious software out through ad content.
Ars Technica
Wired
The Atlantic
Forbes (patch your browser first!)
Maybe Go Further
You can set up Two-Factor Authentication. That means that it requires something you know (a password) and something you have (your phone). Several web sites now allow you to set up two-factor authentication (or 2FA) so that when you try to log in, they ask for your password and a code they send to your phone as a text message.
There are also 2FA apps for smart phones, like:
Google Authenticator
Ask your bank what two-factor authentication they support for on-line banking. If they say they aren't using any yet, that's probably OK. If they don't know what you're talking about, don't do any business with them on-line.
To go deeper into hardening Windows,
Windows Security From The Ground Up
Finally, if you want to go
even deeper into the details,
my cybersecurity web pages are largely collections of
references and links, organized by category.
Further Cybersecurity References